A brand new DDoS (distributed denial of service) approach named ‘HTTP/2 Speedy Reset’ has been actively exploited as a zero-day since August, breaking all earlier information in magnitude.
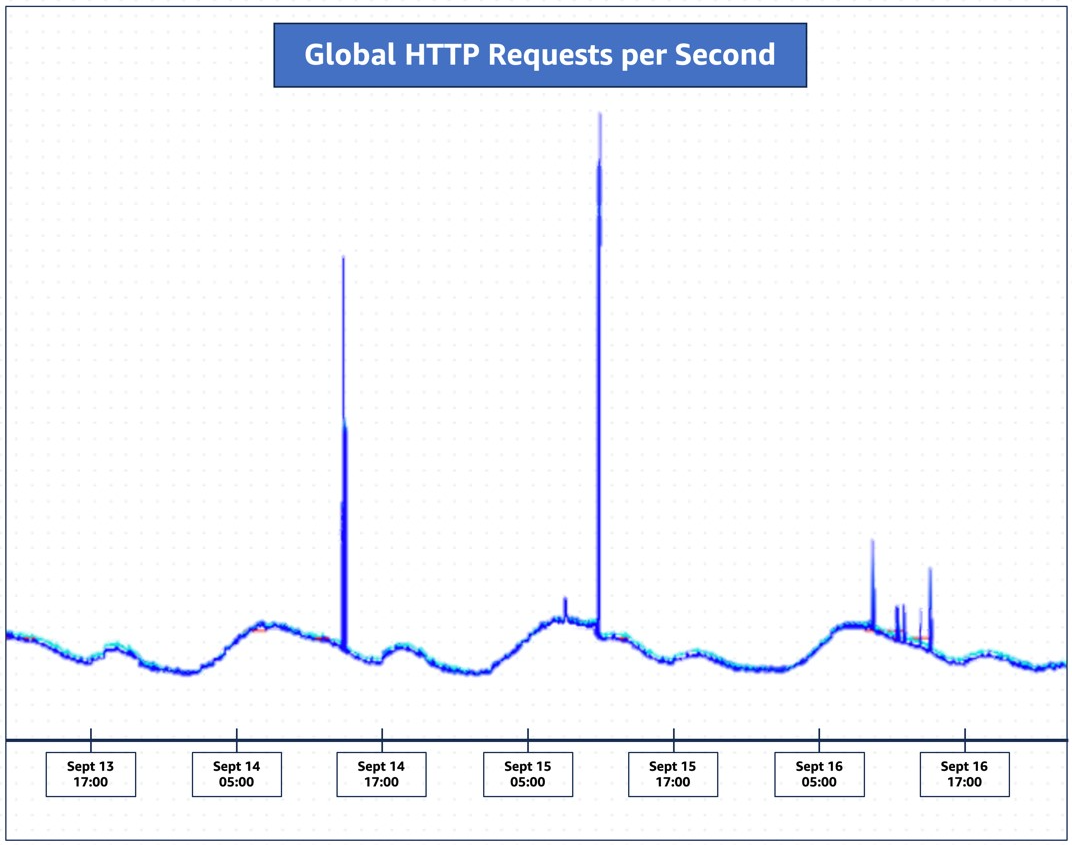
Information of the zero-day approach comes as a coordinated announcement at this time between Amazon Net Companies, Cloudflare, and Google, who report mitigating assaults reaching 155 million requests per second (Amazon), 201 million rps (Cloudflare), and a record-breaking 398 million rps (Google).
Google says they have been capable of mitigate these new assaults by including additional capability on the sting of their community.
Cloudflare feedback that the scale of the assault it mitigated is 3 times larger than its earlier report, from February 2023 (71 million rps), and it is alarming that this was achieved utilizing a comparatively small botnet comprising 20,000 machines.
Since late August, Cloudflare has detected and mitigated over a thousand ‘HTTP/2 Speedy Reset’ DDoS assaults that surpassed 10 million rps, with 184 breaking the earlier 71 million rps report.
Cloudflare is assured that as additional menace actors make use of extra expansive botnets together with this new assault technique, HTTP/2 Speedy Reset assaults will proceed to interrupt even larger information.
“There are botnets at this time which can be made up of a whole lot of 1000’s or thousands and thousands of machines,” feedback Cloudflare.
