The U.S. Cybersecurity and Infrastructure Safety Company (CISA) has revealed analysis wanting into 172 key open-source initiatives and whether or not they’re inclined to reminiscence flaws.
The report, cosigned by CISA, the Federal Bureau of Investigation (FBI), in addition to Australian (ASD, ACSC) and Canadian organizations (CCCS), is a follow-up to the ‘Case for Reminiscence Secure Roadmaps’ launched in December 2023, geared toward elevating consciousness in regards to the significance of memory-safe code.
Reminiscence security
Reminiscence-safe languages are programming languages designed to forestall frequent memory-related errors resembling buffer overflows, use-after-free, and different sorts of reminiscence corruption.
They obtain this by managing reminiscence robotically as an alternative of counting on the programmer to implement protected reminiscence allocation and deallocation mechanisms.
A contemporary instance of a protected language system is Rust’s borrow checker, which eliminates information races. Different languages like Golang, Java, C#, and Python handle reminiscence by way of rubbish assortment, robotically reclaiming freed reminiscence to forestall exploitation.
Reminiscence-unsafe languages are these that don’t present built-in reminiscence administration mechanisms, burdening the developer with this accountability and rising the probability of errors. Examples of such circumstances are C, C++, Goal-C, Meeting, Cython, and D.
Extensively used open-source code unsafe
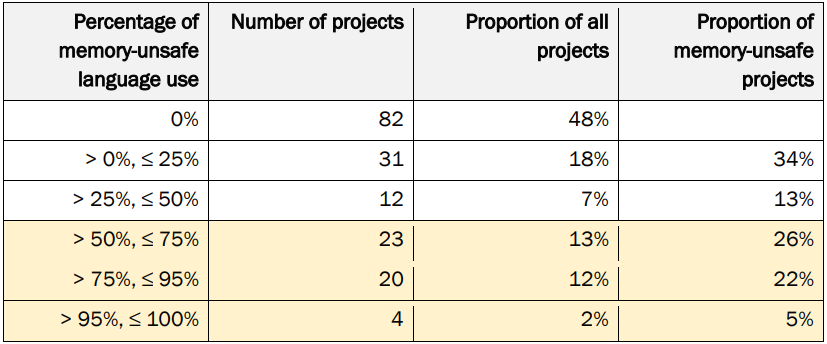
The report presents analysis analyzing 172 broadly deployed open-source initiatives, discovering that over half comprise memory-unsafe code.
Key findings introduced within the report are summarized as follows:
- 52% of essential open-source initiatives analyzed comprise code written in memory-unsafe languages.
- 55% of the overall traces of code (LoC) throughout these initiatives are written in memory-unsafe languages.
- The biggest initiatives are disproportionately written in memory-unsafe languages.
- Of the ten largest initiatives by whole LoC, every has a proportion of memory-unsafe LoC above 26%.
- The median proportion of memory-unsafe LoC in these giant initiatives is 62.5%, with 4 initiatives exceeding 94%.
- Even initiatives written in memory-safe languages usually rely upon elements written in memory-unsafe languages.
Some notable examples from the examined set are Linux (unsafe code ratio 95%), Tor (unsafe code ratio 93%), Chromium (unsafe ratio 51%), MySQL Server (unsafe ratio 84%), glibc (ratio 85%), Redis (ratio 85%), SystemD (65%), and Electron (47%).
Supply: CISA
CISA explains that software program builders face a number of challenges that always oblige them to make use of memory-unsafe languages, resembling useful resource constraints and efficiency necessities.
That’s very true when implementing low-level functionalities like networking, cryptography, and working system features.
“We noticed that many essential open supply initiatives are partially written in memory-unsafe languages and restricted dependency evaluation signifies that initiatives inherit code written in memory-unsafe languages by way of dependencies,” explains CISA within the report.
“The place efficiency and useful resource constraints are essential components, we have now seen, and count on the continued use of, memory-unsafe languages.”
The company additionally highlights the issue of builders disabling memory-safety options, both by error or on goal, to satisfy particular necessities, leading to dangers even when utilizing theoretically safer constructing blocks.
In the end, CISA recommends that software program builders write new code in memory-safe languages resembling Rust, Java, and GO and transition present initiatives, particularly essential elements, to these languages.
As well as, it is strongly recommended to comply with protected coding practices, rigorously handle and audit dependencies, and carry out steady testing, together with static evaluation, dynamic evaluation, and fuzz testing, to detect and deal with reminiscence questions of safety.




