Oracle has lastly acknowledged to some clients that attackers have stolen outdated shopper credentials after breaching a “legacy setting” final utilized in 2017, Bloomberg reported.
Nonetheless, whereas Oracle instructed purchasers that is outdated legacy information that isn’t delicate, the risk actor behind the assault has shared information with BleepingComputer from the tip of 2024 and posted newer information from 2025 on a hacking discussion board.
In response to Bloomberg, the corporate additionally knowledgeable purchasers that cybersecurity agency CrowdStrike and the FBI are investigating the incident.
Cybersecurity agency CybelAngel first revealed that Oracle instructed purchasers that an attacker who gained entry to the corporate’s Gen 1 (often known as Oracle Cloud Basic) servers as early as January 2025 used a 2020 Java exploit to deploy an online shell and extra malware.
In the course of the breach, detected in late February, the attacker allegedly exfiltrated information from the Oracle Identification Supervisor (IDM) database, together with person emails, hashed passwords, and usernames.
This comes after a risk actor (generally known as rose87168) put up on the market 6 million information information on BreachForums on March 20 and launched a number of textual content information containing a pattern database, LDAP data, and a listing of the businesses as proof that the info was authentic, all of them allegedly stolen from Oracle Cloud’s federated SSO login servers.
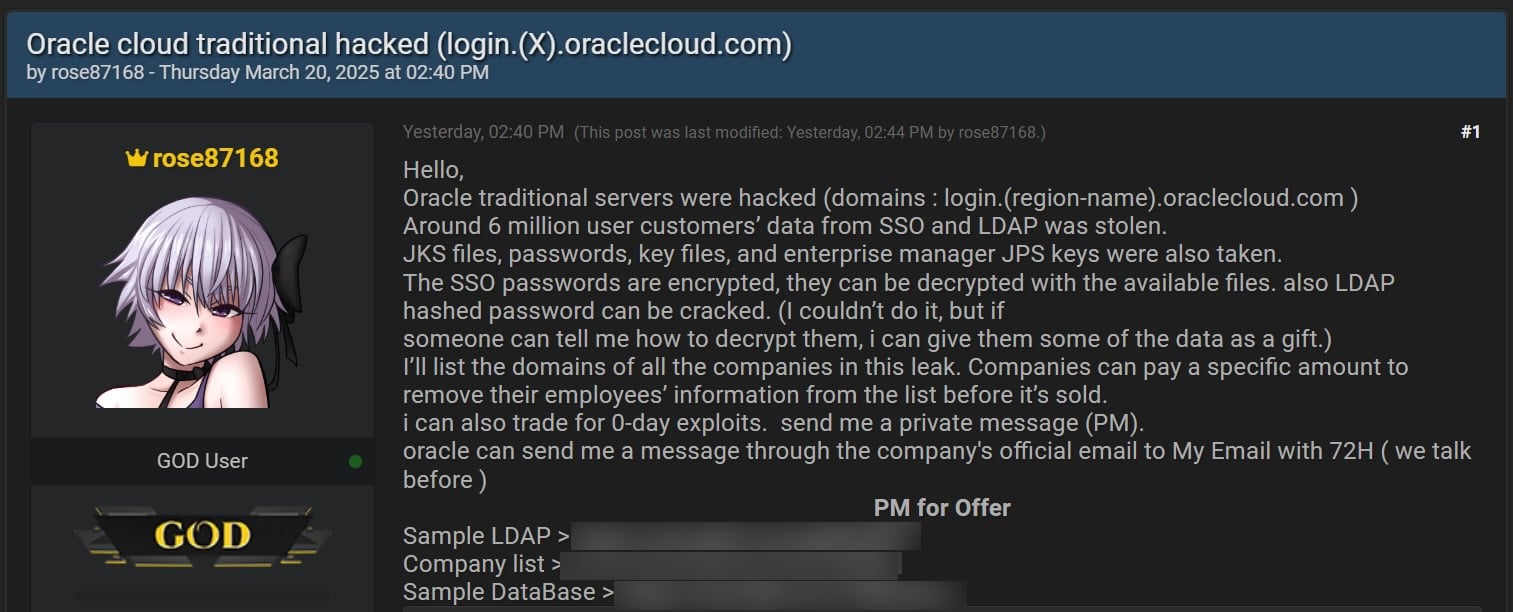
When requested to substantiate the authenticity of the leaked information, Oracle instructed BleepingComputer that “There was no breach of Oracle Cloud. The printed credentials will not be for the Oracle Cloud. No Oracle Cloud clients skilled a breach or misplaced any information.”
Oracle denied this even after an archived URL confirmed that the risk actor uploaded a file containing their e-mail tackle to considered one of Oracle’s servers. This URL was subsequently faraway from Archive.org, however an archive of the archive nonetheless exists.
Nonetheless, days later, BleepingComputer confirmed with a number of firms that further samples of the leaked information (together with related LDAP show names, e-mail addresses, given names, and different figuring out data) obtained from the risk actor had been legitimate.
Oracle has persistently denied studies of a breach in Oracle Cloud in statements shared with the press for the reason that incident surfaced. That is admittedly true because it aligns with the studies that Oracle is telling clients that the breach impacted an older platform generally known as Oracle Cloud Basic.
“Oracle rebadged outdated Oracle Cloud providers to be Oracle Basic. Oracle Basic has the security incident,” cybersecurity knowledgeable Kevin Beaumont confirmed on Monday. “Oracle are denying it on ‘Oracle Cloud’ by utilizing this scope — nevertheless it’s nonetheless Oracle cloud providers that Oracle handle. That’s a part of the wordplay.”
An Oracle spokesperson was not instantly out there for remark when contacted by BleepingComputer earlier at the moment for extra particulars on the Oracle Cloud breach.
Breach at Oracle Well being
Final week, Oracle additionally notified clients of a breach on the software-as-a-service (SaaS) firm Oracle Well being(previously Cerner), impacting a number of U.S. healthcare organizations and hospitals.
Despite the fact that the corporate has not publicly disclosed this incident, BleepingComputer confirmed that affected person information was stolen within the assault, as confirmed by non-public communications between Oracle Well being and impacted clients and from conversations with these concerned.
Oracle Well being stated it detected the breach of legacy Cerner information migration servers on February 20, 2025, and that the attackers used compromised buyer credentials to hack into the servers someday after January 22, 2025.
Sources instructed BleepingComputer that the impacted hospitals at the moment are being extorted by a risk actor named “Andrew,” who has not claimed affiliation with extortion or ransomware teams.
The risk actor is demanding tens of millions of {dollars} in cryptocurrency to not leak or promote the stolen information and has created clearnet web sites in regards to the breach to stress the hospitals into paying the ransom.
BleepingComputer has contacted Oracle Well being a number of instances about this incident since March 4, however we’ve got not obtained a reply.

Primarily based on an evaluation of 14M malicious actions, uncover the highest 10 MITRE ATT&CK methods behind 93% of assaults and tips on how to defend in opposition to them.