“Provided that your complete internet sometimes sees solely between 1–3 billion requests per second, it isn’t inconceivable that utilizing this technique may focus a whole internet’s value of requests on a small variety of targets.”
HTTP/2 Speedy Reset particulars
The novel assault exploits a zero-day vulnerability tracked as CVE-2023-44487, which abuses a weak point within the HTTP/2 protocol.
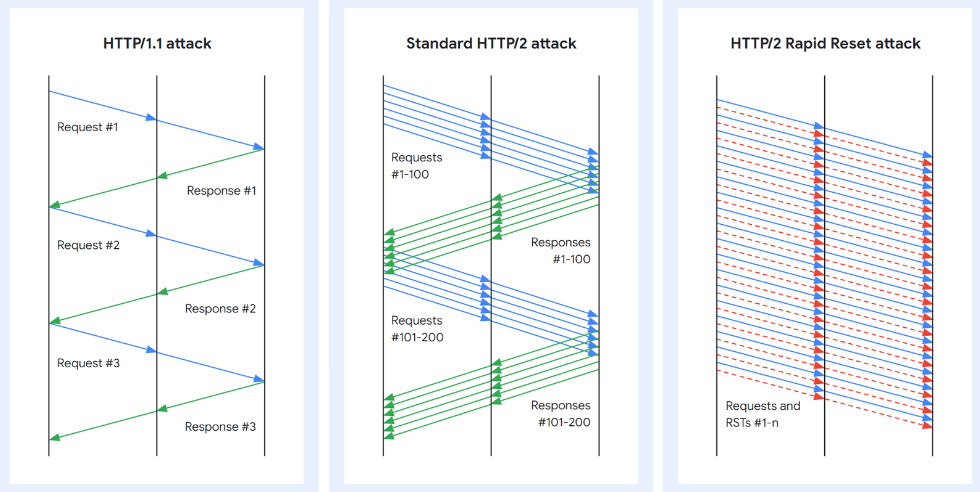
Merely put, the assault technique abuses HTTP/2’s stream cancellation characteristic to constantly ship and cancel requests, overwhelming the goal server/software and imposing a DoS state.
HTTP/2 encompasses a safeguard within the type of a parameter that limits the variety of concurrently energetic streams to forestall DoS assaults; nonetheless, this is not all the time efficient.
The protocol builders launched a extra environment friendly measure referred to as “request cancelation,” which does not tear down the entire connection however which may be abused.
Malicious actors have been abusing this characteristic since late August to ship a flurry of HTTP/2 requests and resets (RST_Stream frames) on a server, asking it to course of every of them and carry out fast resets, overwhelming its capability to answer new incoming requests.
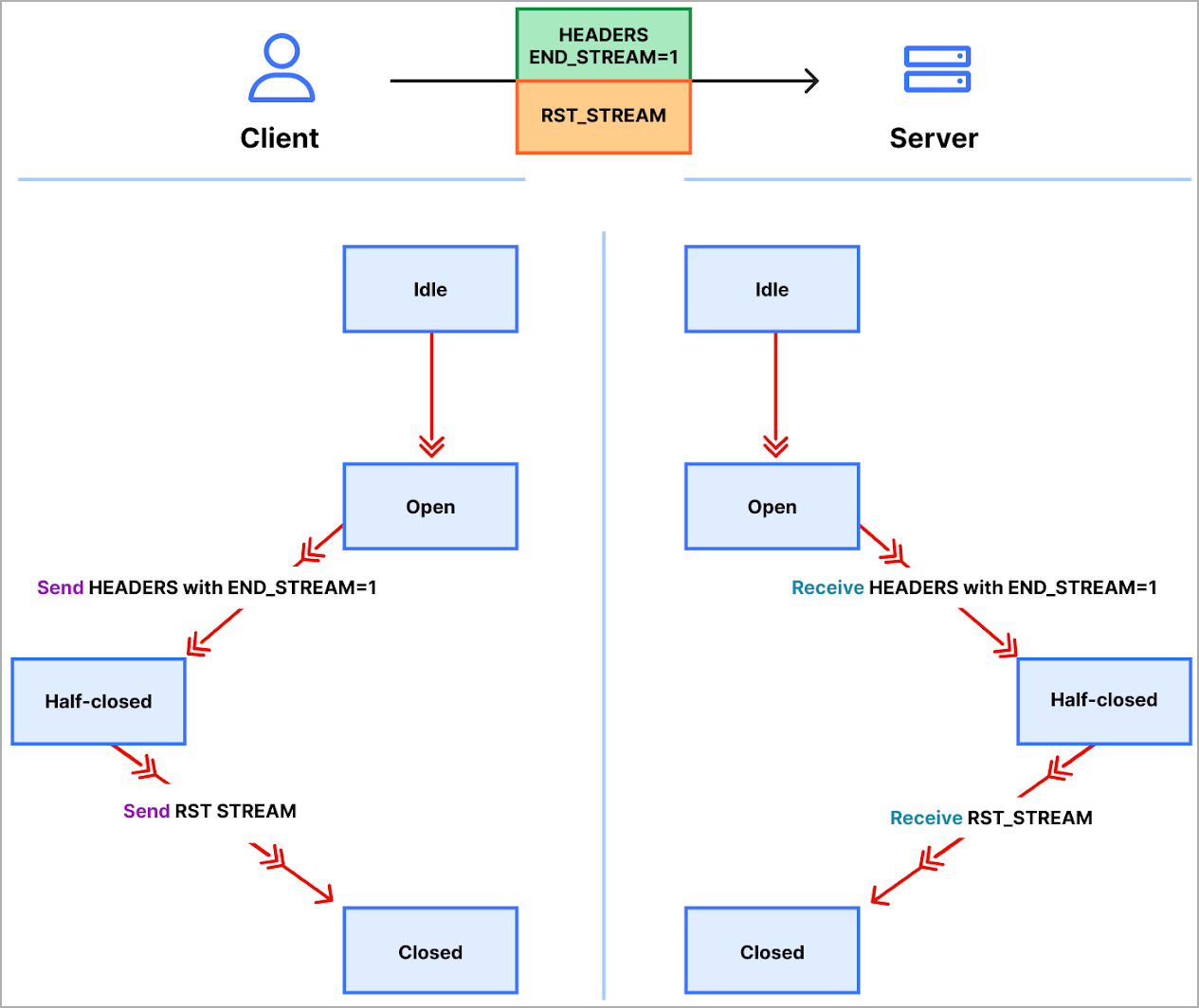
“The protocol doesn’t require the shopper and server to coordinate the cancelation in any means, the shopper could do it unilaterally,” explains Google in its publish on the problem.
“The shopper may additionally assume that the cancellation will take impact instantly when the server receives the RST_STREAM body, earlier than another knowledge from that TCP connection is processed.”
Suppliers develop mitigations
Cloudflare explains that HTTP/2 proxies or load-balancers are significantly prone to these lengthy strings of reset requests despatched rapidly.
The agency’s community was overwhelmed on the level between the TLS proxy and its upstream counterpart, so the injury was carried out earlier than the unhealthy requests reached the block level.
