Luxurious retailer Neiman Marcus confirmed it suffered a data breach after hackers tried to promote the corporate’s database stolen in latest Snowflake information theft assaults.
In a data breach notification filed with the Workplace of the Maine Lawyer Basic, the corporate says that the breach impacted 64,472 individuals.
“In Might 2024, we discovered that, between April and Might 2024, an unauthorized third celebration gained entry to a database platform utilized by Neiman Marcus Group. Based mostly on our investigation, the unauthorized third celebration obtained sure private data saved within the database platform,” warns Neiman Marcus in a data breach notification.
“The forms of private data affected assorted by particular person, and included data corresponding to title, contact data, date of beginning, and Neiman Marcus or Bergdorf Goodman present card quantity(s) (with out present card PINs).”
Neiman Marcus stated they disabled entry to the database platform when the breach was detected, investigated with cybersecurity specialists, and notified regulation enforcement.
Whereas present card numbers for Neiman Marcus and Bergdorf Goodman have been uncovered within the breach, the info didn’t embrace PINs, so the present playing cards ought to nonetheless be legitimate.
In a press release to BleepingComputer, Neiman Marcus confirmed that the info was stolen from their Snowflake account.
“Neiman Marcus Group (NMG) just lately discovered that an unauthorized celebration gained entry to a cloud database platform utilized by NMG that’s supplied by a 3rd celebration, Snowflake,” the Neiman Marcus Group informed BleepingComputer.
Linked to Snowflake information theft assaults
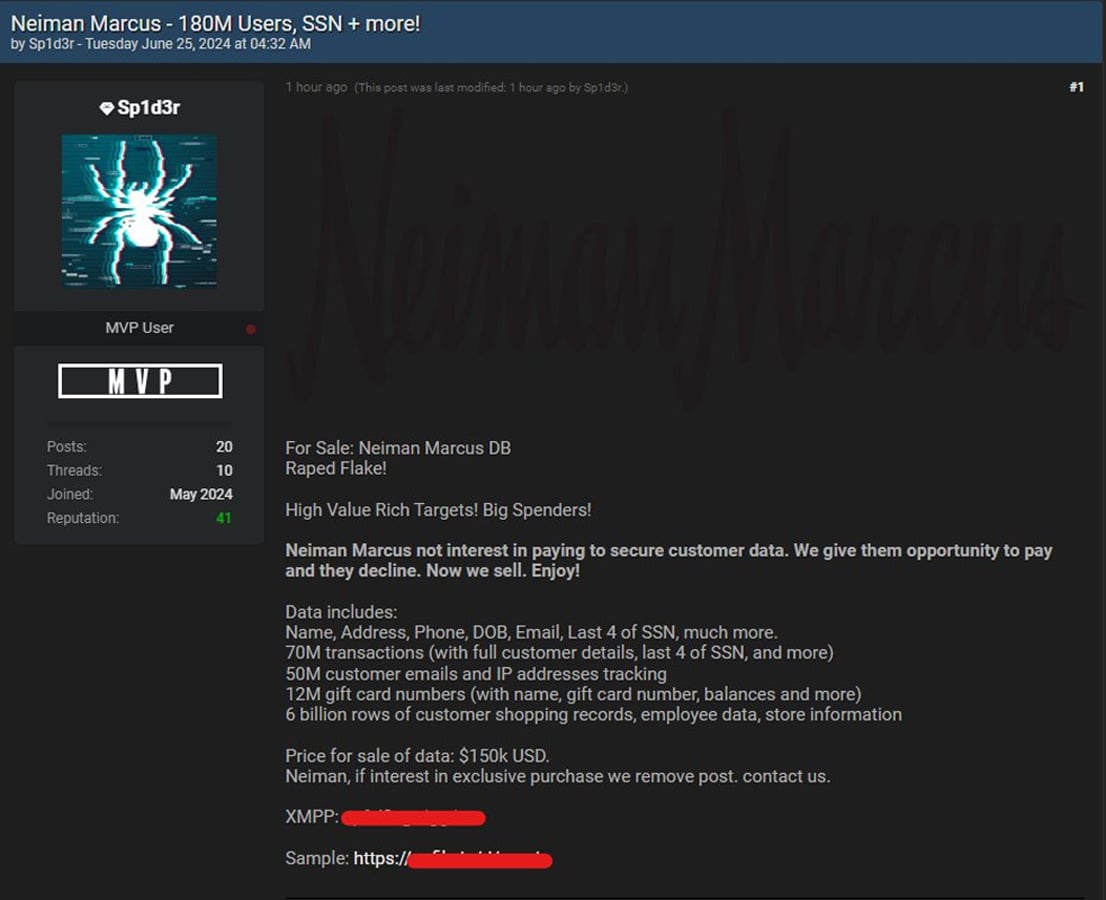
The data breach notifications come after a menace actor named “Sp1d3r” put Neiman Marcus’ information up on the market on a hacking discussion board for $150,000, as first shared by HackManac.
This menace actor is behind the sale of information for quite a few corporations breached within the latest Snowflake information theft assaults.
