A brand new variant of an Apple macOS malware known as XLoader has surfaced within the wild, masquerading its malicious options beneath the guise of an workplace productiveness app known as “OfficeNote.”
“The brand new model of XLoader is bundled inside a regular Apple disk picture with the title OfficeNote.dmg,” SentinelOne security researchers Dinesh Devadoss and Phil Stokes stated in a Monday evaluation. “The applying contained inside is signed with the developer signature MAIT JAKHU (54YDV8NU9C).”
XLoader, first detected in 2020, is taken into account a successor to Formbook and is an info stealer and keylogger supplied beneath the malware-as-a-service (MaaS) mannequin. A macOS variant of the malware emerged in July 2021, distributed as a Java program within the type of a compiled .JAR file.
“Such information require the Java Runtime Atmosphere, and for that purpose the malicious .jar file won’t execute on a macOS set up out of the field, since Apple stopped transport JRE with Macs over a decade in the past,” the cybersecurity agency famous on the time.
The newest iteration of XLoader will get round this limitation by switching to programming languages comparable to C and Goal C, with the disk picture file signed on July 17, 2023. Apple has since revoked the signature.
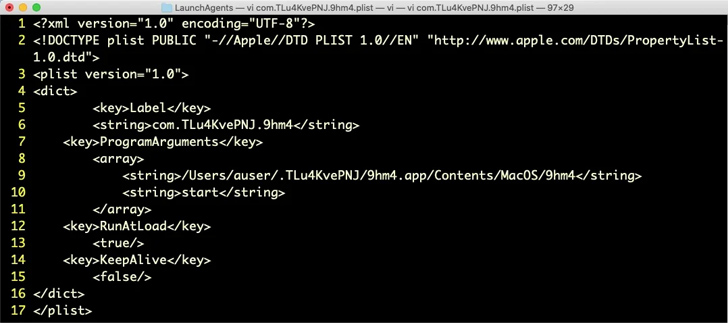
SentinelOne stated it detected a number of submissions of the artifact on VirusTotal all via the month of July 2023, indicating a widespread marketing campaign.
“Ads on crimeware boards provide the Mac model for rental at $199/month or $299/3 months,” the researchers stated. “Apparently, that is comparatively costly in comparison with Home windows variants of XLoader, which go for $59/month and $129/3 months.”
As soon as executed, OfficeNote throws an error message saying it “cannot be opened as a result of the unique merchandise cannot be discovered” as a diversion tactic, however, in actuality, it installs a Launch Agent within the background for persistence.
XLoader is designed to reap clipboard information in addition to info saved within the directories related to internet browsers comparable to Google Chrome and Mozilla Firefox. Safari, nevertheless, will not be focused.
Apart from taking steps to evade evaluation each manually and by automated options, the malware is configured to run sleep instructions to delay its execution and keep away from elevating any purple flags.
“XLoader continues to current a menace to macOS customers and companies,” the researchers concluded.
“This newest iteration masquerading as an workplace productiveness utility reveals that the targets of curiosity are clearly customers in a working surroundings. The malware makes an attempt to steal browser and clipboard secrets and techniques that might be used or offered to different menace actors for additional compromise.”