When it comes to real-world affect, these assaults have induced a rise in 502 error studies amongst Cloudflare’s shoppers.
Cloudflare says it will definitely mitigated these assaults utilizing a system designed to deal with hyper-volumetric assaults referred to as ‘IP Jail,’ which the web agency expanded to cowl its complete infrastructure.
This method “jails” offending IPs and bars them from utilizing HTTP/2 for any Cloudflare area for a time frame whereas impacting reliable customers sharing the jailed IP with a minor efficiency drop.
Amazon says it mitigated dozens of those assaults with out offering any particulars on their affect, highlighting that the supply of their buyer providers was maintained.
All three companies conclude that one of the best strategy for shoppers to counter HTTP/2 Speedy Reset assaults is to make use of all out there HTTP-flood safety instruments and bolster their DDoS resilience with multifaceted mitigations.
Sadly, as this tactic abuses the HTTP/2 protocol, there is no such thing as a basic repair that fully blocks attackers from utilizing this DDoS approach.
As an alternative, software program builders who make the most of the protocol of their software program are implementing price controls to mitigate HTTP/2 Speedy Reset assaults.
In a separate publish, Cloudflare explains that they needed to maintain the zero-day secret for over a month to permit security distributors and stakeholders time to react to the menace earlier than it is made identified to extra menace actors and the “cat and mouse” recreation begins.
“We have saved the knowledge restricted till at this time to provide as many security distributors as potential the chance to react,” defined Cloudflare
“Nevertheless, in some unspecified time in the future, the accountable factor turns into to publicly disclose zero-day threats like this. Right this moment is that day.”




