The LockBit ransomware gang has suffered a data breach after its darkish net affiliate panels have been defaced and changed with a message linking to a MySQL database dump.
The entire ransomware gang’s admin panels now state. “Do not do crime CRIME IS BAD xoxo from Prague,” with a hyperlink to obtain a “paneldb_dump.zip.”
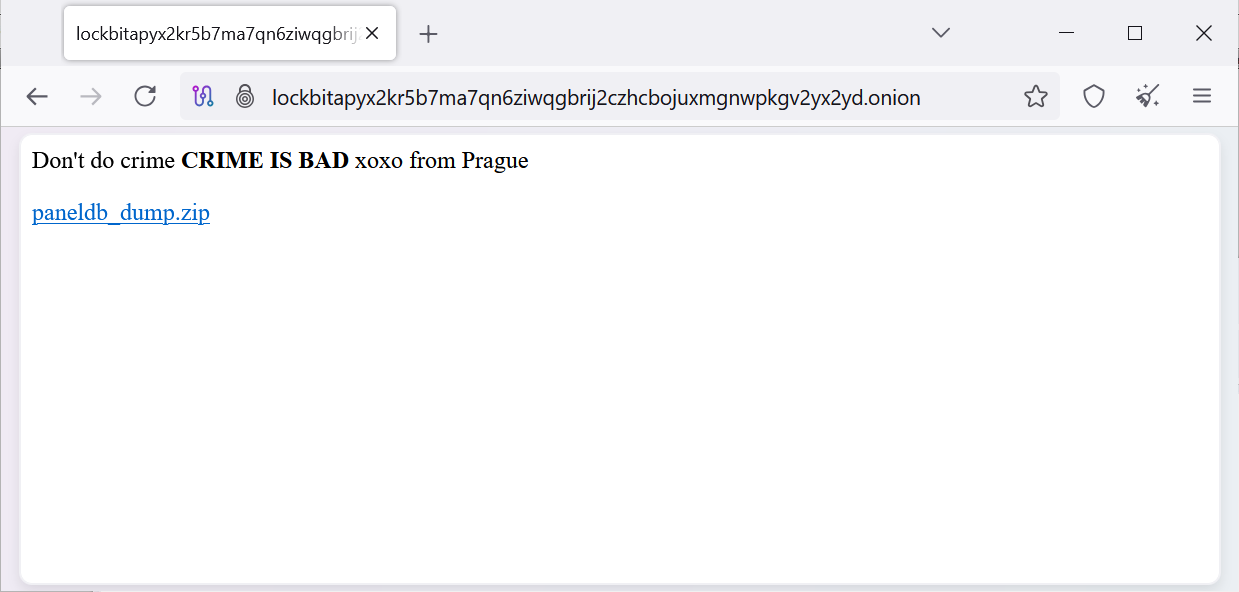
As first noticed by the risk actor, Rey, this archive comprises a SQL file dumped from the location affiliate panel’s MySQL database.
From evaluation by BleepingComputer, this database comprises twenty tables, with some extra attention-grabbing than others, together with:
- A ‘btc_addresses‘ desk that comprises 59,975 distinctive bitcoin addresses.
- A ‘builds‘ desk comprises the person builds created by associates for assaults. Desk rows comprise the general public keys, however no non-public keys, sadly. The focused firms’ names are additionally listed for a number of the builds.
- A ‘builds_configurations‘ desk comprises the completely different configurations used for every construct, resembling which ESXi servers to skip or information to encrypt.
- A ‘chats‘ desk could be very attention-grabbing because it comprises 4,442 negotiation messages between the ransomware operation and victims from December nineteenth to April twenty ninth.
