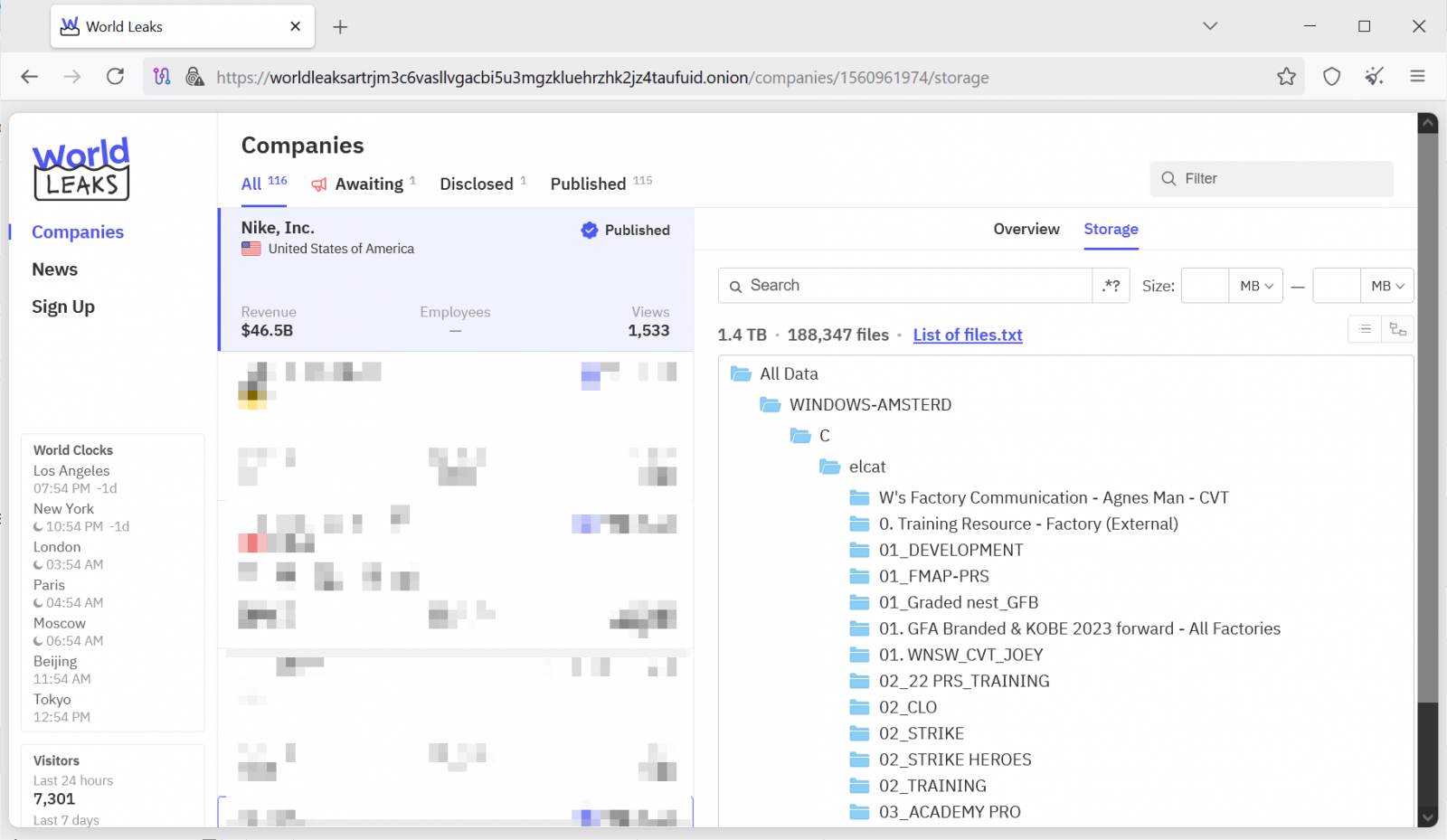
Nike is investigating what it described as a “potential cyber security incident” after the World Leaks ransomware gang leaked 1.4 TB of information allegedly stolen from the sportswear large.
“We all the time take shopper privateness and knowledge security very significantly,” the corporate advised BleepingComputer in an e mail assertion. “We’re investigating a possible cyber security incident and are actively assessing the scenario.”
This comes after the extortion group added Nike to its darkish net data-leak web site, claiming it stole practically 190,000 information containing company knowledge offering info on Nike’s enterprise operations.

Earlier than this text was revealed, World Leaks eliminated the Nike entry from its leak, suggesting that it could be negotiating with the corporate or that Nike has already paid a ransom to have the allegedly stolen paperwork eliminated.
Nevertheless, Nike has but to substantiate the extortion gang’s claims of knowledge theft, and BleepingComputer could not independently confirm whether or not the leaked information contained official knowledge.
World Leaks is believed to be a rebrand of the Hunters Worldwide ransomware, following a change from file encryption to knowledge theft and extortion-only assaults in January 2025, citing issues that ransomware operations have been changing into too dangerous and have been now not worthwhile.
Hunters Worldwide emerged in late 2023 and was itself flagged as a attainable Hive ransomware rebrand on account of code similarities, after claiming duty for over 280 assaults.
The record of victims contains the U.S. Marshals Service, the Indian multinational tech large Tata Applied sciences, the Japanese optics large Hoya, the North American car dealership AutoCanada, and the U.S. Navy contractor Austal USA.
Because it surfaced, World Leaks has additionally revealed knowledge stolen from dozens of organizations worldwide on its knowledge leak web site.
In July, World Leaks associates have been linked to the breach of certainly one of Dell’s product demonstration platforms and to the exploitation of end-of-life SonicWall SMA 100 units to put in customized OVERSTEP rootkit malware on compromised techniques.

Whether or not you are cleansing up previous keys or setting guardrails for AI-generated code, this information helps your workforce construct securely from the beginning.
Get the cheat sheet and take the guesswork out of secrets and techniques administration.




