Researchers discovered half a dozen vulnerabilities of various severity impacting Netgear WNR614 N300, a budget-friendly router that proved widespread amongst house customers and small companies.
The gadget reached end-of-life (EoL) and is not supported by Netgear however it’s nonetheless current in lots of environments as a consequence of its reliability, ease of use, and efficiency.
Researchers at RedFox Safety found within the router six vulnerabilities that vary from authentication bypass and weak password coverage to storing passwords in plain textual content and Wi-Fi Protected Setup (WPS) PIN publicity:
CVE-2024-36787: permits an attacker to bypass authentication and entry the executive interface through unspecified vectors. The flaw allows unauthorized entry to the router’s settings, posing a extreme risk to community security and delicate person knowledge.
Supply: RedFox
CVE-2024-36788: the router has improper setting of the HTTPOnly flag for cookies. An attacker may leverage the vulnerability to intercept and entry delicate communications between the router and the gadgets connecting to it.
CVE-2024-36789: permits attackers to create passwords that don’t adjust to correct security requirements and even settle for a single character as a password for the administrator account. This may result in unauthorized entry, community manipulation, and potential knowledge publicity.
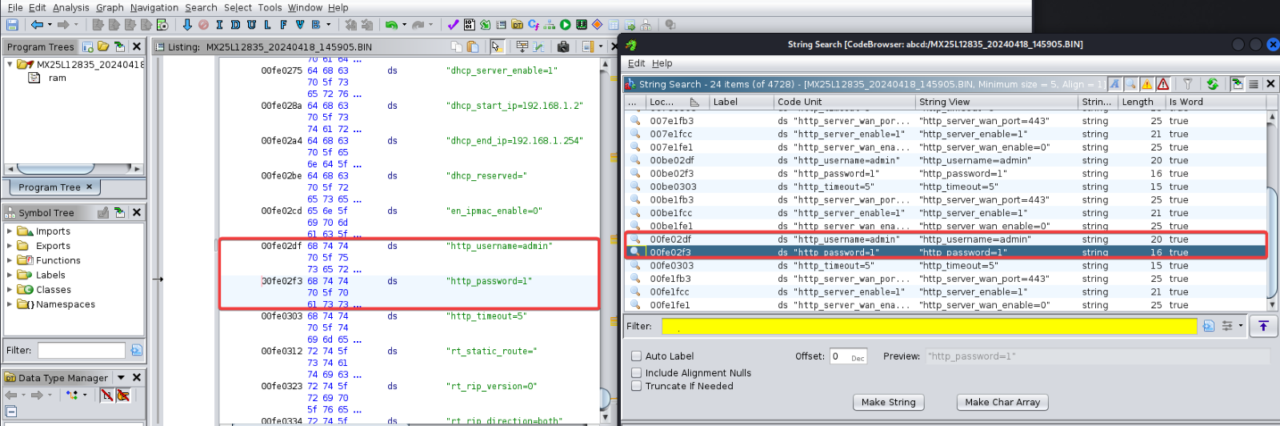
CVE-2024-36790: the router shops credentials in plain textual content, which makes it straightforward for an attacker to acquire unauthorized entry, manipulate the router, and expose delicate knowledge.
Supply: RedFox
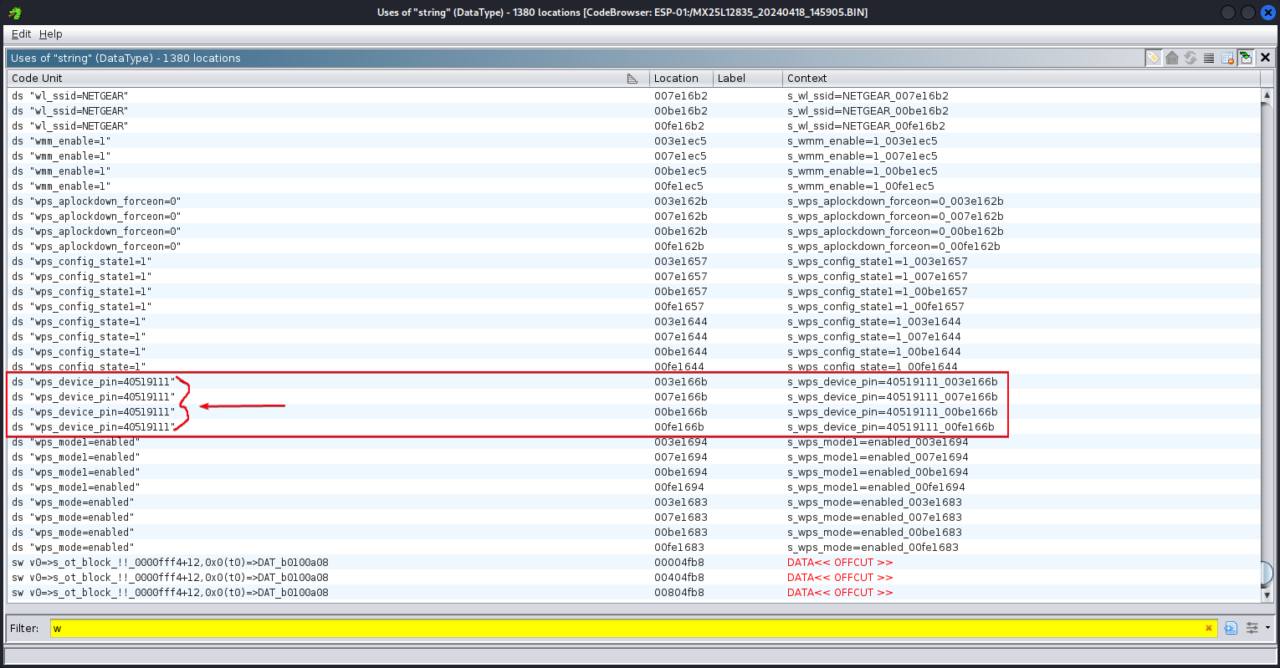
CVE-2024-36792: the implementation of the WPS Wi-Fi characteristic permits attackers to achieve entry to the router’s PIN. This exposes the router to potential unauthorized entry and manipulation.
Supply: RedFox
CVE-2024-36795: insecure permissions that enable attackers to entry URLs and directories embedded inside the router’s firmware. This heightens the chance of unauthorized community entry and management.
For the reason that router has reached EoL, Netgear is just not anticipated to launch security updates for the vulnerabilities. If changing the gadget is just not an choice in the meanwhile, customers are strongly suggested to use mitigatations that might assist forestall assaults:
- Flip off distant administration options to cut back the chance of unauthorized entry.
- Use advanced, lengthy passwords and alter them repeatedly.
- Separate the router from vital methods inside the community to restrict the impression of any potential breach.
- Make sure the router makes use of HTTPS and use browser settings that implement HTTPS to safe all communications and defend towards interception.
- Flip off WPS to stop attackers from exploiting this characteristic and gaining unauthorized entry.
- Swap to WPA3 for enhanced security over older protocols.
- Prohibit entry to the router’s administrative interface.
Nonetheless, customers that also depend on Netgear WNR614 ought to think about changing it with a mannequin that’s actively supported by its producer and gives higher security.




