A crew of researchers from UC Irvine and Tsinghua College has developed a brand new highly effective cache poisoning assault named ‘MaginotDNS,’ that targets Conditional DNS (CDNS) resolvers and might compromise complete TLDs top-level domains.
The assault is made attainable due to inconsistencies in implementing security checks in several DNS software program and server modes (recursive resolvers and forwarders), leaving roughly one-third of all CDNS servers weak.
The researchers offered the assault and paper earlier this week at Black Hat 2023, reporting that the recognized issues have now been remediated on the software program degree.
DNS cache poisoning background
DNS (Area Identify System) is a hierarchical and distributed naming system for web assets and networks, serving to resolve human-readable domains to numerical IP addresses so {that a} community connection could be made.
The DNS decision course of makes use of UDP, TCP, and DNSSEC to carry out queries and obtain responses. It may be iterative and recursive, involving a number of steps and exchanges with root servers, TLD servers, authoritative servers, caching data alongside the way in which, and many others.
The idea of DNS cache poisoning is injecting cast solutions into the DNS resolver cache, inflicting the server to direct customers who enter a website to incorrect IP addresses, probably main them to malicious web sites with out their data.
Many assaults of this kind have been demonstrated prior to now, like, for instance, the Kashpureff Attack in 1997, which exploited an absence of information verification (bailiwick guidelines), and the Kaminsky Attack in 2008 that took benefit of the absence of a supply port randomization system.
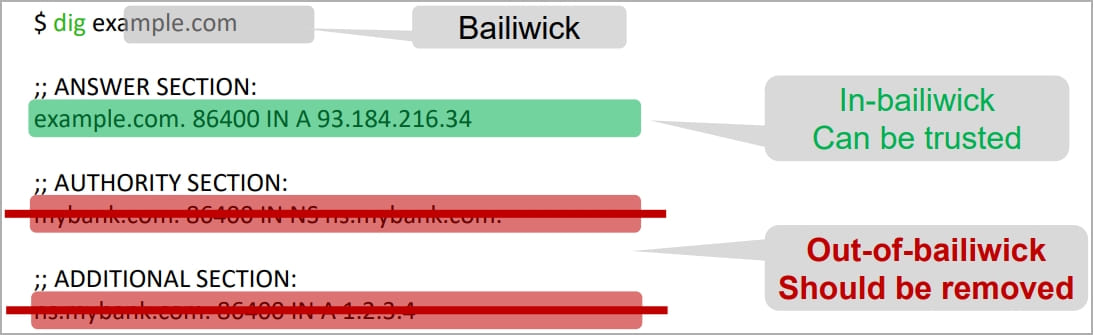
These assaults have been mitigated by including defenses into the resolvers’ implementation, rendering off-path assaults difficult.
Nonetheless, the ‘MaginotDNS’ assault can overcome these defenses by attacking the forwarding mode of CDNS from both on-path or off-path.
The MaginotDNS assault
CDNS resolvers help each recursive and forwarding question modes, utilized by ISPs and the enterprise to scale back prices and higher entry management.
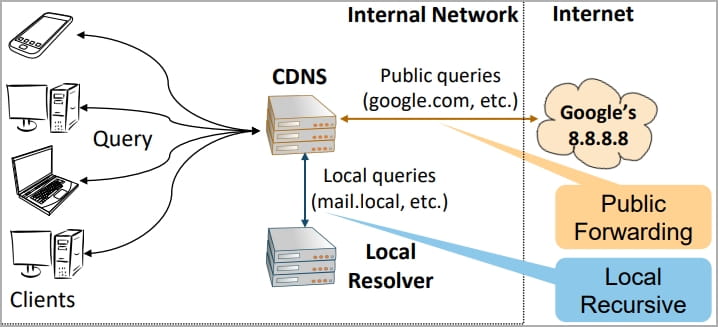
The researchers discovered that bailiwick checks are adequately enforced within the recursive mode; nevertheless, the forwarder is weak.
As a result of the 2 share the identical world DNS cache, an assault on the forwarder mode can open the trail to breaching the recursive mode, basically breaking the DNS cache safety boundary.
Researchers recognized inconsistencies within the bailiwick checking of outstanding DNS software program, together with BIND9 (CVE-2021-25220), Knot Resolver (CVE-2022-32983), Microsoft DNS, and Technitium (CVE-2021-43105).