Whereas the menace actor didn’t point out Snowflake within the put up, they included “Raped Flake,”, which is in reference to a customized software of the identical title the menace actors created to steal information from the database platform.
Supply: HacManac
In response to the menace actor, the stolen information included what Neiman Marcus shared, plus the final 4 digits of social security numbers, buyer transactions, buyer emails, procuring information, worker information, and hundreds of thousands of present card numbers.
The menace actor claims to have tried to extort the corporate earlier than the discussion board posting, stating that the corporate refused to pay an extortion demand.
Nonetheless, quickly after the put up was made on the discussion board, it was subsequently taken down together with the info pattern, indicating that the corporate might have begun negotiating with the menace actors.
165 orgs seemingly impacted by Snowflake assaults
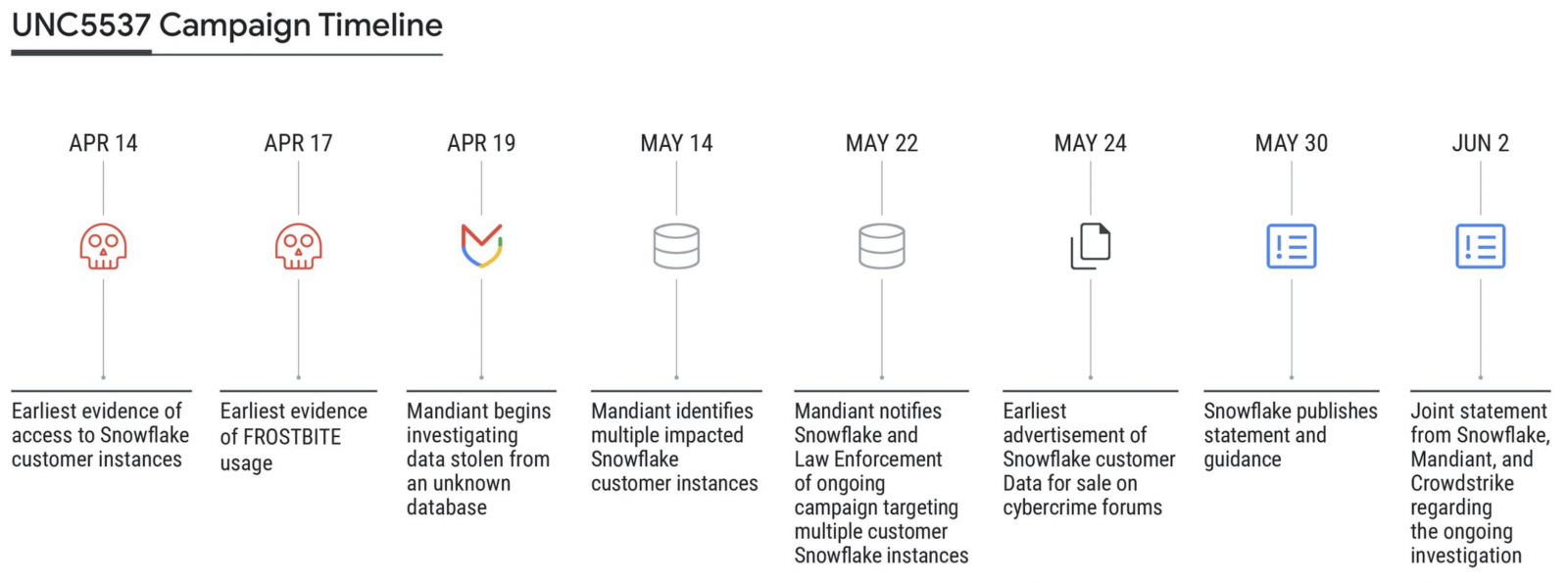
A joint investigation by SnowFlake, Mandiant, and CrowdStrike revealed {that a} menace actor, tracked as UNC5537, used stolen buyer credentials to focus on at the least 165 organizations that had not configured multi-factor authentication safety on their accounts.
Mandiant additionally linked the Snowflake assaults to a financially motivated menace actor tracked as UNC5537 since Might 2024. This menace actor is understood for breaching organizations, stealing information, and trying to extort corporations into paying a ransom for the info to not be printed or leaked to different menace actors.
Whereas Mandiant has not publicly disclosed a lot details about UNC5537, BleepingComputer has discovered they’re a part of a group of menace actors who ceaselessly go to the identical web sites, Telegram and Discord servers.
To breach Snowflake accounts, the menace actor used credentials stolen by information-stealing malware infections courting again to 2020.
“The impacted accounts weren’t configured with multi-factor authentication enabled, that means profitable authentication solely required a legitimate username and password,” Mandiant stated.
“Credentials recognized in infostealer malware output have been nonetheless legitimate, in some instances years after they have been stolen, and had not been rotated or up to date. The impacted Snowflake buyer cases didn’t have community permit lists in place to solely permit entry from trusted areas.”
Supply: Mandiant
Snowflake and Mandiant have already notified round 165 organizations doubtlessly uncovered to those ongoing assaults.
Current breaches linked to those assaults embrace Santander, Ticketmaster, QuoteWizard/LendingTree, Advance Auto Components, Los Angeles Unified, and Pure Storage.




