Match Group, the proprietor of a number of well-liked on-line courting providers, Tinder, Match.com, Meetic, OkCupid, and Hinge, confirmed a cybersecurity incident that compromised consumer information.
The corporate acknowledged that hackers stole a “restricted quantity of consumer information” after the ShinyHunters risk group leaked 1.7 GB of compressed information allegedly containing 10 million data of Hinge, Match, and OkCupid consumer info, in addition to inner paperwork.
In a press release to BleepingComputer, a spokesperson for Match Group confirmed the incident.

“We’re conscious of claims being made on-line associated to a not too long ago recognized security incident,” the corporate spokesperson mentioned.
“Match Group takes the protection and security of our customers significantly and acted shortly to terminate the unauthorized entry.”
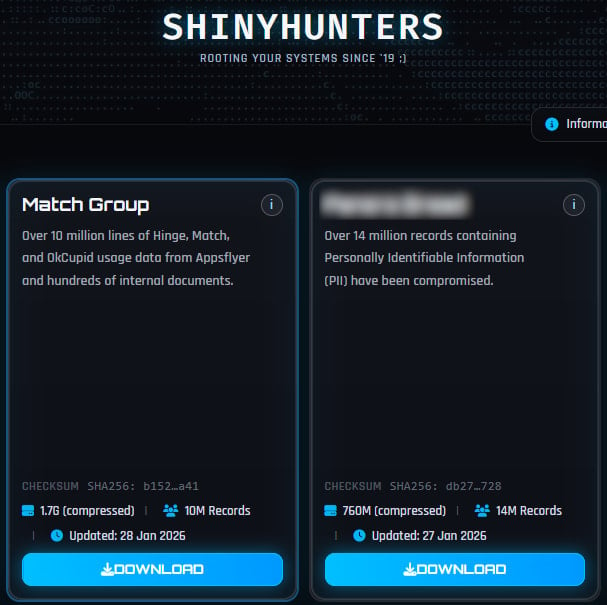
Supply: BleepingComputer
The corporate mentioned the investigation into the incident is in progress with the assistance of exterior consultants, and that there’s no indication that the hackers accessed consumer log-in credentials, monetary info, or non-public communications.
“We imagine the incident impacts a restricted quantity of consumer information, and we’re already within the means of notifying people, as applicable,” Match Group says.
Match Group is a huge in on-line courting, producing annual income of $3.5 billion, and the energetic consumer base throughout all its apps is estimated to be greater than 80 million.
This newest incident is a part of a brand new ShinyHunters voice phishing (vishing) marketing campaign focusing on single sign-on (SSO) accounts at Okta, Microsoft, and Google throughout over 100 high-value organizations, utilizing hyperlinks to supposedly inner login portals.
Within the case of Match Group, BleepingComputer was instructed that the attacker stole information after compromising an Okta SSO account that gave them entry to the corporate’s AppsFlyer advertising and marketing analytics occasion and Google Drive and Dropbox cloud storage accounts.
BleepingComputer has realized that the social engineering assault used the phishing area at ‘matchinternal.com.’
The hackers mentioned that the info comprises personally identifiable info (PII), however not plenty of it. and that almost all of it consists of monitoring info.
Corporations can add defenses towards assaults primarily based on social-engineering by implementing options which are proof against phishing makes an attempt.
“Whereas this isn’t the results of a security vulnerability in distributors’ merchandise or infrastructure, we strongly suggest shifting towards phishing-resistant MFA, equivalent to FIDO2 security keys or passkeys the place attainable, as these protections are proof against social engineering assaults in ways in which push-based or SMS authentication aren’t,” Charles Carmakal, Mandiant’s Chief Expertise Officer, says.
Moreover, “directors must also implement strict app authorization insurance policies and monitor logs for anomalous API exercise or unauthorized gadget enrollments.”
In a publish final week, Okta additionally recommends phishing resistance to stop entry to assets.”When utilizing Okta for workforce authentication, that might equate to enrolling customers in Okta FastPass, passkeys or each for the sake of redundancy,” says Moussa Diallo, risk researcher at Okta Menace Intelligence.
“Social engineering actors can be pissed off by setting community zones or tenant entry management lists that deny entry through the anonymizing providers favoured by risk actors. The secret’s to know the place your professional requests come from, and allowlist these networks,” Diallo mentioned.
The researcher notes that there are some monetary establishments, like Monzo Financial institution and the Crypto trade, at present testing reside caller checks, the place customers can confirm within the official cell app from the corporate if a certified consultant is on the telephone with them.

Whether or not you are cleansing up outdated keys or setting guardrails for AI-generated code, this information helps your crew construct securely from the beginning.
Get the cheat sheet and take the guesswork out of secrets and techniques administration.




