Microsoft’s Visible Studio Code (VS Code) code editor and improvement surroundings incorporates a flaw that permits malicious extensions to retrieve authentication tokens saved in Home windows, Linux, and macOS credential managers.
These tokens are used for integrating with numerous third-party companies and APIs, reminiscent of Git, GitHub, and different coding platforms, so stealing them might have important penalties for a compromised group’s information security, doubtlessly resulting in unauthorized system entry, data breaches, and so forth.
The flaw was found by Cycode researchers, who reported it to Microsoft together with a working proof-of-concept (PoC) they developed. But, the tech big determined in opposition to fixing the problem, as extensions will not be anticipated to be sandboxed from the remainder of the surroundings.
Stealing secrets and techniques with extensions
The security drawback found by Cycode is attributable to a scarcity of isolation of authentication tokens in VS Code’s ‘Secret Storage,’ an API that permits extensions to retailer authentication tokens within the working system.
That is finished utilizing Keytar, VS Code’s wrapper for communication with the Home windows credential supervisor (on Home windows), keychain (on macOS), or keyring (for Linux).
Which means any extension operating in VS Code, even malicious ones, can acquire entry to the Secret Storage and abuse Keytar to retrieve any saved tokens.
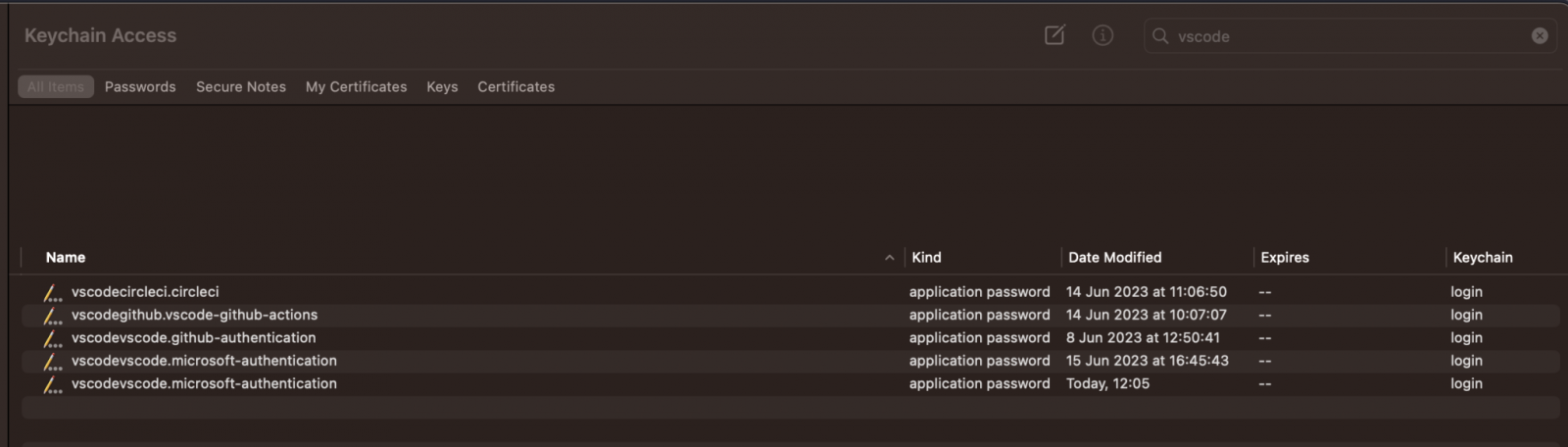
Cycode researcher Alex Ilgayev instructed BleepingComputer that aside from the built-in GitHub and Microsoft authentication, all the saved credentials from use of third-party extensions.
“Apart from the built-in Github/Microsoft authentication, all tokens saved in VSCode come from extensions,” Ilgayev instructed BleepingComputer.
“They’re both outlined by official extensions (from Microsoft), reminiscent of Git, Azure, Docker/Kubernetes, and so forth., or by third-party extensions, reminiscent of CircleCI, GitLab, AWS.”
