An Ivanti Join Safe and Ivanti Coverage Safe server-side request forgery (SSRF) vulnerability tracked as CVE-2024-21893 is at present beneath mass exploitation by a number of attackers.
Ivanti first warned in regards to the flaw within the gateway’s SAML elements on January 31, 2024, giving it a zero-day standing for restricted lively exploitation, impacting a small variety of prospects.
Exploitation of CVE-2024-21893 allowed attackers to bypass authentication and entry restricted assets on weak units (variations 9.x and 22.x).
Menace monitoring service Shadowserver is now seeing a number of attackers leveraging the SSRF bug, with 170 distinct IP addresses making an attempt to take advantage of the flaw.
The exploitation quantity of this explicit vulnerability is way larger than that of different lately mounted or mitigated Ivanti flaws, indicating a transparent shift within the attackers’ focus.
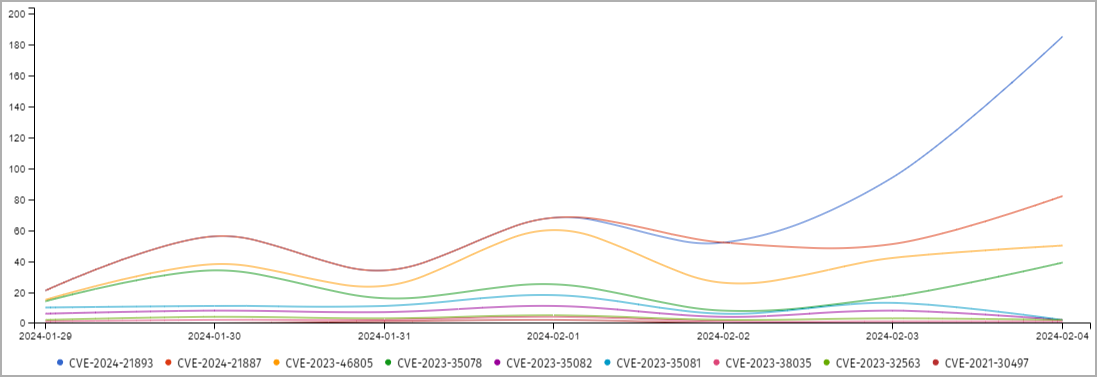
Though the proof-of-concept (PoC) exploit launched by Rapid7 researchers on February 2, 2024, has undoubtedly performed a task in aiding assaults, Shadowserver notes that they noticed attackers utilizing related strategies hours previous to the publication of the Rapid7 report.
Which means hackers had already found out leverage CVE-2024-21893 for unrestricted, unauthenticated entry to weak Ivanti endpoints.
In response to ShadowServer, there are at present virtually 22,500 Ivanti Join Safe units uncovered on the Web. Nonetheless, it’s unknown what number of are weak to this explicit vulnerability.
A security mess
The disclosure of CVE-2024-21893 got here together with the discharge of security updates for 2 different zero-days impacting the identical merchandise, CVE-2023-46805 and CVE-2024-21887, which Ivanti first found on January 10, 2024, sharing momentary mitigations.
These two flaws had been discovered to be exploited by Chinese language espionage menace group UTA0178/UNC5221 to put in webshells and backdoors on breached units. Infections from this marketing campaign peaked at round 1,700 in mid-January.
Regardless of preliminary mitigations, attackers bypassed defenses, compromising even the machine’s configuration information, main Ivanti to postpone its firmware patches, scheduled for January 22, to deal with the subtle menace.
Because of the state of affairs with lively exploitation of a number of crucial zero-day vulnerabilities, lack of efficient mitigations, and lack of security updates for a number of the impacted product variations, the U.S. Cybersecurity & Infrastructure Safety Company (CISA) has ordered federal businesses to disconnect all Ivanti Join Safe and Coverage Safe VPN home equipment.
Solely units which were manufacturing facility reset and upgraded to the most recent firmware model ought to be reconnected to the community. Nonetheless, older variations that stay impacted are nonetheless and not using a patch.
This instruction extends to non-public organizations, though it isn’t necessary. Subsequently, firms ought to severely contemplate the security standing of their Ivanti deployments and the belief of their atmosphere typically.