Oracle has linked an ongoing extortion marketing campaign claimed by the Clop ransomware gang to E-Enterprise Suite (EBS) vulnerabilities that have been patched in July 2025.
Whereas the corporate has but to attribute the assault to this ransomware operation, Rob Duhart, the Chief Safety Officer of Oracle, confirmed that clients had obtained extortion emails from the gang.
Duhart additionally urged Oracle clients to replace their software program and suggested these requiring additional help to contact the Oracle assist group.
“Oracle is conscious that some Oracle E-Enterprise Suite (EBS) clients have obtained extortion emails, Duhart stated in a Thursday assertion. “Our ongoing investigation has discovered the potential use of beforehand recognized vulnerabilities which are addressed within the July 2025 Crucial Patch Replace. Oracle reaffirms its robust advice that clients apply the newest Crucial Patch Updates.”
Though it did not pinpoint a selected vulnerability that might have been exploited, Oracle addressed 9 security flaws impacting its E-Enterprise Suite as a part of its July 2025 Crucial Patch Replace, three of them (CVE-2025-30745, CVE-2025-30746, and CVE-2025-50107) exploitable remotely with out requiring person credentials.
Mandiant and the Google Risk Intelligence Group (GTIG) instructed BleepingComputer this week that executives at a number of firms have obtained emails requesting ransoms to stop delicate information allegedly stolen from their Oracle E-Enterprise Suite techniques from being leaked on-line.
In response to Genevieve Stark, the pinnacle of GTIG’s cybercrime unit, the attackers started sending these extortion emails “on or earlier than September 29, 2025,” and the menace analysts are nonetheless investigating this malicious exercise.
“We’re CL0P group. If you have not heard about us, you may google about us on web. We’ve just lately breached your Oracle E-Enterprise Suite software and copied loads of paperwork. All of the personal recordsdata and different data are actually held on our system,” an extortion e-mail shared with BleepingComputer reads.
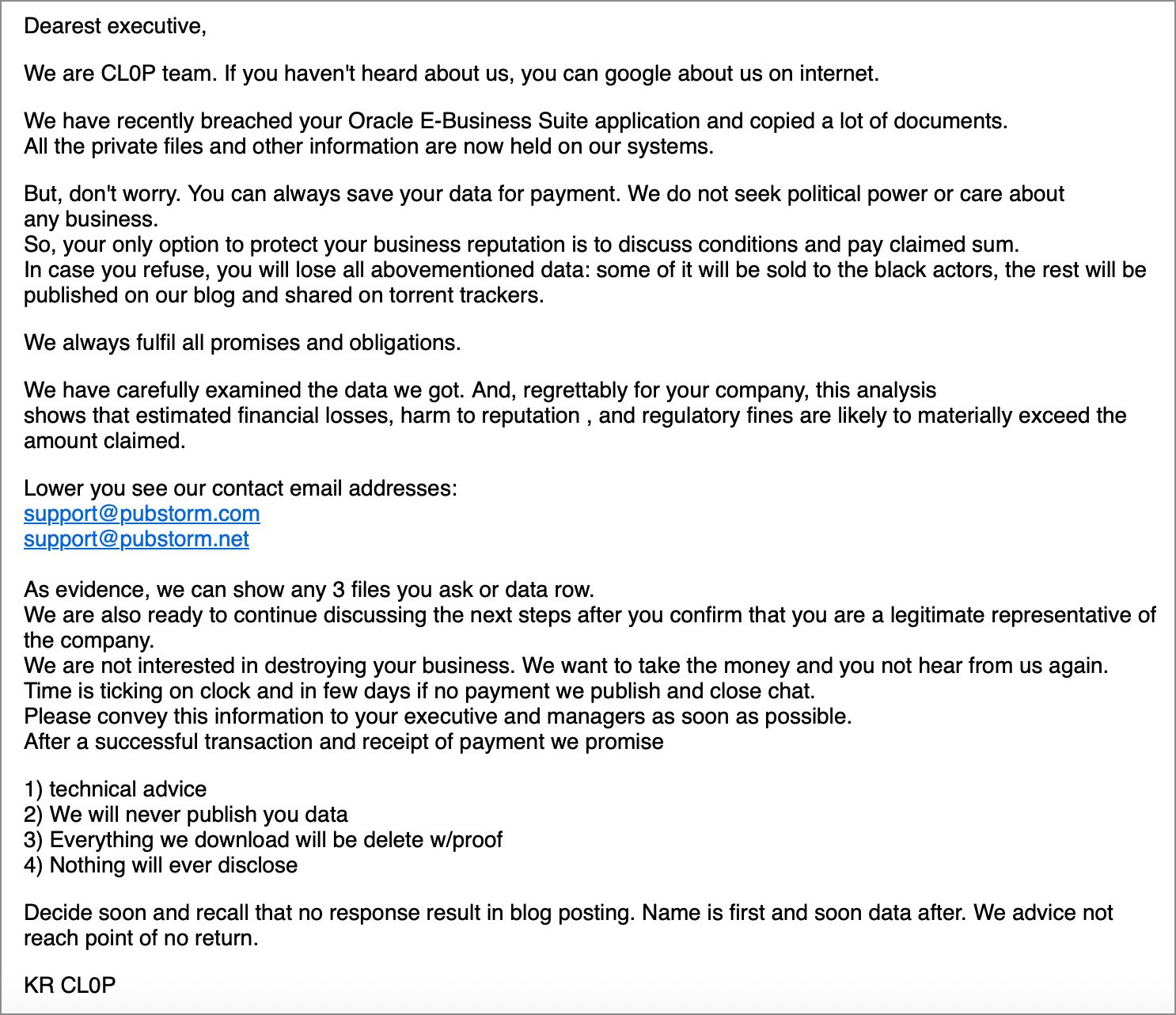
Whereas Mandiant Chief Expertise Officer Charles Carmakal acknowledged that there’s inadequate proof to find out if information has really been stolen, the Clop gang claimed in a press release shared with BleepingComputer that they’re concerned within the extortion marketing campaign, linking the assaults to a bug in an Oracle product.
“Quickly all will change into apparent that Oracle bugged up their core product and as soon as once more, the process is on clop to save lots of the day. We don’t injury to techniques and solely count on fee for providers we offer to guard a whole bunch of greatest firms in world,” Clop stated.
Clop’s claims observe the extortion of dozens of victims in January, who have been breached in an enormous wave of knowledge theft assaults focusing on a zero-day vulnerability (CVE-2024-50623) in Cleo’s safe file switch software program.
Beforehand, the cybercrime group was linked to a number of different information theft campaigns focusing on zero-day flaws in Accellion FTA, GoAnywhere MFT, and MOVEit Switch, with the latter impacting over 2,770 organizations worldwide.
The U.S. State Division now affords a $10 million reward for any data linking Clop ransomware assaults to a international authorities.

Be a part of the Breach and Attack Simulation Summit and expertise the way forward for security validation. Hear from prime specialists and see how AI-powered BAS is reworking breach and assault simulation.
Do not miss the occasion that can form the way forward for your security technique




