Oracle denies it was breached after a menace actor claimed to be promoting 6 million knowledge data allegedly stolen from the corporate’s Oracle Cloud federated SSO login servers.
“There was no breach of Oracle Cloud. The printed credentials usually are not for the Oracle Cloud. No Oracle Cloud clients skilled a breach or misplaced any knowledge,” the corporate advised BleepingComputer.
This assertion comes after a menace actor generally known as rose87168 launched a number of textual content recordsdata yesterday containing a pattern database, LDAP info, and an inventory of the businesses that they claimed have been stolen from Oracle Clouds’ SSO platform.
As additional proof that that they had entry to Oracle Cloud servers, the menace actor shared this URL with BleepingComputer, exhibiting an Web Archive URL that signifies they uploaded a .txt file containing their ProtonMail e mail tackle to the login.us2.oraclecloud.com server.
BleepingComputer contacted Oracle once more to elucidate how the menace actor uploaded a textual content file containing their e mail tackle with out entry to Oracle Cloud servers.
Alleged Oracle data breach
rose87168 is now promoting the allegedly stolen knowledge from Oracle Cloud’s SSO service for an undisclosed value or in change for zero-day exploits on the BreachForums hacking discussion board.
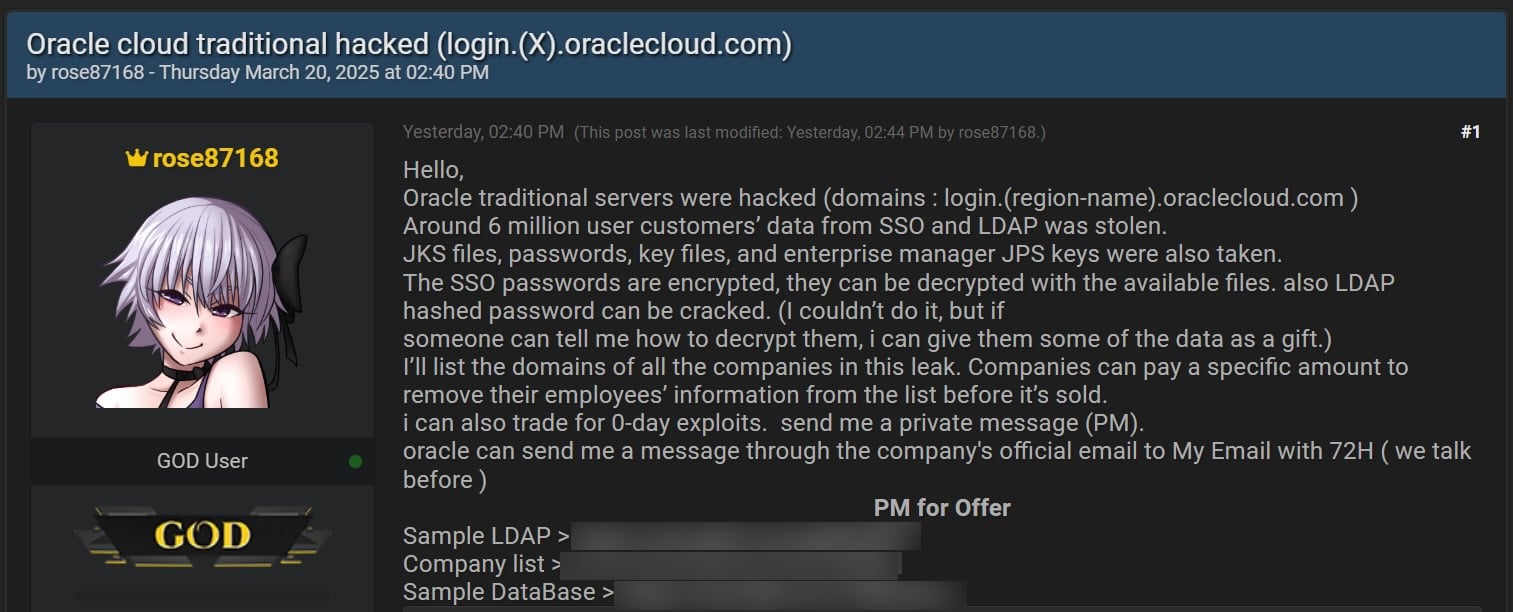
They are saying the information (together with encrypted SSO passwords, Java Keystore (JKS) recordsdata, key recordsdata, and enterprise supervisor JPS keys) was stolen after hacking into ‘login.(region-name).oraclecloud. com’ Oracle servers.
“The SSO passwords are encrypted, they are often decrypted with the accessible recordsdata. additionally LDAP hashed password might be cracked,” rose87168 says. “I am going to listing the domains of all the businesses on this leak. Corporations will pay a certain amount to take away their workers’ info from the listing earlier than it is offered.”
They’ve additionally supplied to share a number of the knowledge with anybody who might help decrypt the SSO passwords or crack the LDAP passwords.
The menace actor advised BleepingComputer they gained entry to Oracle Cloud servers round 40 days in the past and claimed to e mail the corporate after exfiltrating knowledge from the US2 and EM2 cloud areas.
Within the e mail change, rose87168 stated they requested Oracle to pay 100,000 XMR for info on how they breached the servers, however the firm allegedly refused to pay after asking for “all info wanted for repair and patch
BleepingComputer has contacted varied corporations whose knowledge was allegedly stolen to substantiate whether or not it is legitimate. We’ll replace this text if we hear again.

Primarily based on an evaluation of 14M malicious actions, uncover the highest 10 MITRE ATT&CK methods behind 93% of assaults and easy methods to defend in opposition to them.