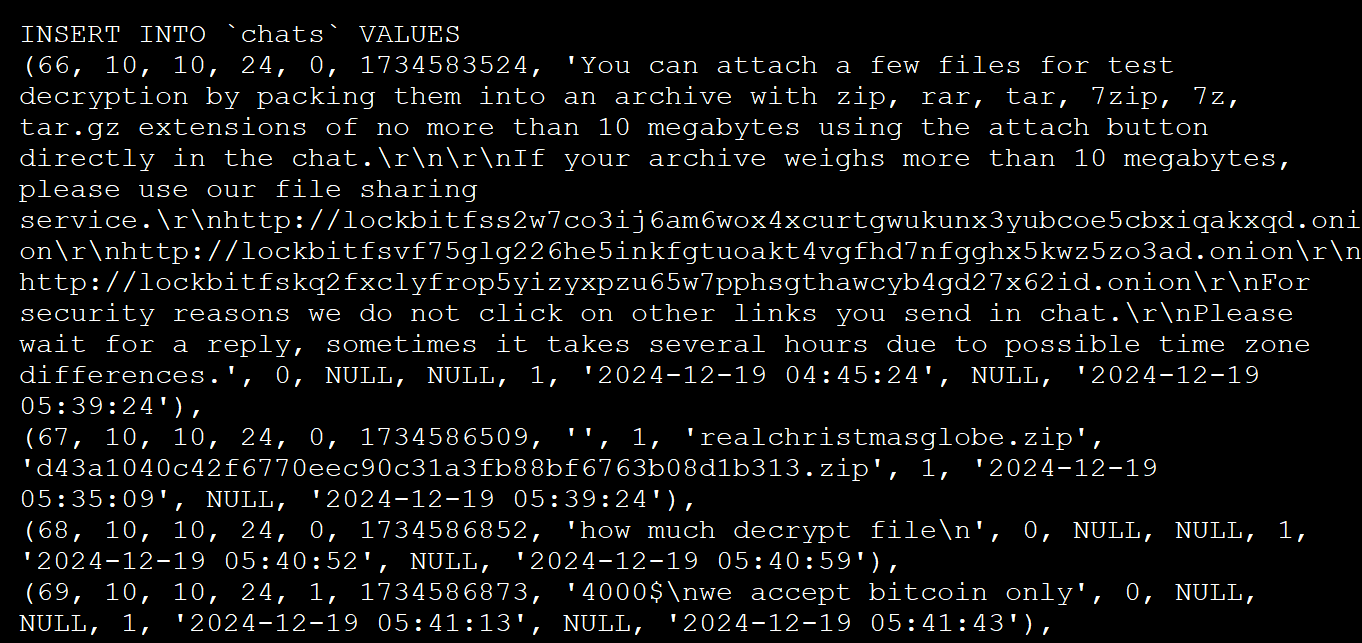
Affiliate panel ‘chats’ desk - A ‘customers‘ desk lists 75 admins and associates who had entry to the affiliate panel, with Michael Gillespie recognizing that passwords have been saved in plaintext. Examples of a number of the plaintext passwords are ‘Weekendlover69, ‘MovingBricks69420’, and ‘Lockbitproud231’.
In a Tox dialog with Rey, the LockBit operator generally known as ‘LockBitSupp’ confirmed the breach, stating that no non-public keys have been leaked or knowledge misplaced.
Based mostly on the MySQL dump technology time and the final date report within the negotiation chats desk , the database seems to have been dumped in some unspecified time in the future on April twenty ninth, 2025.
It is unclear who carried out the breach and the way it was achieved, however the defacement message matches the one utilized in a current breach of Everest ransomware’s darkish website, suggesting a attainable hyperlink.
Moreover, the phpMyAdmin SQL dump reveals that the server was working PHP 8.1.2, which is weak to important and actively exploited vulnerability tracked as CVE-2024-4577 that can be utilized to attain distant code execution on servers.
In 2024, a legislation enforcement operation known as Operation Cronos took down LockBit’s infrastructure, together with 34 servers internet hosting the info leak web site and its mirrors, knowledge stolen from the victims, cryptocurrency addresses, 1,000 decryption keys, and the affiliate panel.
Though LockBit managed to rebuild and resume operations after the takedown, this newest breach strikes an additional blow to its already broken repute.
It is too early to inform if this extra repute hit would be the last nail within the coffin for the ransomware gang.
Different ransomware teams who’ve skilled related leaks embrace Conti, Black Basta, and Everest.

Based mostly on an evaluation of 14M malicious actions, uncover the highest 10 MITRE ATT&CK strategies behind 93% of assaults and the way to defend in opposition to them.




