Roughly 1,450 pfSense situations uncovered on-line are weak to command injection and cross-site scripting flaws that, if chained, may allow attackers to carry out distant code execution on the equipment.
pfSense is a well-liked open-source firewall and router software program that enables intensive customization and deployment flexibility. It’s a cost-effective resolution that accommodates particular wants, providing a variety of options usually present in costly business merchandise.
In mid-November, SonarSource’s researchers with the help of their SonarCloud resolution found three flaws impacting pfSense 2.7.0 and older and pfSense Plus 23.05.01 and older. The issues are tracked as CVE-2023-42325 (XSS), CVE-2023-42327 (XSS), and CVE-2023-42326 (command injection).
Though the mirrored XSS flaws require person motion on the sufferer’s aspect to work, the command injection flaw is extra extreme (CVSS rating: 8.8).
This vulnerability in pfSense’s internet UI arises from shell instructions being constructed from user-provided knowledge for configuring community interfaces with out making use of correct validation.
The flaw impacts the “gifif” community interface parameter, which isn’t checked for protected values, permitting malicious actors to inject extra instructions within the parameter, resulting in their execution with root privileges.
For this exploit to work, the risk actor wants entry to an account with interface modifying permissions, therefore the necessity to chain the issues collectively for a strong assault.
Both CVE-2023-42325 or CVE-2023-42327 can be utilized for executing malicious JavaScript in an authenticated person’s browser to achieve management over their pfSense session.
Netgate, the seller of pfSense, acquired studies concerning the three flaws on July 3, 2023, and launched security updates that addressed them on November 6 (pfSense Plus 23.09) and November 16 (pfSense CE 2.7.1).
Nonetheless, a month after patches have been made accessible by Netgate, practically 1,500 pfSense situations stay weak to assaults.
Shodan scan outcomes SonarSource’s researchers shared with BleepingComputer present that out of the 1,569 internet-exposed pfSense situations, 42 use pfSense Plus 23.09, and one other 77 run pfSense Neighborhood Version 2.7.1.
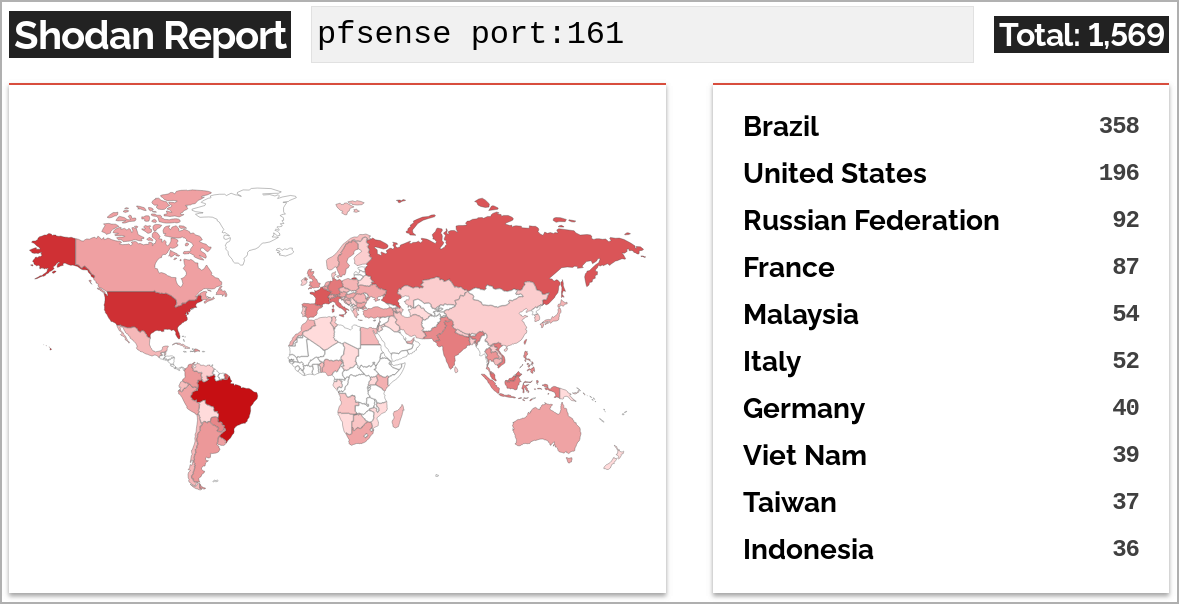
This leaves 1,450 situations (92.4%), that are immediately discoverable by means of Shodan, weak to the talked about flaws.
Whereas this publicity doesn’t make these situations prone to rapid compromise, as risk actors would first want to focus on victims with XSS flaws, the publicity creates a major assault floor.
Whereas the variety of weak endpoints represents a small fraction of pfSense deployments globally, the truth that massive enterprises typically use the software program makes this standing significantly harmful.
An attacker with entry to pfSense working with high-level privileges can simply trigger data breaches, entry delicate inside sources, and transfer laterally inside the compromised community.




