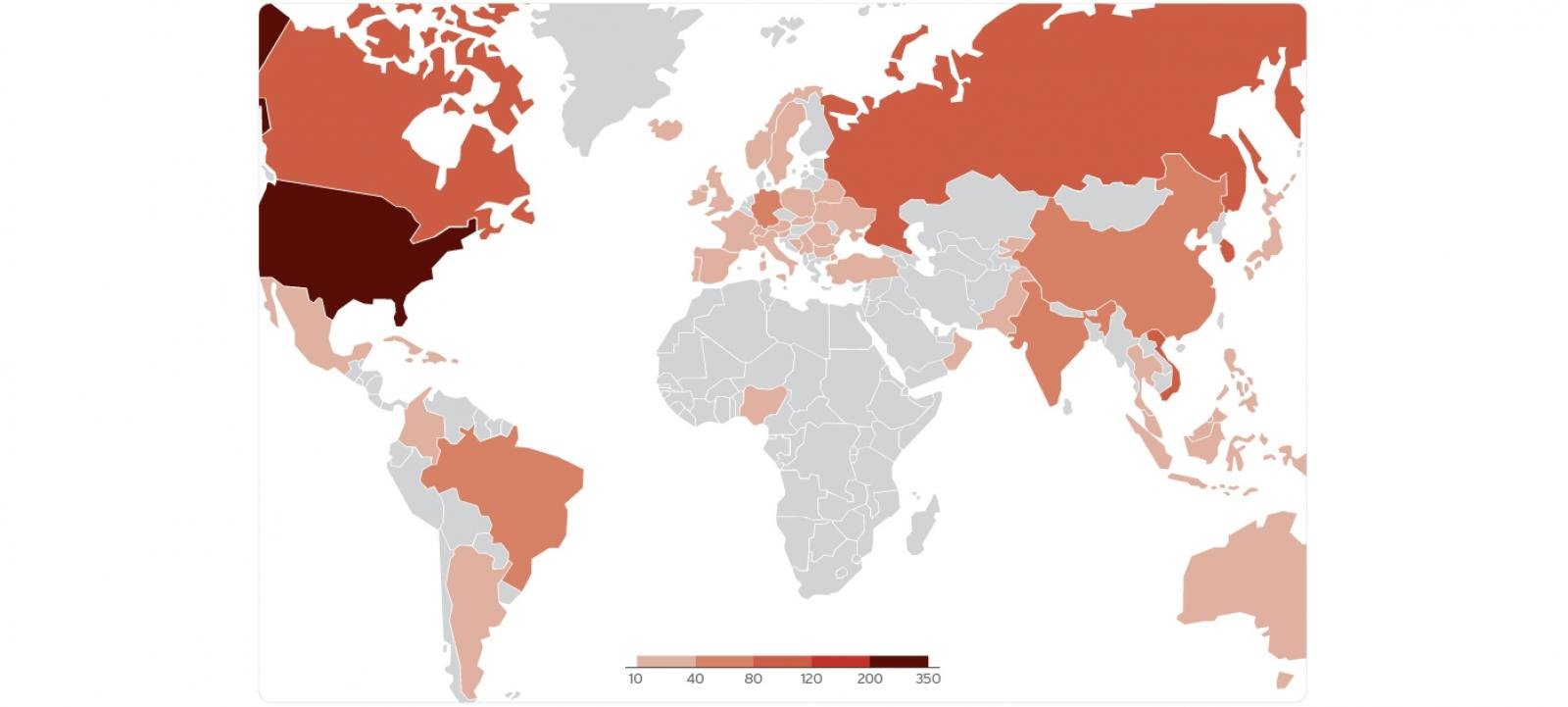
At the very least 11 state-backed hacking teams from North Korea, Iran, Russia, and China have been exploiting a brand new Home windows vulnerability in knowledge theft and cyber espionage zero-day assaults since 2017.
Nevertheless, as security researchers Peter Girnus and Aliakbar Zahravi with Pattern Micro’s Zero Day Initiative (ZDI) reported right now, Microsoft tagged it as “not assembly the bar servicing” in late September and mentioned it would not launch security updates to handle it.
