PcComponentes, a serious know-how retailer in Spain, has denied claims of a data breach on its techniques impacting 16 million prospects, however confirmed it suffered a credential stuffing assault.
The Spanish e-commerce firm specializes within the sale of computer systems, laptops, peripherals, and {hardware}, and has an estimated 75 million distinctive market guests per 12 months.
Yesterday, a risk actor named ‘daghetiaw’ revealed what they claimed to be a buyer database stolen from PcComponentes, containing 16.3 million data. The risk actor leaked 500,000 data and supplied to promote the remaining to the best bidder.

The leaked information incorporates order particulars, bodily addresses, full names, cellphone numbers, IP addresses, product wish-lists, and buyer assist messages exchanged with the agency through Zendesk.
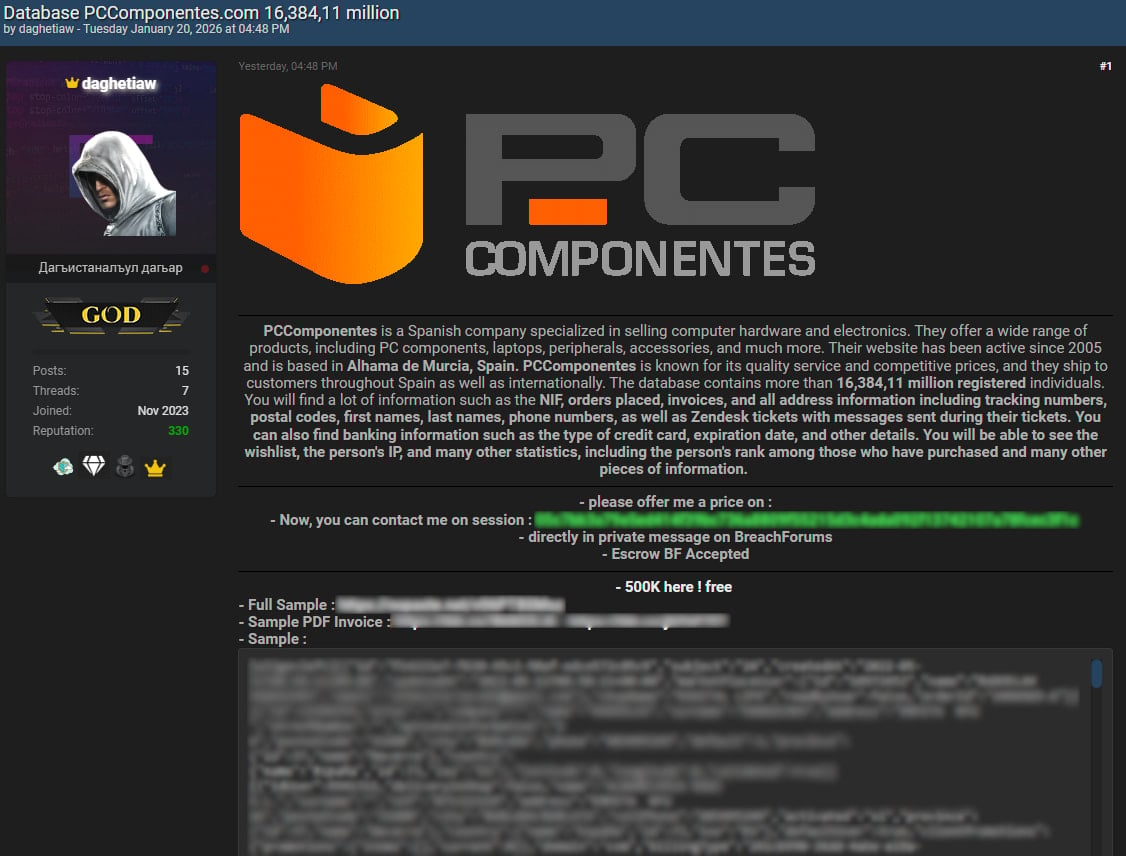
Supply: BleepingComputer
In an announcement in the present day, PcComponents says that it investigated a potential breach of its techniques, however its security consultants discovered no proof of unauthorized entry.
“There was no illegitimate entry to our databases or inner techniques,” the corporate assures, including that “the determine of 16 million supposedly affected prospects is fake, because the variety of lively PcComponentes accounts is considerably decrease.”
The corporate additionally underlined that no monetary particulars or buyer passwords are saved on its techniques.
Nonetheless, PcComponentes admitted that its investigation found proof of a credential stuffing assault on its platform. Because of this a risk actor tried e-mail addresses and passwords from different security breaches or leaked databases to seek out PcComponentes accounts.
Credential stuffing assaults are usually automated and depend on massive volumes of reused login credentials from different providers.
An investigation from risk intelligence firm Hudson Rock found that the attackers possible collected the login information from computer systems contaminated with info-stealing malware.
“Each single e-mail we checked from the risk actor’s pattern was present in present infostealer logs,” Hudson Rock says in a publish in the present day, including that among the logins had been as previous as 2020.
A screenshot that Hudson Rock revealed reveals a set of six e-mail addresses that had been verified and all of them had been marked as beforehand compromised in infostealer infections.
In response to PcComponentes’ announcement, the next information was uncovered for a small variety of compromised accounts:
- First and final names
- Nationwide ID quantity
- Bodily addresses
- IP addresses
- E-mail addresses
- Telephone numbers
In response to the incident, PcComponentes has applied a set of defenses that embody CAPTCHA on the login pages, necessary activation of two-factor authentication (2FA) for all accounts, and invalidation of all lively classes.
Because of this, prospects will probably be robotically logged out, and accounts with out two-factor authentication (2FA) will probably be required to allow it earlier than regaining entry.
PcComponentes additionally recommends that prospects use robust, distinctive passwords for every account, retailer their passwords in a password supervisor, and keep vigilant for potential phishing messages.
BleepingComputer has contacted PcComponentes to ask what number of prospects have been impacted exactly, however an announcement wasn’t instantly obtainable.

Whether or not you are cleansing up previous keys or setting guardrails for AI-generated code, this information helps your crew construct securely from the beginning.
Get the cheat sheet and take the guesswork out of secrets and techniques administration.




