Microsoft says that the North Korean Lazarus and Andariel hacking teams are exploiting the CVE-2023-42793 flaw in TeamCity servers to deploy backdoor malware, more likely to conduct software program provide chain assaults.
TeamCity is a steady integration and deployment server organizations use as a part of their software program growth infrastructure.
In September, TeamCity mounted a vital 9.8/10 vulnerability tracked as CVE-2023-42793 that allowed unauthenticated attackers to remotely execute code.
Whereas TeamCity shortly mounted the vulnerability, risk actors, equivalent to ransomware gangs, started to take advantage of the flaw to breach company networks.
North Korean hackers exploit TeamCity
In a brand new report, Microsoft’s Menace intelligence workforce says that the Lazarus (aka Diamond Sleet and ZINC) and Andariel (aka Onyx Sleet and PLUTONIUM) hacking teams have been noticed exploiting CVE-2023-42793 to breach TeamCity servers.
Whereas Microsoft has not stated the last word purpose of those assaults, they imagine it may very well be to conduct software program provide chain assaults.
“In previous operations, Diamond Sleet and different North Korean risk actors have efficiently carried out software program provide chain assaults by infiltrating construct environments,” explains Microsoft.
“Given this, Microsoft assesses that this exercise poses a very excessive threat to organizations who’re affected. “
As soon as the risk actors breach a TeamCity server, they make the most of totally different assault chains to deploy backdoors and achieve persistence on the compromised community.
Lazarus was seen deploying the ForestTiger malware in a single assault chain, which is used as a backdoor for executing instructions on the breached server.
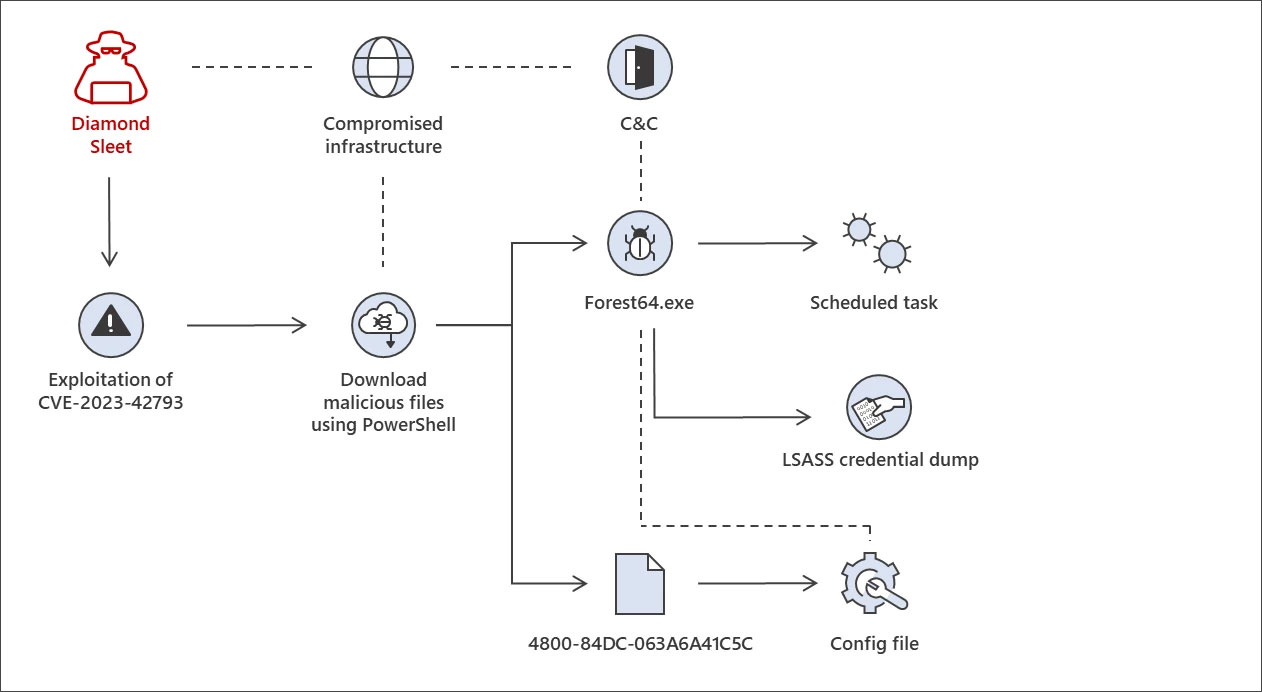
Supply: Microsoft
A second assault chain makes use of DLL search order hijacking assaults to launch a malware loader referred to as FeedLoad, which installs a distant entry Trojan (RAT).
