A brand new set of vulnerabilities in 5G modems by Qualcomm and MediaTek, collectively referred to as “5Ghoul,” affect 710 5G smartphone fashions from Google companions (Android) and Apple, routers, and USB modems.
5Ghoul was found by college researchers from Singapore and consists of 14 vulnerabilities in cell communication methods, 10 of which have been publicly disclosed and 4 withheld for security causes.
The 5Ghoul assaults vary from non permanent service disruptions to community downgrades, which can be extra extreme from a security standpoint.
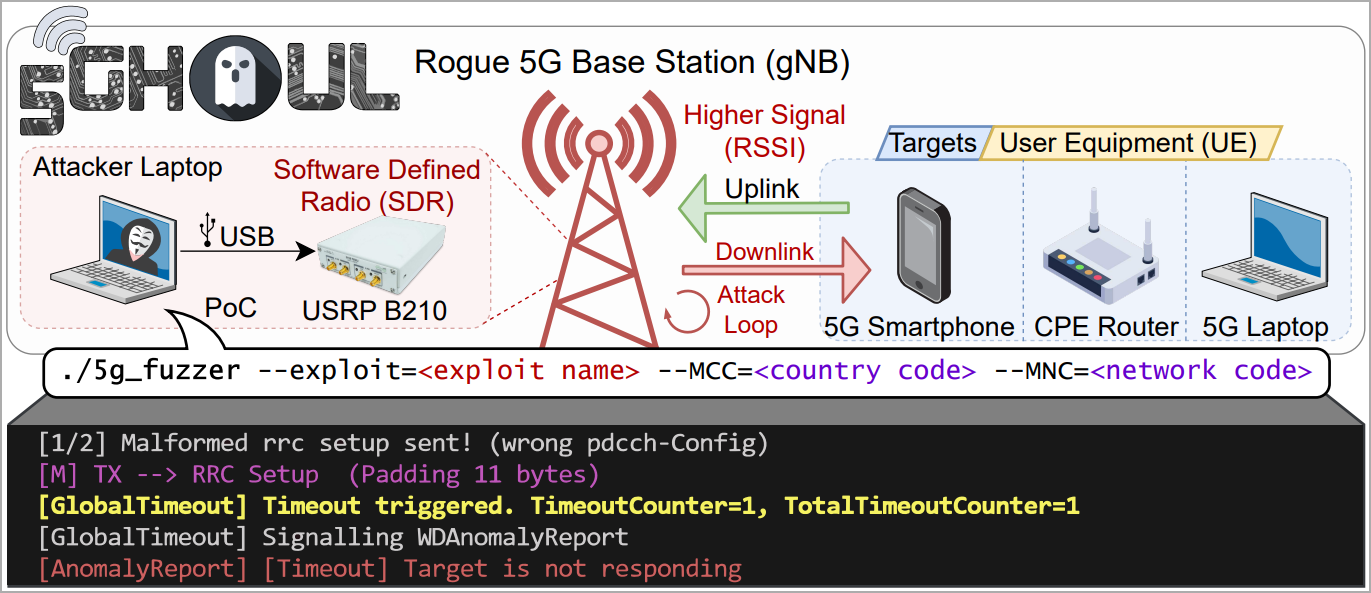
The researchers found the failings whereas experimenting with 5G modem firmware evaluation and report that the failings are simple to use over-the-air by impersonating a respectable 5G base station.
This is applicable even when attackers lack details about the goal’s SIM card, because the assault happens earlier than the NAS authentication step.
“The attacker doesn’t want to pay attention to any secret data of the goal UE e.g., UE’s SIM card particulars, to finish the NAS community registration,” explains the researchers on their web site.
“The attacker solely must impersonate the respectable gNB utilizing the recognized Cell Tower connection parameters (e.g., SSB ARFCN, Monitoring Space Code, Bodily Cell ID, Level A Frequency).”