“We found practically a thousand Shell Hyperlink (.lnk) samples that exploit ZDI-CAN-25373; nevertheless, it’s possible that the entire variety of exploitation makes an attempt are a lot greater,” they mentioned. “Subsequently, we submitted a proof-of-concept exploit via Pattern ZDI’s bug bounty program to Microsoft, who declined to handle this vulnerability with a security patch.”
A Microsoft spokesperson was not instantly obtainable for remark when contacted by BleepingComputer earlier right now.
Whereas Microsoft has but to assign a CVE-ID to this vulnerability, Pattern Micro is monitoring it internally as ZDI-CAN-25373 and mentioned it allows attackers to execute arbitrary code on affected Home windows programs.
Because the researchers discovered whereas investigating in-the-wild ZDI-CAN-25373 exploitation, the security flaw has been exploited in widespread assaults by many state-sponsored risk teams and cybercrime gangs, together with Evil Corp, APT43 (Kimsuky), Bitter, APT37, Mustang Panda, SideWinder, RedHotel, Konni, and others.
Though the campaigns have focused victims worldwide, they have been primarily centered on North America, South America, Europe, East Asia, and Australia. Out of all of the assaults analyzed, practically 70% have been linked to espionage and knowledge theft, whereas monetary acquire was the main focus of solely 20%.
”Numerous malware payloads and loaders like Ursnif, Gh0st RAT, and Trickbot have been tracked in these campaigns, with malware-as-a-service (MaaS) platforms complicating the risk panorama,” Pattern Micro added.
The ZDI-CAN-25373 Home windows zero-day
The Home windows zero-day, tracked as ZDI-CAN-25373, is brought on by a Person Interface (UI) Misrepresentation of Crucial Info (CWE-451) weak spot, which permits attackers to use how Home windows shows shortcut (.lnk) information to evade detection and execute code on susceptible gadgets with out the consumer’s information.
Risk actors exploit ZDI-CAN-25373 by hiding malicious command-line arguments inside .LNK shortcut information utilizing padded whitespaces added to the COMMAND_LINE_ARGUMENTS construction.
The researchers say these whitespaces could be within the type of hex codes for Area (x20), Horizontal Tab (x09), Linefeed (x0A), Vertical Tab (x0B), Type Feed (x0C), and Carriage Return (x0D) that can be utilized as padding.
If a Home windows consumer inspects such a .lnk file, the malicious arguments are usually not displayed within the Home windows consumer interface due to the added whitespaces. In consequence, the command line arguments added by the attackers stay hidden from the consumer’s view.
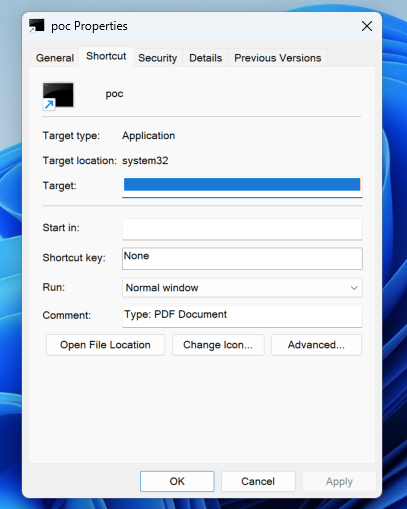
“Person interplay is required to use this vulnerability in that the goal should go to a malicious web page or open a malicious file,” a Pattern Micro advisory issued right now explains.
“Crafted knowledge in an .LNK file may cause hazardous content material within the file to be invisible to a consumer who inspects the file through the Home windows-provided consumer interface. An attacker can leverage this vulnerability to execute code within the context of the present consumer.”
This vulnerability is just like one other flaw tracked as CVE-2024-43461 that enabled risk actors to make use of 26 encoded braille whitespace characters (%E2percentA0percent80) to camouflage HTA information that may obtain malicious payloads as PDFs. CVE-2024-43461 was discovered by Peter Girnus, a Senior Risk Researcher at Pattern Micro’s Zero Day, and patched by Microsoft through the September 2024 Patch Tuesday.
The Void Banshee APT hacking group exploited CVE-2024-43461 in zero-day assaults to deploy information-stealing malware in campaigns towards organizations throughout North America, Europe, and Southeast Asia.

Primarily based on an evaluation of 14M malicious actions, uncover the highest 10 MITRE ATT&CK methods behind 93% of assaults and tips on how to defend towards them.




