Oracle lastly confirmed in e-mail notifications despatched to clients {that a} hacker stole and leaked credentials that had been stolen from what it described as “two out of date servers.”
Nevertheless, the corporate added that its Oracle Cloud servers weren’t compromised, and this incident didn’t influence buyer knowledge and cloud companies.
“Oracle wish to state unequivocally that the Oracle Cloud—also referred to as Oracle Cloud Infrastructure or OCI—has NOT skilled a security breach,” Oracle says in a buyer notification shared with BleepingComputer.
“No OCI buyer atmosphere has been penetrated. No OCI buyer knowledge has been considered or stolen. No OCI service has been interrupted or compromised in any approach,” it added in emails despatched from replies@oracle-mail.com, prompting clients to contact Oracle Help or their account supervisor if they’ve further questions.
“A hacker did entry and publish consumer names from two out of date servers that had been by no means part of OCI. The hacker didn’t expose usable passwords as a result of the passwords on these two servers had been both encrypted and/or hashed. Subsequently the hacker was not capable of entry any buyer environments or buyer knowledge.”

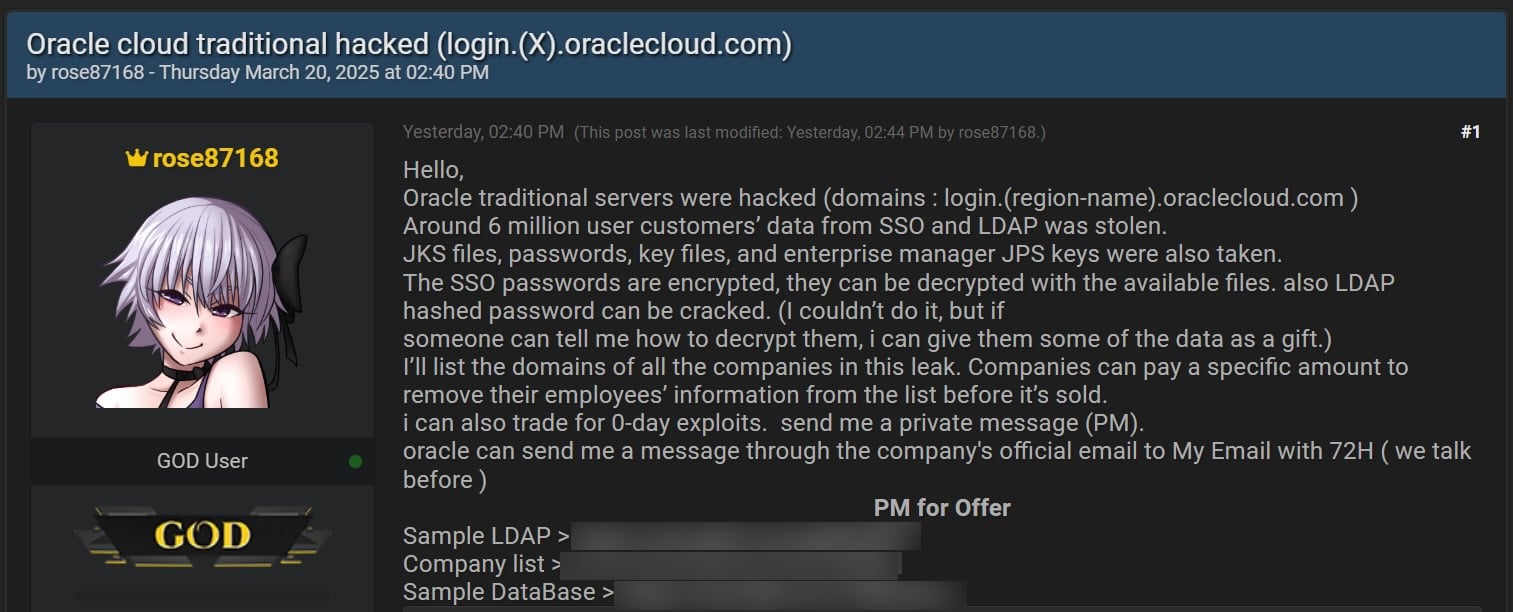
Because the incident surfaced in March, when a menace actor (rose87168) put up 6 million knowledge information on the market on BreachForums, Oracle has persistently denied experiences of an Oracle Cloud breach in statements shared with the press. Whereas that is admittedly true because it matches what Oracle is telling clients—that the breach impacted an older platform, Oracle Cloud Traditional—that is merely wordsmithing, as cybersecurity professional Kevin Beaumont stated.
“Oracle rebadged previous Oracle Cloud companies to be Oracle Traditional. Oracle Traditional has the security incident,” Beaumont stated. “Oracle are denying it on ‘Oracle Cloud’ through the use of this scope — but it surely’s nonetheless Oracle cloud companies that Oracle handle. That is a part of the wordplay.”
BleepingComputer has contacted Oracle to substantiate whether or not these notices are respectable and never despatched by the menace actor or one other third social gathering, however we have not obtained a response. Oracle has additionally but to make clear if the breached servers are a part of Oracle Cloud Traditional or one other platform.
The breach that wasn’t a breach
This comes after the corporate privately acknowledged in calls with a few of its shoppers one week in the past that attackers stole previous shopper credentials after breaching a “legacy atmosphere” final utilized in 2017.
Nevertheless, whereas Oracle informed clients that this was non-sensitive previous legacy knowledge, the menace actor behind the breach shared knowledge with BleepingComputer from the tip of 2024 and later posted newer information from 2025 on BreachForums.
BleepingComputer has additionally individually confirmed with a number of Oracle clients that samples of the leaked knowledge (together with related LDAP show names, e-mail addresses, given names, and different figuring out info) obtained from the menace actor had been legitimate after Oracle informed BleepingComputer that “There was no breach of Oracle Cloud. The revealed credentials are usually not for the Oracle Cloud. No Oracle Cloud clients skilled a breach or misplaced any knowledge.”
Cybersecurity agency CybelAngel first revealed final week that Oracle informed clients that an attacker deployed an online shell and extra malware on a few of Oracle’s Gen 1 (also referred to as Oracle Cloud Traditional) servers as early as January 2025. Till the breach was detected in late February, the menace actor allegedly stole knowledge from the Oracle Id Supervisor (IDM) database, together with consumer emails, hashed passwords, and usernames.
Final month, BleepingComputer first reported that Oracle privately notified clients of one other January breach at Oracle Well being (a software-as-a-service (SaaS) firm beforehand generally known as Cerner), which impacted affected person knowledge at a number of healthcare organizations and hospitals in the US.
Sources informed BleepingComputer {that a} menace actor named “Andrew”—who has but to say affiliation with an extortion or ransomware operation—is now extorting the breached hospitals, demanding thousands and thousands of {dollars} in cryptocurrency to not promote or leak the stolen knowledge.

Based mostly on an evaluation of 14M malicious actions, uncover the highest 10 MITRE ATT&CK methods behind 93% of assaults and the best way to defend in opposition to them.




