Readers assist help Home windows Report. While you make a purchase order utilizing hyperlinks on our website, we could earn an affiliate fee.
Learn the affiliate disclosure web page to seek out out how are you going to assist Home windows Report effortlessly and with out spending any cash. Learn extra
15 LATAM international locations have been focused in latest months by malware distribution campaigns that use Microsoft installers and Google Cloud Run to contaminate units with banking trojans that steal delicate data, comparable to banking credentials.
Whereas they’ve been initially focusing on LATAM international locations, these campaigns are actually spreading to a number of European international locations utilizing the identical technique: phishing emails containing Microsoft installer hyperlinks which can be distributed by means of Google Cloud Run, or Google Cloud storage bucket.
Cisco Talos, one of many largest cybersecurity firms on the planet, not too long ago launched a report detailing these malware distribution campaigns which embody the banking trojans comparable to Astaroth (aka Guildma), Mekotio, and Ousaban.
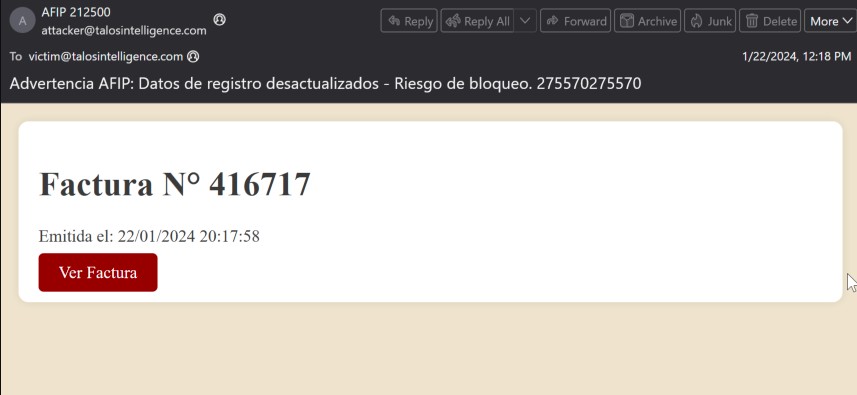
Victims normally obtain phishing emails containing corrupted hyperlinks that may simply compromise units as soon as accessed. These phishing emails make it appear as if they’re despatched by official establishments and will be simply mistaken if these focused should not paying consideration.
Usually, these emails are being despatched utilizing themes associated to invoices or monetary and tax paperwork, and generally pose as being despatched from the native authorities tax company within the nation being focused. Within the instance beneath, the e-mail purports to be from Administración Federal de Ingresos Públicos (AFIP), the native authorities tax company in Argentina, a rustic often focused by latest malspam campaigns.
Cisco Talos
The risk actors use a mix of Google Cloud Run and Microsoft installer instruments to ensure the malware reaches its targets, as Cisco explains:
When victims entry these hyperlinks, they’re redirected to the Cloud Run net companies deployed by the risk actors and delivered the parts essential to provoke the an infection course of. As beforehand acknowledged, we’ve got noticed Astaroth and Mekotio being distributed on this method within the type of malicious Microsoft Installers (MSI) recordsdata because the Stage 1 payload to start the an infection course of. We’ve noticed two latest variations in the way in which the MSI recordsdata are being delivered. In lots of circumstances, the MSI file is being delivered straight from the Google Cloud Run net service deployed by the adversary as proven within the case of Mekotio beneath.
Cisco Talos
In response to the cybersecurity firm, the risk actors have already infiltrated the European market, as a number of European establishments observed suspecting emails written in Spanish or Italian. These European establishments which can be affected by it, ought to take fast motion, and for good purpose too. Cisco says the Astaroth variant already triggered injury to over 300 establishments throughout 15 Latin American international locations.
Google and Microsoft haven’t launched any official statements on the matter, however Microsoft not too long ago up to date its Copilot for Safety to evaluate the brand new AI-based cyber threats which can be beginning to turn into widespread and environment friendly.
Nevertheless, the traditional phishing-based assaults are simply as harmful.
You possibly can learn the complete report right here.