Andariel makes use of a extra hands-on method of their assaults, making a ‘krtbgt’ admin account on the breached server and operating instructions to assemble system info.
The risk actors in the end deploy a payload that installs the HazyLoad proxy instrument, permitting a persistent connection between the compromised server and Andarial’s servers.
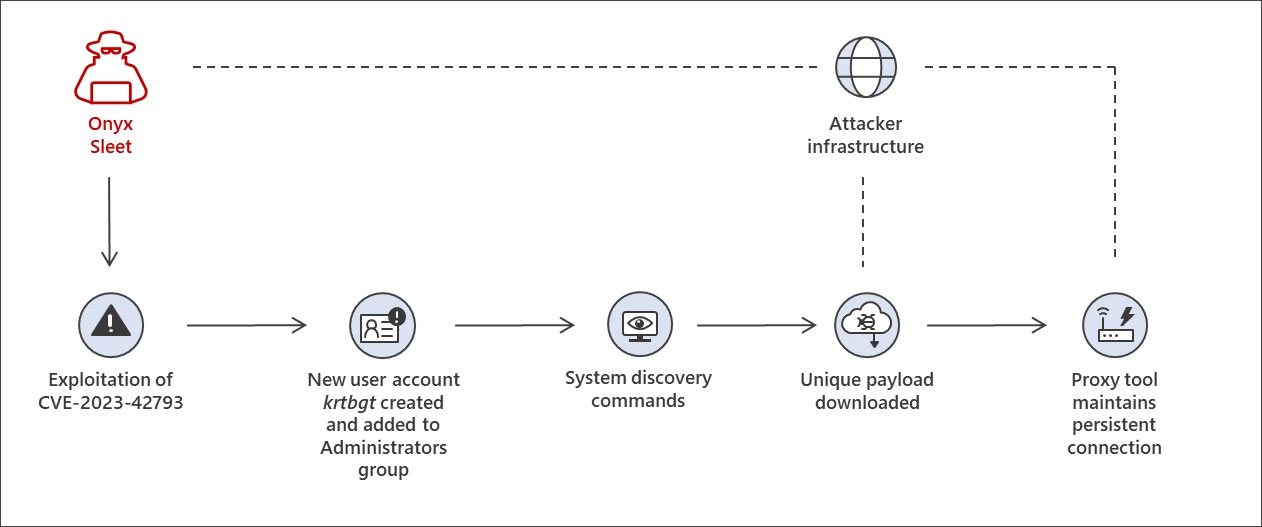
Supply: Microsoft
No matter how the assaults are performed, Microsoft says that the hackers in the end dump credentials from LSASS, seemingly used to unfold laterally on the compromised community.
Microsoft has shared extra technical particulars for all three of the noticed assault chains, together with indicators of compromise.
Who’s Lazarus and Andariel
Each Lazarus and Andariel are state-sponsored North Korean hacking teams, with Andariel a subgroup of Lazarus
Whereas the teams’ assaults are used to learn the North Korean authorities, their objectives might be totally different.
Lazarus has been linked to numerous espionage, information theft, and monetary achieve assaults, together with concentrating on security researchers, trojanizing open-source crypto platforms, performing huge cryptocurrency heists, and conducting pretend job interviews to distribute malware.
Alternatively, Andariel targets protection and IT providers entities in South Korea, the US, and India to conduct cyber espionage, information theft, damaging assaults, and ransomware assaults.
The group is thought to make the most of vulnerabilities for preliminary entry to company networks.