Supply: Cycode
Upon discovering the issue, Cycode’s researchers began experimenting by making a malicious extension to steal tokens for CircleCI, a preferred coding platform with VS Code extensions. They did this by modifying CircleCI’s extension to run a command that might expose its safe token and even ship it straight to the researcher’s server.
Progressively, they developed a extra versatile assault technique to extract these secrets and techniques with out tampering with the goal extension’s code.
The important thing to this course of was discovering that any VS Code extension is allowed to entry the keychain as a result of it runs from throughout the utility that the working system has already granted entry to the keychain.
“We developed a proof-of-concept malicious extension that efficiently retrieved tokens not solely from different extensions but additionally from VS Code’s built-in login and sync performance for GitHub and Microsoft accounts, presenting a “Token Stealing” assault.” – Cycode.
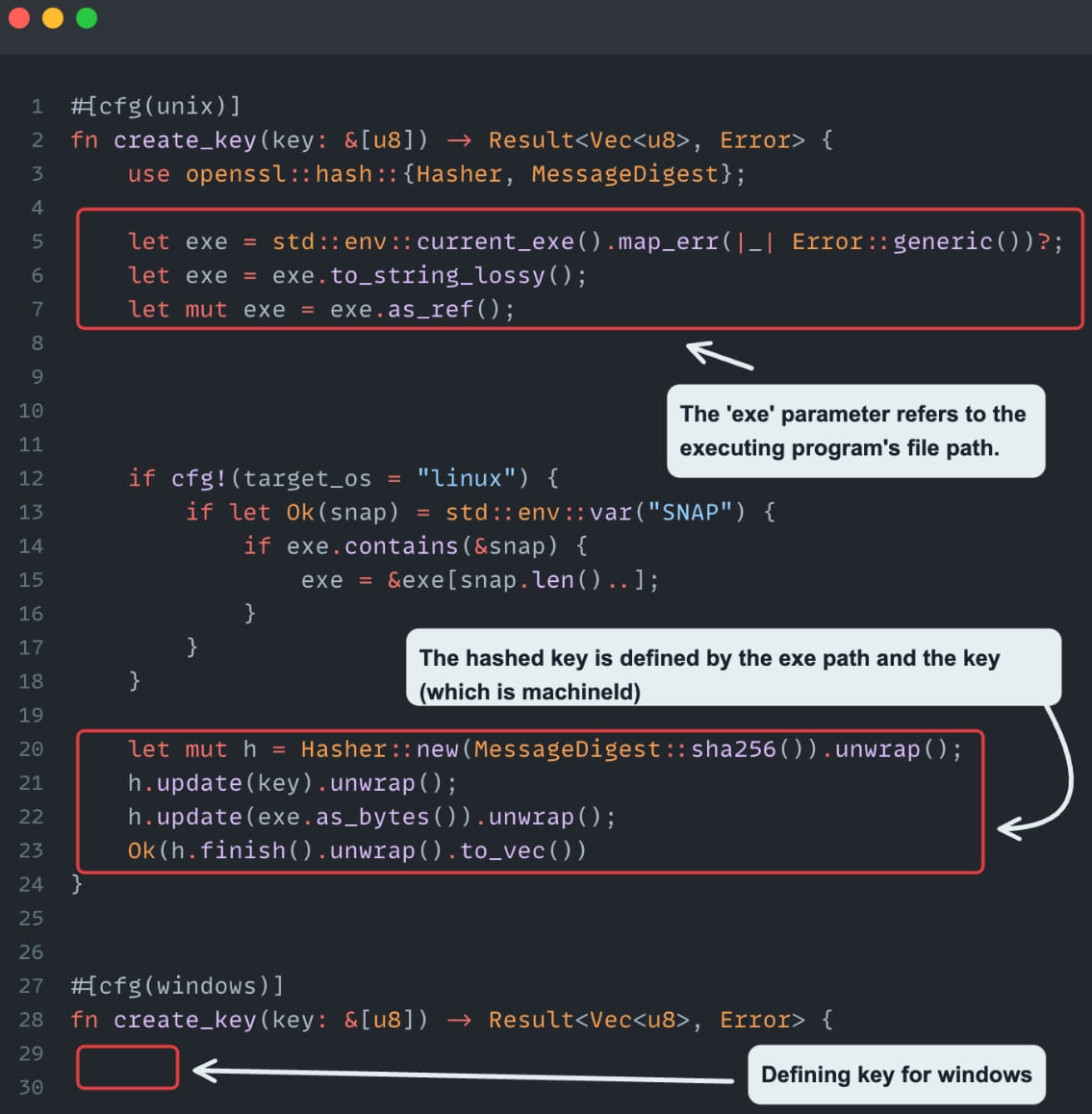
Subsequent, the retrieved tokens needed to be decrypted, and Cycode discovered that the algorithm used to encrypt tokens was AES-256-GCM, which is normally secure. Nonetheless, the important thing used to encrypt the tokens was derived from the present executable path and the machine ID, making it simple to recreate the important thing.
