Two vulnerabilities affecting some model of Jupiter X Core, a premium plugin for organising WordPress and WooCommerce web sites, enable hijacking accounts and importing recordsdata with out authentication.
Jupiter X Core is an easy-to-use but highly effective visible editor, a part of the Jupiter X theme, which is utilized in over 172,000 web sites.
Rafie Muhammad, an analyst at WordPress security firm Patchstack, found the 2 essential vulnerabilities and reported them to ArtBee, the developer of Jupiter X Core, who addressed the problems earlier this month.
Flaw particulars
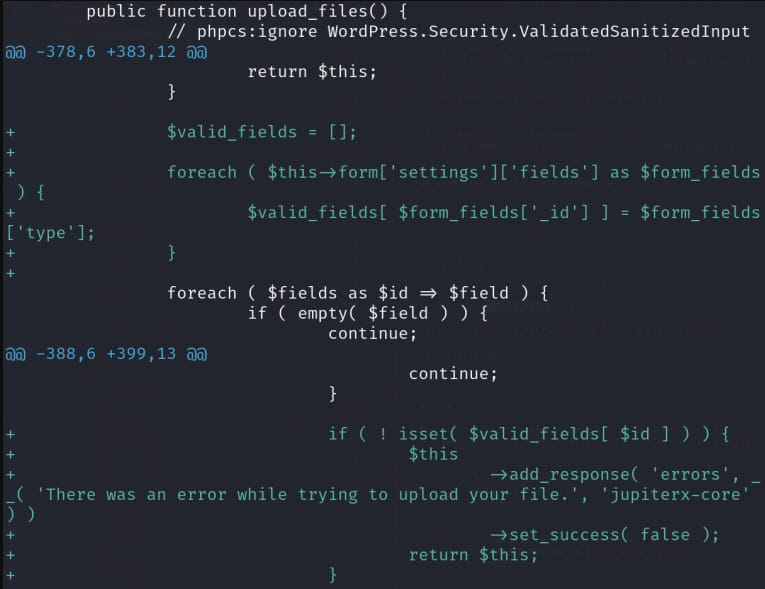
The primary vulnerability is recognized as CVE-2023-38388 and permits importing recordsdata with out authentication, which might result in executing arbitrary code on the server.
The security drawback has acquired a severity rating of 9.0 and impacts all JupiterX Core variations beginning 3.3.5 beneath. The developer fastened the issue in model 3.3.8 of the plugin.
CVE-2023-38388 might be exploited as a result of there aren’t any authentication checks throughout the plugin’s ‘upload_files’ operate, which might be known as from the frontend by anybody.
The seller’s patch provides a test for the operate and in addition prompts a second test to stop importing dangerous file varieties.
The second vulnerability, CVE-2023-38389, permits unauthenticated attackers to take management of any WordPress person account on the situation that they know the e-mail deal with. It acquired a essential severity score of 9.8 and impacts all variations of Jupiter X Core ranging from 3.3.8 and beneath.
ArtBees fastened the issue on August 9 by releasing model 3.4.3. All customers of the plugin are beneficial to replace the part to the newest launch.
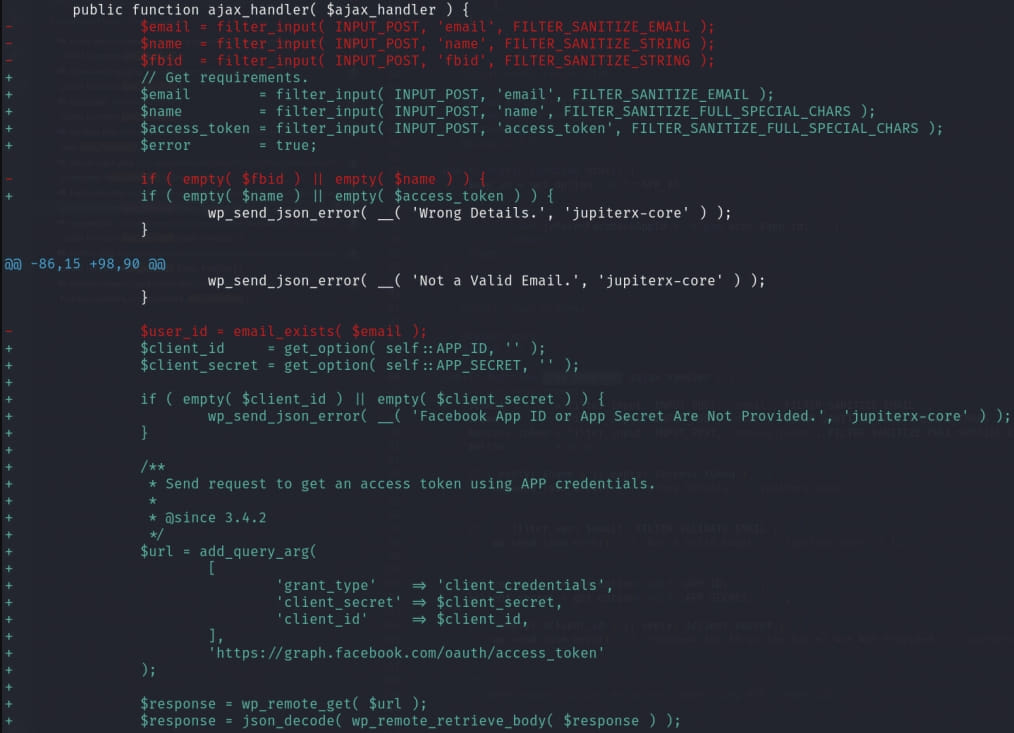
Rafie Muhammad explains that the underlying drawback was that the ‘ajax_handler’ operate within the Fb login technique of the plugin allowed an unauthenticated person to set any WordPress person’s ‘social-media-user-facebook-id’ meta with any worth by the ‘set_user_facebook_id’ operate.
As this meta worth is used for person authentication in WordPress, an attacker can abuse it to authenticate as any registered person on the location, together with directors, so long as they use the right electronic mail deal with.
ArtBees’ answer is to fetch the required electronic mail deal with and distinctive person ID straight from Fb’s authentication endpoint, making certain the legitimacy of the login course of.
Customers of the JupiterX Core plugin are beneficial to improve to model 3.4.3 as quickly as potential to mitigate the extreme dangers posed by the 2 vulnerabilities.
On the time of writing we couldn’t discover any public experiences in regards to the two vulnerabilities being exploited within the wild.




