Two vulnerabilities impacting the POST SMTP Mailer WordPress plugin, an e-mail supply device utilized by 300,000 web sites, might assist attackers take full management of a web site authentication.
Final month, Wordfence security researchers Ulysses Saicha and Sean Murphy found two vulnerabilities within the plugin and reported them to the seller.
The primary, tracked as CVE-2023-6875, is a crucial authorization bypass flaw arising from a “kind juggling” situation on the connect-app REST endpoint. The difficulty impacts all variations of the plugin as much as 2.8.7
An unauthenticated attacker might exploit it to reset the API key and examine delicate log data, together with password reset emails.
Particularly, the attacker can exploit a perform referring to the cellular app to set a sound token with a zero worth for the authentication key by way of a request.
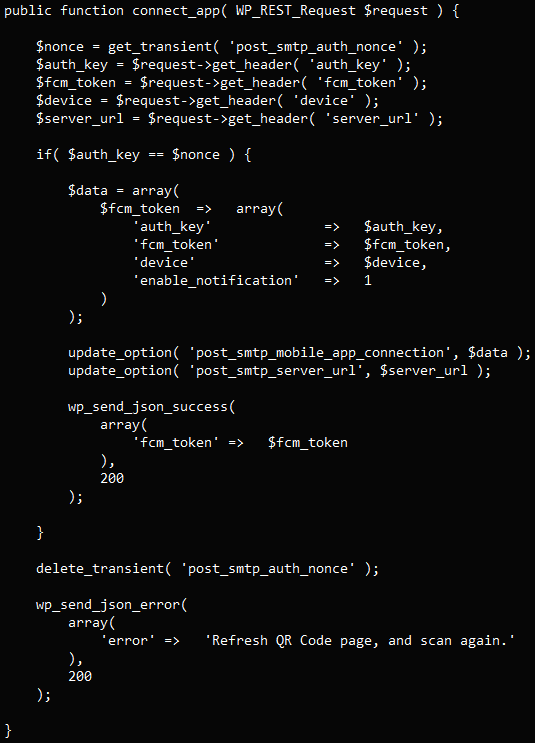
Subsequent, the attacker triggers a password reset for the positioning’s admin after which accesses the important thing from throughout the utility, altering it and locking the legit consumer out of the account.
With administrator privileges, the attacker has full entry and may plant backdoors, modify plugins and themes, edit and publish content material, or redirect customers to malicious locations.
The second vulnerability, is a cross-site scripting (XSS) downside recognized as CVE-2023-7027 that arises from inadequate enter sanitization and output escaping.
The flaw impacts POST SMPT as much as model 2.8.7 and will let attackers inject arbitrary scripts into the net pages of the affected web site.
Wordfence first contacted the seller concerning the crucial flaw on December 8, 2023, and after submitting the report they adopted up with a proof-of-concept (PoC) exploit on December 15.
The XSS situation was reported on December 19, 2023, and a PoC was shared the following day.
The plugin’s vendor printed on January 1, 2024 model 2.8.8 of POST SMPT that features security fixes for each points.
Based mostly on statitics from wordpress.org, there are roughly 150,000 websites that run a susceptible model of the plugin that’s decrease than 2.8. From the remaining half which have model 2.8 and better put in, 1000’s are seemingly susceptible as effectively when contemplating that the platform stories roughly 100,000 downloads for the reason that launch of the patch.




