The Ohio Lottery is sending data breach notification letters to over 538,000 people affected by a cyberattack that hit the group’s programs on Christmas Eve.
A submitting with the Workplace of Maine’s Lawyer Normal revealed that the incident impacted 538,959 people. The attackers gained entry to the affected individuals’s names, Social Safety numbers, and different private identifiers.
“On or about December 24, 2023, the Ohio Lottery detected unauthorized entry to our inside workplace community because of a cybersecurity incident that resulted within the publicity of the information we keep. The incident didn’t influence the gaming community,” the Ohio Lottery stated.
“After an intensive forensic investigation and our handbook doc evaluation, we realized on April 5, 2024 that sure recordsdata containing your private data was topic to unauthorized entry.”
Ohio Lottery says that no proof was discovered that the stolen data had been used for fraud. Nonetheless, it gives free credit score monitoring and id theft safety providers to all probably impacted people “out of an abundance of warning.”
Breach claimed by DragonForce ransomware
Whereas the Ohio Lottery did not reveal the character of the incident, which affected cell and prize-cashing operations, the DragonForce ransomware gang claimed the assault days later.
The menace actors claimed they encrypted gadgets and stole paperwork belonging to each Ohio Lottery clients and workers.
An entry added to the ransomware group’s darkish net leak web site on December 27 stated the attackers stole over 3 million information. After negotiations failed, the gang leaked 4 .bak archives and a number of CSV recordsdata on January 22, allegedly stolen from Ohio Lottery’s programs.
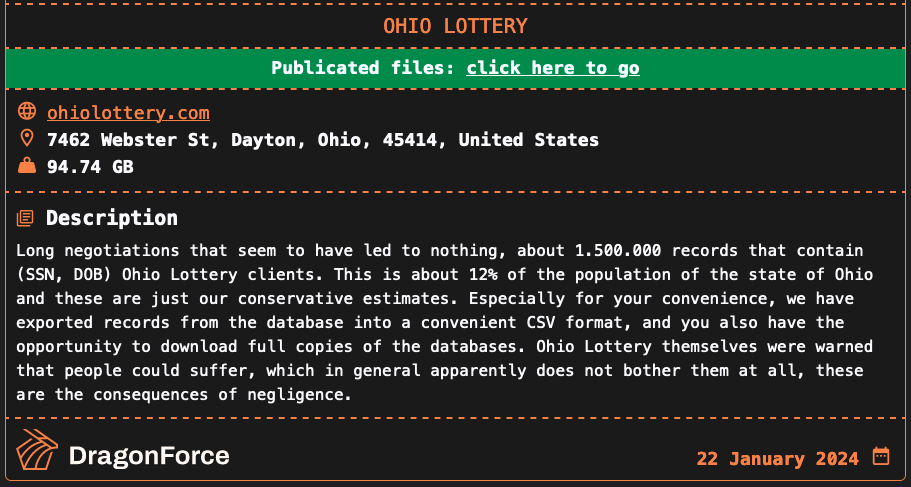
DragonForce says the 94 GB of leaked knowledge accommodates just one.500.000 information with Ohio Lottery shoppers’ names, Social Safety numbers, and dates of start.
Whereas DragonForce ransomware is a comparatively new operation that uncovered its first sufferer in December 2023, the techniques, negotiation model, and knowledge leak web site counsel an skilled extortion group.
Since their leak web site now lists virtually 4 dozen victims and regulation enforcement has been disrupting many ransomware operations in current months, it would not be shocking if this was a rebrand of a beforehand recognized gang.
DragonForce ransomware additionally claimed a cyberattack that impacted Japanese probiotic beverage producer Yakult’s IT programs in Australia and New Zealand in mid-December.
Yakult disclosed the assault after the ransomware gang leaked what it claimed to be 95 GB of knowledge stolen from the corporate’s compromised servers.