In sure circumstances, they famous configurations that handled all data as in the event that they had been below the basis area, a extremely weak setup.
The examples showcased by the researchers throughout their BlackHat presentation embrace each on-path and off-path assaults, with the latter being the extra sophisticated but additionally much more useful for risk actors.
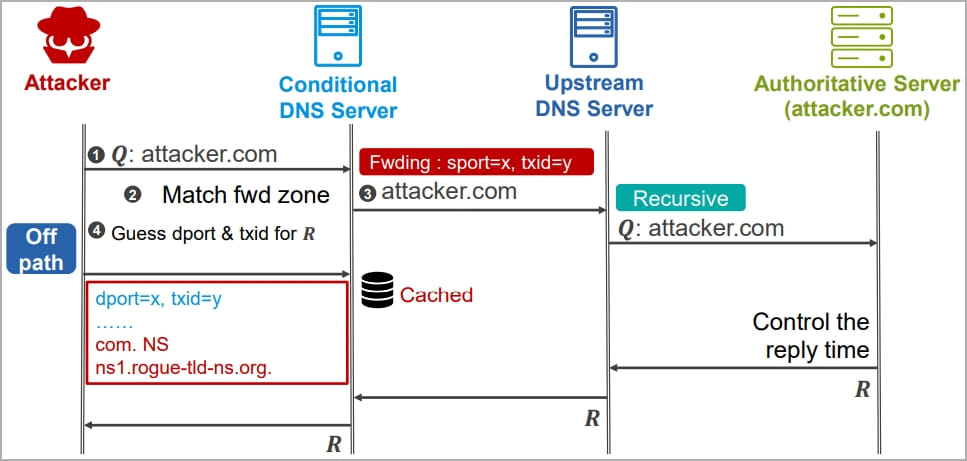
For these assaults, the risk actor must predict the supply port and the transaction ID utilized by the goal’s recursive DNS servers when producing a request after which use a malicious DNS server to ship cast responses with the proper parameters.
Inferring the supply port and guessing the transaction IDs could be performed by brute forcing or utilizing SADDNS (side-channel attacked DNS).
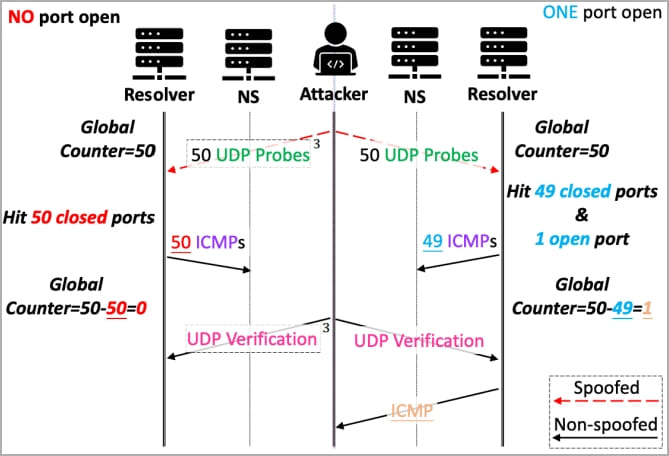
For BIND9, each parameters could be efficiently retrieved after 3,600 question rounds, whereas for Microsoft DNS, this drops to 720 rounds.
To extend the possibilities of success, the attacker should management the reply time of the malicious DNS responses to make sure their cast response reaches the sufferer’s server earlier than the legit one.
The researchers shared the next video demonstrating the MaginotDNS assault on Microsoft DNS.
Scanning for weak CDNS
The researchers scanned the web and located 1,200,000 DNS resolvers, of which 154,955 are CDNS servers.
Subsequent, utilizing software program fingerprints to establish weak variations, they discovered 54,949 weak CDNS servers, all of that are vulnerable to on-path assaults, and 88.3% are impacted by off-path assaults.
All of the affected software program distributors talked about above have confirmed and stuck the issues, and Microsoft has awarded a bounty to the researchers for his or her report.
Nonetheless, for the problems to be totally mitigated, CDNS directors should apply the patches and observe the proper configuration tips offered by the distributors.




