Infostealer malware is without doubt one of the most substantial and underappreciated threat vectors for company data security groups. Infostealers infect computer systems, steal the entire credentials saved within the browser together with energetic session cookies and different information, then export it again to command and management (C2) infrastructure earlier than, in some circumstances, self-terminating.
This text will discover the methods wherein risk actors make the most of credentials to interrupt into privileged IT infrastructure to create data breaches and distribute ransomware.
Infostealers aren’t the one credential risk nevertheless. Leaked credentials from conventional sources are nonetheless a outstanding and substantial threat to organizations.
It comes as no shock that almost all customers reuse passwords throughout dozens of purposes, creating an ideal alternative for risk actors to brute pressure their approach into SaaS and on-premise purposes.
At Flare we at the moment monitor greater than forty million stealer logs, a quantity that’s rising by tens of millions each month and appears set to extend much more quickly in 2024. As well as, we monitor greater than 14 billion leaked credentials discovered from dumps throughout the darkish internet.
This provides us a singular perspective into how risk actors are buying, distributing, and utilizing leaked credentials.
Kinds of Leaked Credentials
To raised perceive leaked credentials it’s useful to “tier” them into classes primarily based on the tactic wherein they’re leaked, and the danger that they pose to the group.
Jason Haddix pioneered this strategy to allow security professionals to obviously talk the dangers related to credential leaks in a straightforward and consumable approach for managers and company executives.
Tier 1 Leaked Credentials
Tier 1 leaked credentials outcome from a third-party software/service breaches, and the entire customers of that service having their passwords compromised and distributed in an information dump on the darkish internet. That is what most individuals consider after they discuss “leaked credentials.”
For instance, let’s say the fictional company Scatterholt has person logins with lots of of hundreds of shopper logins. Attackers breach Scatterholt and entry the identification and entry administration system, then they steal these credentials and leak them onto the darkish internet.
It’s straightforward sufficient for Scatterholt company to pressure a password reset throughout all customers, however chances are high these customers have reused the identical password throughout many companies.
This leak permits risk actors to make use of brute forcing/pentesting instruments to aim to brute pressure credentials for hundreds of customers on different purposes that they might have used the identical password for.
Defending Towards Tier 1 Leaked Credentials
There are quite a few well-researched defenses that organizations can use to cut back threat. First and most significantly: monitor a leaked credentials database for company worker emails. This alone could make a large distinction as risk actors intentionally hunt down passwords related to company e-mail addresses to facilitate data breaches.
Secondly, require customers to routinely reset passwords on a time-schedule in order that if a particular password is breached, they’ll have already rotated different company credentials.
Lastly, we advocate using a password supervisor with a coverage that requires staff to randomize passwords to numerous purposes and retailer them with the supervisor, lowering the danger that staff will solely make small adjustments to passwords.
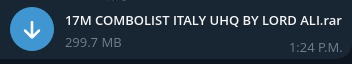
The Particular Case of Combolists
Combolists are usually composed of credential pairs which can be both organized by service, or geographically, that are then utilized by cybercriminals together with Brute Forcing instruments to aim to realize entry to numerous companies.
Supply: Flare
These credentials normally come from earlier identified breaches, or stealer logs, or typically completely made up; the unique supply isn’t completely clear, however the sheer quantity of credentials one can purchase by combolists mixed with frequent password reuse on the person’s half nonetheless makes them a substantial assault vector.
Tier 2
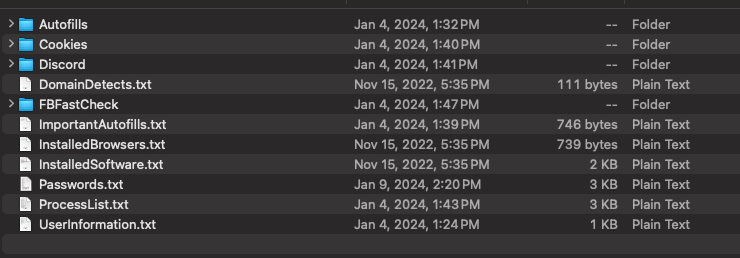
Tier 2 leaked credentials pose a particular diploma of threat to firms. These are credentials harvested immediately from the person by infostealer malware that steals all passwords saved within the browser.
We contemplate tier 2 leaked credentials to be of considerably elevated threat to each the corporate and the person for the next causes:
- A single stealer log will include all of the credentials the person saved of their browser. This creates an ideal alternative for risk actors to socially engineer the sufferer, the IT assist desk, and even the corporate utilizing the victims data.
- These logs include the plain textual content username, password, and host for the credentials, typically for lots of of various logins. Menace actors have an infinite benefit after they can see dozens of password variations that the person makes use of.
- These logs typically include kind fill information with solutions to secret questions which may be successfully used to bypass web sites with secret questions.
Supply: Flare
Tier 3 Leaked Credentials
This tier of leaks can also be from stealer logs, however pose excessive threat to the group. Contemporary stealer logs typically have energetic session cookies in them which may be simply utilized by actors for session hijacking assaults wherein they impersonate the sufferer and probably bypass 2FA and MFA controls.
Discovering a recent stealer log being distributed with company credentials ought to instantly immediate an incident investigation, as it’s extremely probably that the passwords are working and that actors may immediately entry company assets.
Supply: Flare
Defending Towards Tier 3 Leaked Credentials
The place attainable restrict TTL for company purposes to cut back the danger of session cookies nonetheless being legitimate if distributed on account of an infostealer an infection.
Multi-Issue Authentication isn’t a Silver Bullet
Should you aren’t monitoring for leaked credentials and also you probably have single-factor authentication for a lot of of your staff since a lot of them could have uncovered passwords.
Many individuals are beneath the impression that having two-factor authentication enabled is safety sufficient from stolen credentials, however the actuality, as we’ve witnessed many occasions over, is that risk actors are very acutely aware of the barrier 2FA imposes and have strategies and techniques to recover from the hurdle.
Whether or not by social engineering of staff, or utilizing 2FA bots to seize the one-time code/password from their victims, and even SIM-swapping, there’s a stunning quantity of the way to bypass multi-factor authentication controls which can be actively used within the wild.
The perfect protection towards these kinds of assaults function using authenticator apps, which function momentary rotating codes fairly than the one-time passwords customers could get through e-mail or SMS, as these purposes are normally rather more safe, and to a sure extent make sure the person in query has management of (normally) a second system.
Nervous about Credentials? Flare Can Assist
Flare screens greater than 14 billion leaked credentials distributed on the darkish internet and lots of of tens of millions leaked by infostealer malware.
Our platform units up in half-hour and gives strong detection for leaked worker credentials throughout lots of of boards, channels, and marketplaces.
Try our free trial.
Sponsored and written by Flare.




