The Lockbit ransomware assaults use publicly out there exploits for the Citrix Bleed vulnerability (CVE-2023-4966) to breach the methods of huge organizations, steal information, and encrypt recordsdata.
Though Citrix made fixes out there for CVE-2023-4966 greater than a month in the past, 1000’s of internet-exposed endpoints are nonetheless operating weak home equipment, many within the U.S.
Excessive-profile Lockbit assaults
Menace researcher Kevin Beaumont has been monitoring assaults towards varied firms, together with the Industrial and Industrial Financial institution of China (ICBC), DP World, Allen & Overy, and Boeing, and located that they had one thing in frequent.
These are uncovered Citrix servers [1, 2] weak to the Citrix Bleed flaw, which he says the LockBit ransomware gang is exploiting assaults.
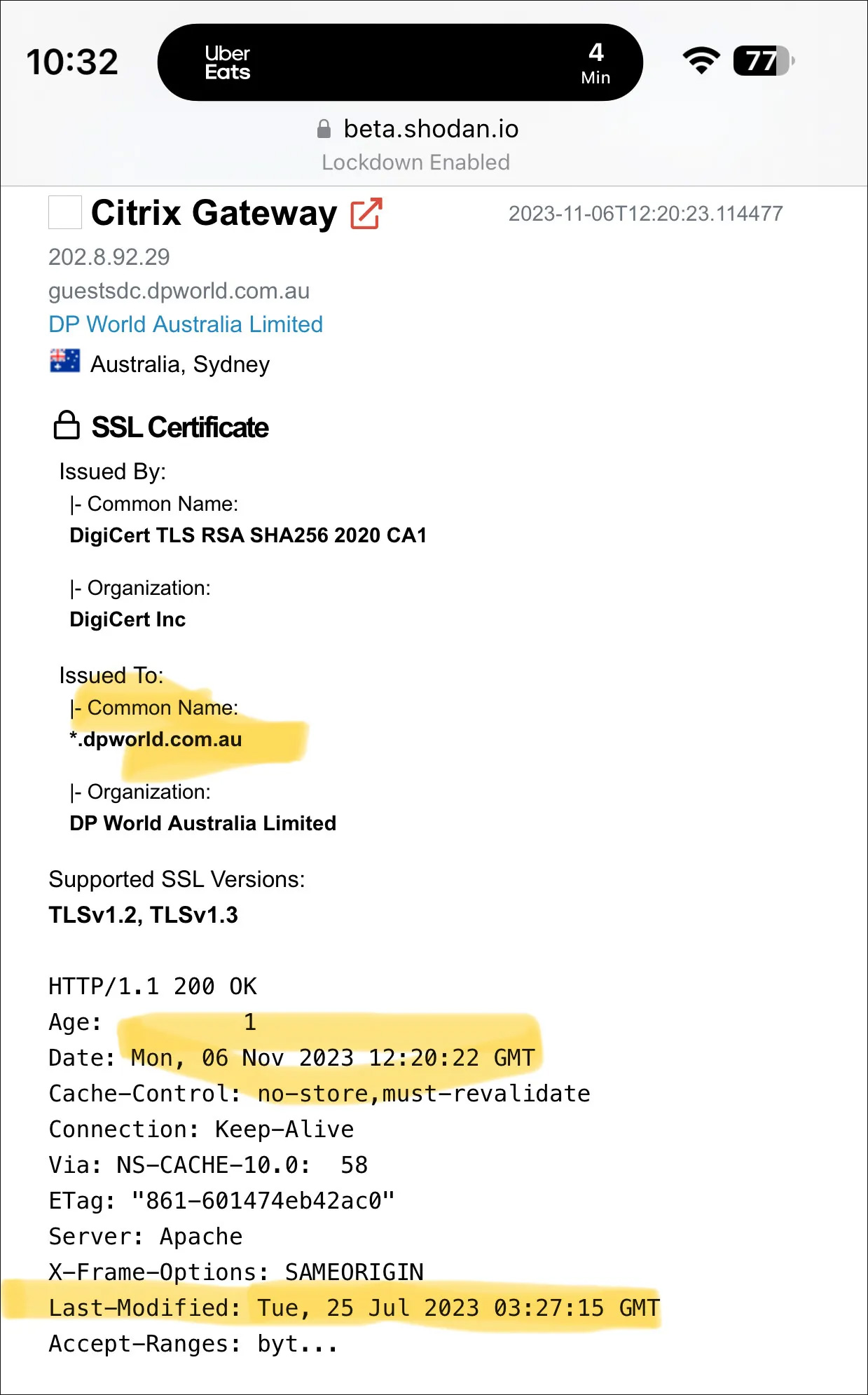
Supply: Kevin Beaumont
This was additional confirmed by the Wall Avenue Journal, which obtained an electronic mail from the U.S. Treasury despatched to pick monetary service suppliers, mentioning that LockBit was chargeable for the cyberattack on ICBC, which was achieved by exploiting the Citrix Bleed flaw.
If LockBit used the vulnerability to breach one firm, it’s believed they seemingly breached Boeing and DP World equally.
These assaults are seemingly being performed by a LockBit affiliate who’s closely using this vulnerability to breach networks moderately than the ransomware operation itself being behind the assault.
As LockBit is the biggest Ransomware-as-a-Service, it makes use of many associates who’ve full discretion on how they breach networks.
As we noticed with an affiliate who belonged to each the GandCrab after which REvil operations, it isn’t unusual for a hacker to concentrate on one specific trade or preliminary entry methodology.
For instance, a GandCrab/REvil affiliate specialised in exploiting MSP software program [1, 2, 3] to encrypt firms, and we’re seemingly seeing a LockBit affiliate using the Citrix Bleed flaw to mass-breach networks.
An enormous assault floor
On the time of writing, greater than 10,400 Citrix servers are weak to CVE-2023-4966, in response to findings from Japanese risk researcher Yutaka Sejiyama shared with BleepingComputer.
The vast majority of the servers, 3,133, are within the U.S., adopted by 1,228 in Germany, 733 in China, 558 within the U.Ok., 381 in Australia, 309 in Canada, 301 in France, 277 in Italy, 252 in Spain, 244 within the Netherlands, and 215 in Switzerland.
Sejiyama’s scans have revealed weak servers in giant and demanding organizations within the above and plenty of different nations, all of which stay unpatched over a full month following the general public disclosure of the vital flaw.
Citrix Bleed particulars
Citrix Bleed was disclosed on October 10 as a vital security subject that impacts Citrix NetScaler ADC and Gateway, enabling entry to delicate system data.
Mandiant reported that risk actors began exploiting Citrix Bleed in late August, when the security flaw was nonetheless a zero day. Within the assaults, hackers used HTTP GET requests to acquire Netscaler AAA session cookies after the multi-factor authentication stage (MFA).
Citrix urged admins to guard methods from this low-complexity, no-interaction assaults. On October 25, exterior assault floor administration firm AssetNote launched a proof-of-concept exploit demonstrating how session tokens will be stolen.