Supply: asset-group.github.io
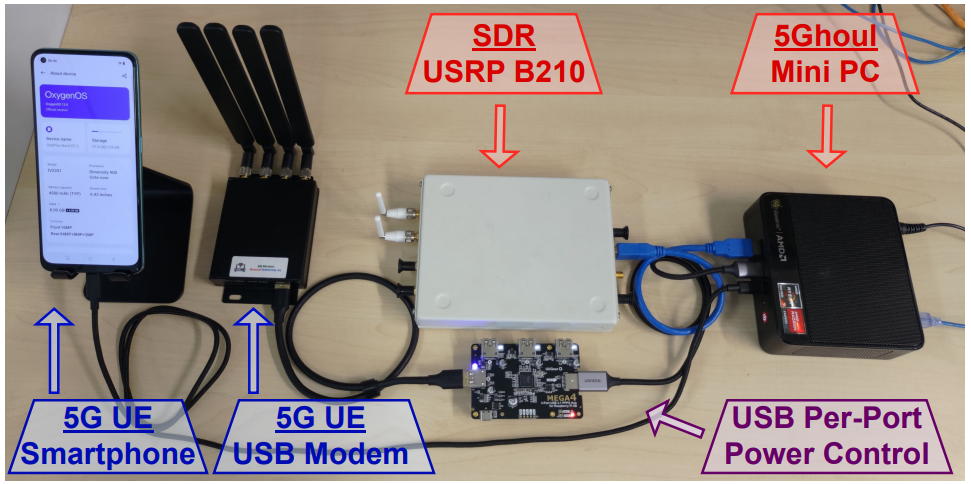
The above is achievable at the price of a couple of thousand USD, utilizing open-source software program for community evaluation and fuzzing, a mini PC, a software program outlined radio (SDR), and miscellaneous gear like cables, antennas, energy provides, and many others.
Supply: asset-group.github.io
5Ghoul vulnerability particulars
The ten 5Ghoul vulnerabilities which have been publicly disclosed to Qualcomm and MediaTek as of December 7, 2023, are:
- CVE-2023-33043: Invalid MAC/RLC PDU inflicting Denial of Service (DoS) in Qualcomm X55/X60 modems. Attackers can ship an invalid downlink MAC body to the goal 5G UE from a close-by malicious gNB, resulting in a brief cling and modem reboot.
- CVE-2023-33044: NAS Unknown PDU inflicting DoS in Qualcomm X55/X60 modems. This vulnerability permits attackers to ship an invalid NAS PDU to the goal UE, leading to modem failure and reboot.
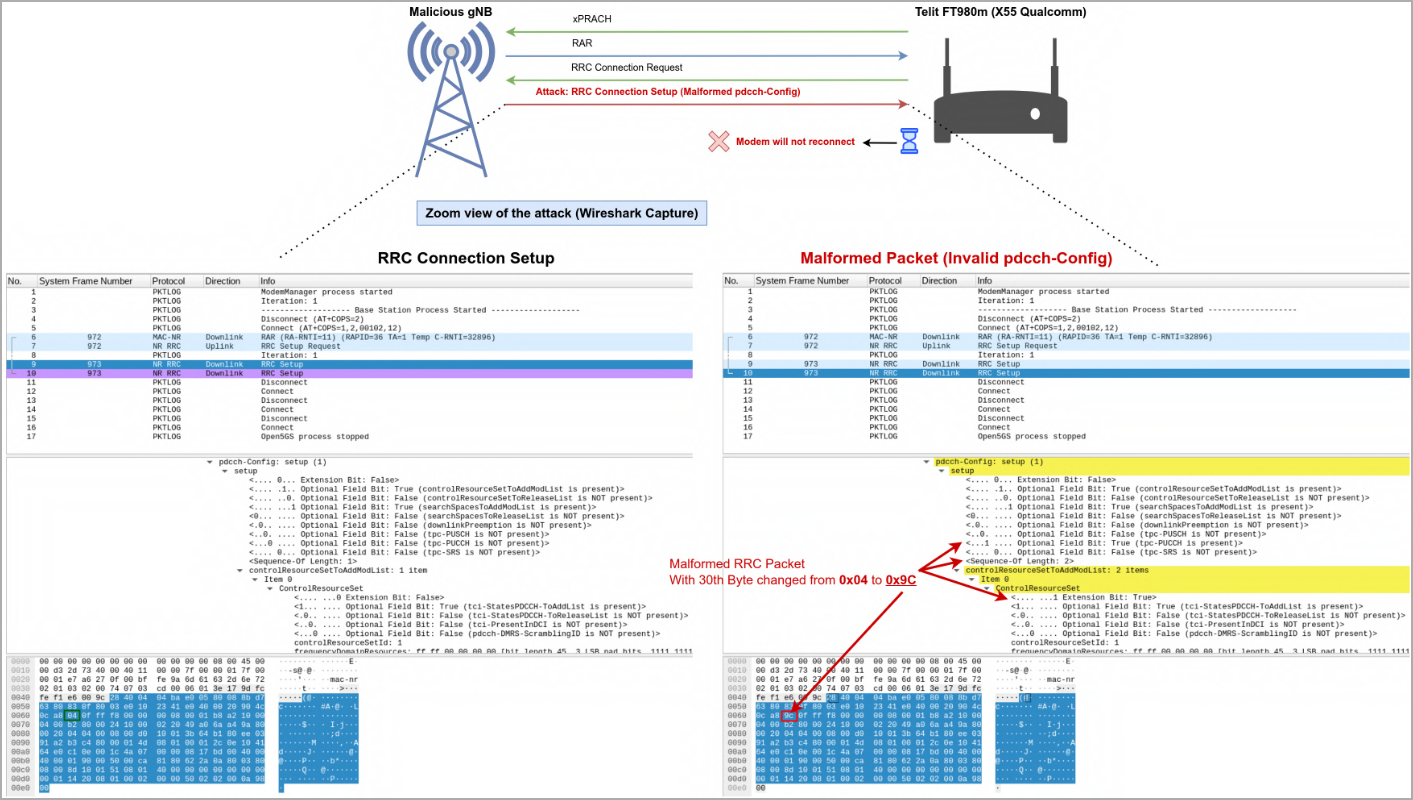
- CVE-2023-33042: Disabling 5G/Downgrade through Invalid RRC pdcch-Config in Qualcomm X55/X60 modems, resulting in both downgrade or denial of service. An attacker can ship a malformed RRC body in the course of the RRC Connect Process, disabling 5G connectivity and requiring a handbook reboot for restoration.
- CVE-2023-32842: Invalid RRC Setup spCellConfig inflicting DoS in MediaTek Dimensity 900/1200 modems. The vulnerability includes sending a malformed RRC Connection Setup, resulting in modem failure and reboot in affected units.
- CVE-2023-32844: Invalid RRC pucch CSIReportConfig inflicting DoS in MediaTek Dimensity 900/1200 modems. Attackers can ship a malformed RRC Connection Setup, inflicting the modem to fail and reboot.
