4 vulnerabilities, certainly one of which is rated important, have been found within the Perforce Helix Core Server, a supply code administration platform extensively utilized by the gaming, authorities, navy, and expertise sectors.
Microsoft analysts found the issues throughout a security evaluation of the product, which the corporate’s sport growth studios use, and responsibly reported them to Perforce in late August 2023.
Though Microsoft says it has not noticed any exploitation makes an attempt of the found vulnerabilities within the wild, customers of the product are really helpful to improve to model 2023.1/2513900, launched on November 7, 2023, to mitigate the danger.
The Perforce Helix Core vulnerabilities
The 4 flaws found by Microsoft primarily contain denial of service (DoS) points, with probably the most extreme permitting arbitrary distant code execution as LocalSystem by unauthenticated attackers.
The vulnerabilities are summarized as follows:
- CVE-2023-5759 (CVSS rating 7.5): Unauthenticated (DoS) through RPC header abuse.
- CVE-2023-45849 (CVSS rating 9.8): Unauthenticated distant code execution as LocalSystem.
- CVE-2023-35767 (CVSS rating 7.5): Unauthenticated DoS through distant command.
- CVE-2023-45319 (CVSS rating 7.5): Unauthenticated DoS through distant command.
Probably the most harmful flaw of the set, CVE-2023-45849, permits unauthenticated attackers to execute code from ‘LocalSystem,’ a high-privileged Home windows OS account reserved for system capabilities. This account stage can entry native assets and system information, modify registry settings, and extra.
The vulnerability arises from the server’s mishandling of the user-bgtask RPC command. In its default configuration, Perforce Server permits unauthenticated attackers to remotely execute arbitrary instructions, together with PowerShell scripts, as LocalSystem.
By leveraging CVE-2023-45849, attackers might set up backdoors, entry delicate info, create or modify system settings, and probably take full management of the system operating a weak model of Perforce Server.
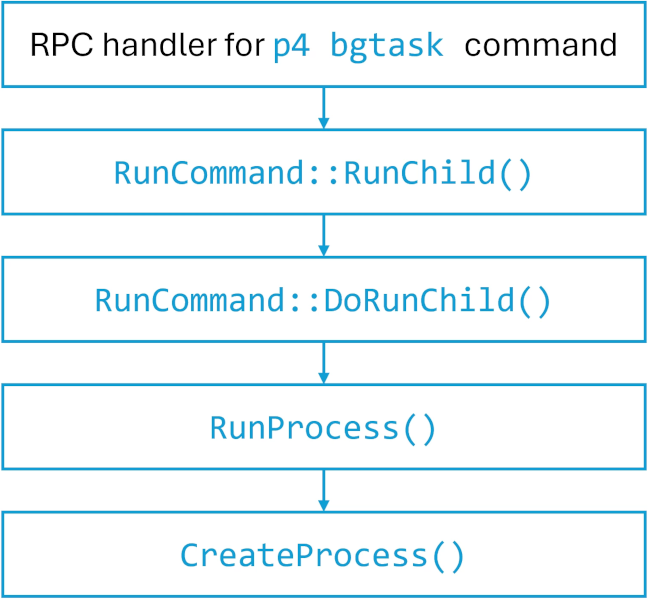
The remaining three vulnerabilities are much less extreme, permitting denial of service assaults, however can nonetheless trigger operational disruption that would translate to important monetary losses in large-scale deployments.
Safety suggestions
Other than downloading the most recent model of Helix Core from the seller’s obtain portal, Microsoft proposes taking the next steps:
- Recurrently replace third-party software program.
- Limit entry utilizing VPN or IP allow-list.
- Use TLS certificates with a proxy for consumer validation.
- Log all entry to the Perforce Server.
- Arrange crash alerts for IT and security groups.
- Use community segmentation to include breaches.
It’s also really helpful to observe the ideas supplied on this official security information.




