North Korean risk actors generally known as the Lazarus Group exploited a flaw within the Home windows AppLocker driver (appid.sys) as a zero-day to realize kernel-level entry and switch off security instruments, permitting them to bypass noisy BYOVD (Carry Your Personal Weak Driver) methods.
This exercise was detected by Avast analysts, who promptly reported it to Microsoft, resulting in a repair for the flaw, now tracked as CVE-2024-21338, as a part of the February 2024 Patch Tuesday. Nonetheless, Microsoft has not marked the flaw as being exploited as a zero-day.
Avast studies that Lazarus exploited CVE-2024-21338 to create a learn/write kernel primitive in an up to date model of its FudModule rootkit, which ESET first documented in late 2022. Beforehand, the rootkit abused a Dell driver for BYOVD assaults.
The brand new model of FudModule options vital enhancements in stealth and performance, together with new and up to date methods for evading detection and turning off security protections like Microsoft Defender and CrowdStrike Falcon.
Furthermore, by retrieving many of the assault chain, Avast found a beforehand undocumented distant entry trojan (RAT) utilized by Lazarus, which the security agency promised to share extra particulars about at BlackHat Asia in April.
Lazarus 0-day exploitation
The malware exploited a vulnerability in Microsoft’s ‘appid.sys’ driver, a Home windows AppLocker part that gives utility whitelisting capabilities.
Lazarus exploits it by manipulating the Enter and Output Management (IOCTL) dispatcher within the appid.sys driver to name an arbitrary pointer, tricking the kernel into executing unsafe code, thus bypassing security checks.
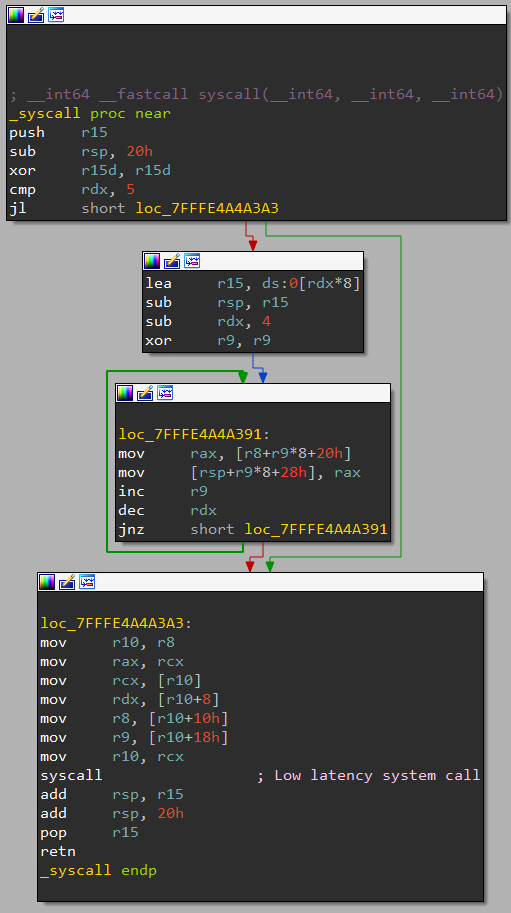
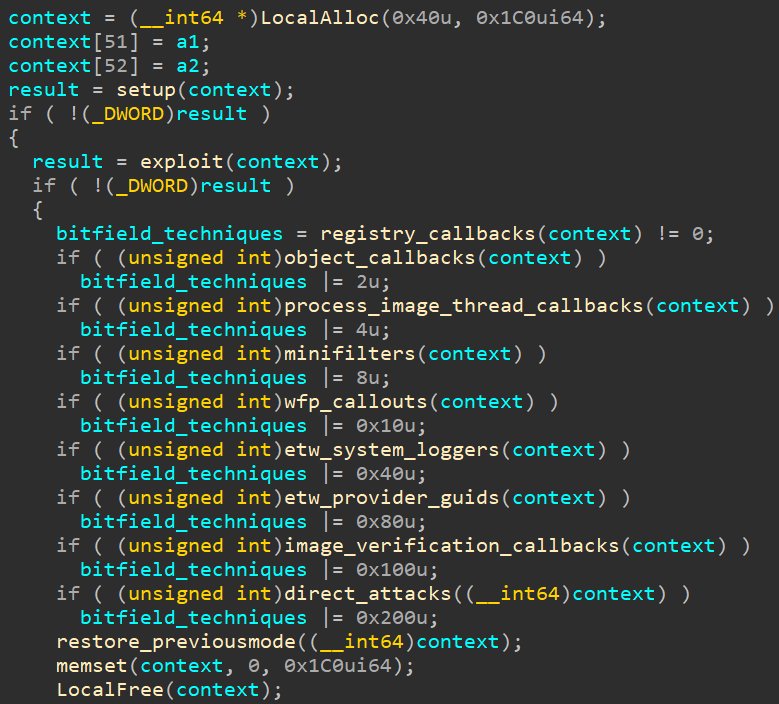
The FudModule rootkit, constructed throughout the identical module because the exploit, executes direct kernel object manipulation (DKOM) operations to show off security merchandise, cover malicious actions, and keep persistence on the breached system.
The focused security merchandise are AhnLab V3 Endpoint Safety, Home windows Defender, CrowdStrike Falcon, and the HitmanPro anti-malware resolution.
Avast noticed new stealth options and expanded capabilities within the new rootkit model, like the flexibility to suspect processes protected by Protected Course of Mild (PPL) by manipulating deal with desk entries, selective and focused disruption through DKOM, enhancements in tampering with Driver Signature Enforcement and Safe Boot, and extra.
Avast notes that this new exploit tactic marks a big evolution within the risk actor’s kernel entry capabilities, permitting them to launch stealthier assaults and persist on compromised techniques for longer durations.
The one efficient security measure is to use the February 2024 Patch Tuesday updates as quickly as attainable, as Lazarus’ exploitation of a Home windows built-in driver makes the assault significantly difficult to detect and cease.
YARA guidelines to assist defenders detect exercise linked to the newest model of the FudModule rootkit may be discovered right here.




