As many as 100 malicious synthetic intelligence (AI)/machine studying (ML) fashions have been found within the Hugging Face platform.
These embrace cases the place loading a pickle file results in code execution, software program provide chain security agency JFrog mentioned.
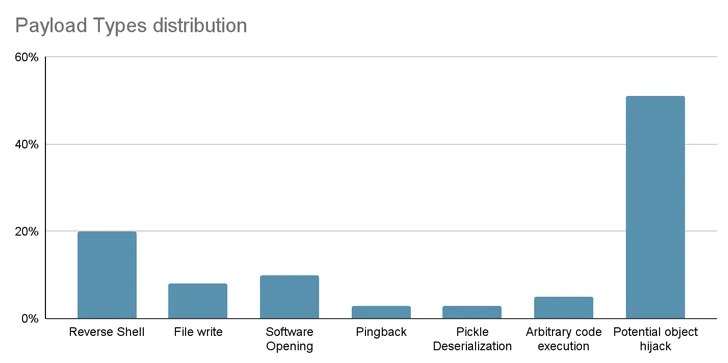
“The mannequin’s payload grants the attacker a shell on the compromised machine, enabling them to realize full management over victims’ machines by way of what is usually known as a ‘backdoor,'” senior security researcher David Cohen mentioned.
“This silent infiltration might doubtlessly grant entry to essential inner programs and pave the way in which for large-scale data breaches and even company espionage, impacting not simply particular person customers however doubtlessly complete organizations throughout the globe, all whereas leaving victims completely unaware of their compromised state.”
Particularly, the rogue mannequin initiates a reverse shell connection to 210.117.212[.]93, an IP handle that belongs to the Korea Analysis Surroundings Open Community (KREONET). Different repositories bearing the identical payload have been noticed connecting to different IP addresses.
In a single case, the authors of the mannequin urged customers to not obtain it, elevating the likelihood that the publication stands out as the work of researchers or AI practitioners.
“Nonetheless, a basic precept in security analysis is refraining from publishing actual working exploits or malicious code,” JFrog mentioned. “This precept was breached when the malicious code tried to attach again to a real IP handle.”
The findings as soon as once more underscore the risk lurking inside open-source repositories, which may very well be poisoned for nefarious actions.
From Provide Chain Dangers to Zero-click Worms
In addition they come as researchers have devised environment friendly methods to generate prompts that can be utilized to elicit dangerous responses from large-language fashions (LLMs) utilizing a method referred to as beam search-based adversarial assault (BEAST).
In a associated growth, security researchers have developed what’s often known as a generative AI worm referred to as Morris II that is able to stealing information and spreading malware by way of a number of programs.
Morris II, a twist on one of many oldest laptop worms, leverages adversarial self-replicating prompts encoded into inputs reminiscent of photographs and textual content that, when processed by GenAI fashions, can set off them to “replicate the enter as output (replication) and interact in malicious actions (payload),” security researchers Stav Cohen, Ron Bitton, and Ben Nassi mentioned.
Much more troublingly, the fashions might be weaponized to ship malicious inputs to new purposes by exploiting the connectivity inside the generative AI ecosystem.
The assault method, dubbed ComPromptMized, shares similarities with conventional approaches like buffer overflows and SQL injections owing to the truth that it embeds the code inside a question and information into areas identified to carry executable code.
ComPromptMized impacts purposes whose execution move is reliant on the output of a generative AI service in addition to people who use retrieval augmented era (RAG), which mixes textual content era fashions with an data retrieval element to counterpoint question responses.
The research will not be the primary, nor will it’s the final, to discover the thought of immediate injection as a approach to assault LLMs and trick them into performing unintended actions.
Beforehand, lecturers have demonstrated assaults that use photographs and audio recordings to inject invisible “adversarial perturbations” into multi-modal LLMs that trigger the mannequin to output attacker-chosen textual content or directions.
“The attacker might lure the sufferer to a webpage with an fascinating picture or ship an e mail with an audio clip,” Nassi, together with Eugene Bagdasaryan, Tsung-Yin Hsieh, and Vitaly Shmatikov, mentioned in a paper revealed late final yr.
“When the sufferer instantly inputs the picture or the clip into an remoted LLM and asks questions on it, the mannequin will likely be steered by attacker-injected prompts.”
Early final yr, a bunch of researchers at Germany’s CISPA Helmholtz Heart for Info Safety at Saarland College and Sequire Know-how additionally uncovered how an attacker might exploit LLM fashions by strategically injecting hidden prompts into information (i.e., oblique immediate injection) that the mannequin would seemingly retrieve when responding to consumer enter.