Supply: Cycode
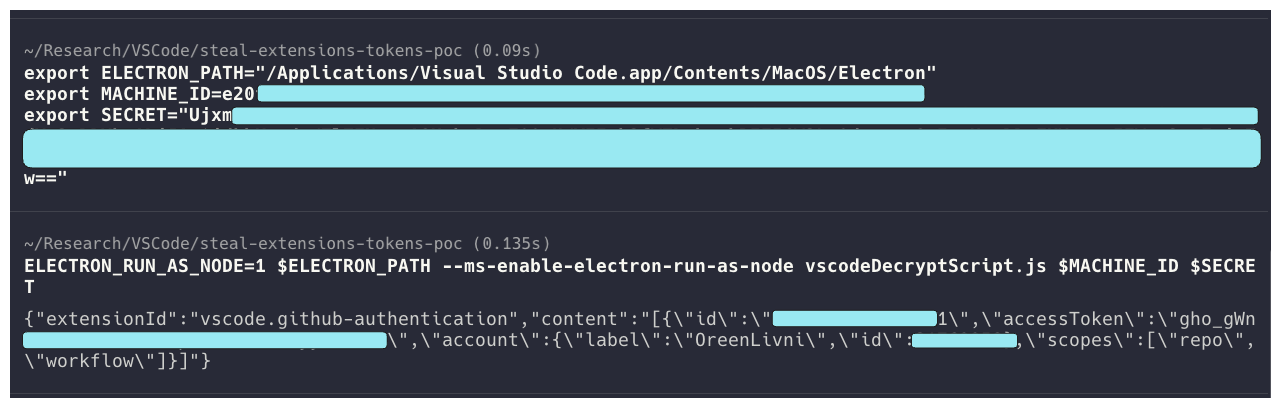
The retrieved tokens had been decrypted by a customized JS script run in VS Code’s Electron executable, deciphering and printing all passwords of regionally put in extensions.
Supply: Cycode
A second flaw found by Cycode’s researchers was that the ‘getFullKey’ perform retrieves secrets and techniques by a given ‘extensionId,’ which is derived from the extension’s identify and writer.
This drawback permits anybody to switch these fields and trick VS Code into granting them entry to a different extension’s safe tokens.
Cycode examined this utilizing a PoC extension that mimicked CircleCI once more; nonetheless, they famous that replicating some other extension and getting access to its secrets and techniques can be trivial.
Disclosure and (not) fixing
Cycode instructed BleepingComputer that they disclosed the issue to Microsoft two months in the past, even demonstrating their PoC extension and its capacity to steal saved extension tokens.
Regardless, Microsoft’s engineers did not see this as a security concern and determined to keep up the present design of VS Code’s secret storage administration framework.
Replace 8/14/23: Microsoft shared the next assertion about this subject, which is shared in its entirety under.
“This state of affairs depends on a consumer to obtain a malicious extension which might compromise their machine previous to performing the described assault. Extensions execute on the consumer machine below the identical privileges because the software program program itself and there’s no sandboxing for extensions. To assist preserve prospects secure and guarded, we scan extensions for viruses and malware earlier than they’re uploaded to the Market, and we verify that an extension has a Market certificates and verifiable signature previous to being put in. To assist make knowledgeable selections, we suggest customers use extensions from publishers they belief and evaluation data reminiscent of area verification, rankings, and suggestions to stop undesirable downloads.” – a Microsoft spokesperson