- CVE-2023-20702: Invalid RLC Data Sequence inflicting DoS (null pointer dereference) in MediaTek Dimensity 900/1200 modems. An attacker can exploit this by sending a malformed RLC Standing PDU, resulting in a modem crash and reboot.
- CVE-2023-32846: Truncated RRC physicalCellGroupConfig inflicting DoS (null pointer dereference) in MediaTek Dimensity 900/1200 modems. Malformed RRC Connection Setup may cause reminiscence entry errors, resulting in a modem crash.
- CVE-2023-32841: Invalid RRC searchSpacesToAddModList inflicting DoS in MediaTek Dimensity 900/1200 modems. This includes sending a malformed RRC Connection Setup, inflicting a modem crash in affected units.
- CVE-2023-32843: Invalid RRC Uplink Config Factor inflicting DoS in MediaTek Dimensity 900/1200 modems. Sending a malformed RRC Connection Setup can lead to modem failure and reboot in affected units.
- CVE-2023-32845: Null RRC Uplink Config Factor inflicting DoS in MediaTek Dimensity 900/1200 modems. Malformed RRC Connection Setup can set off a modem crash by setting sure RRC payload fields to null.
CVE-2023-33042 is especially regarding as a result of it might probably pressure a tool to disconnect from a 5G community and fall again to 4G, exposing it to potential vulnerabilities within the 4G area that expose it to a broader vary of assaults.
Supply: asset-group.github.io
The DoS flaws in these vulnerabilities trigger the units to lose all connectivity till they’re rebooted. This is not as vital, though it might probably nonetheless have vital implications in mission-critical environments that depend on mobile service.
You will need to word that the disclosed flaws aren’t restricted to the units talked about within the above record.
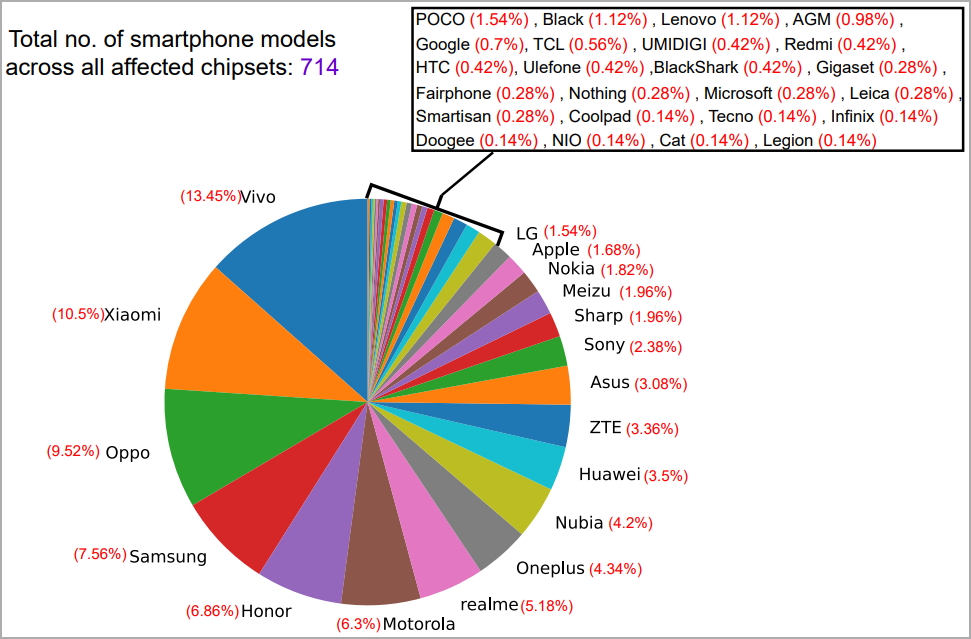
Figuring out all impacted fashions is ongoing, however the researchers have already confirmed that 714 smartphones from 24 manufacturers are impacted.
Some susceptible manufacturers embody telephones from POCO, Black, Lenovo, AGM, Google, TCL, Redmi, HTC, Microsoft, and Gigaset, with the whole record within the picture beneath.
Supply: asset-group.github.io
To be taught extra in regards to the 5Ghoul flaws, their exploitation potential and ramifications, and technical data may be present in the researchers’ whitepaper.
A proof-of-concept (PoC) exploit equipment may also be discovered of their GitHub repository.
Vendor response and fixes
Each Qualcomm and MediaTek launched security bulletins on Monday for the disclosed 5Ghoul vulnerabilities,
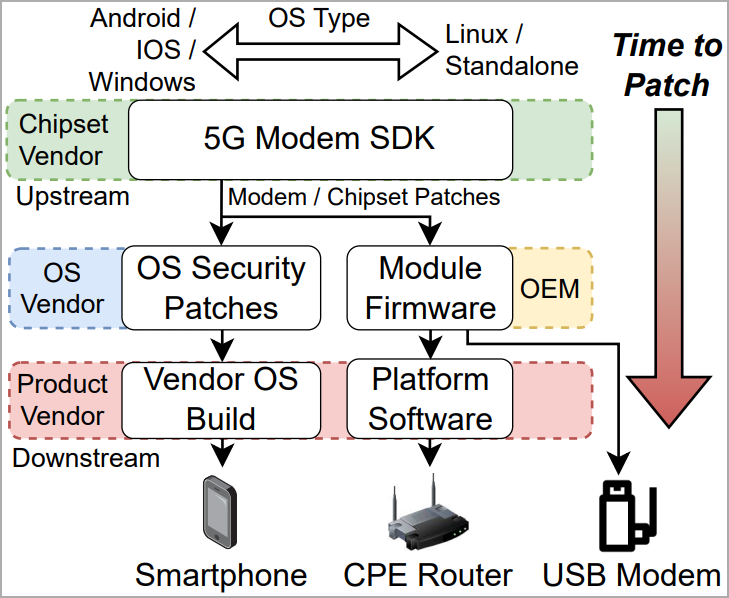
The security updates have been made obtainable to system distributors two months in the past. Nonetheless, given the complexity of the software program provide, particularly on Android, will probably be some time earlier than the fixes attain the tip customers through security updates.
Inevitably, some impacted smartphone fashions and different units won’t ever obtain the fixes as they are going to possible attain finish of assist first.
Supply: asset-group.github.io
In the event you’re overly nervous about 5Ghool flaws, the one sensible resolution is to keep away from utilizing 5G totally till fixes can be found.
Indicators of a 5Ghoul assault embody lack of 5G connections, incapacity to re-connect till the system is rebooted, and constant drop to 4G regardless of the provision of a 5G community within the space.




