Israeli greater schooling and tech sectors have been focused as a part of a collection of harmful cyber assaults that commenced in January 2023 with an intention to deploy beforehand undocumented wiper malware.
The intrusions, which occurred as just lately as October, have been attributed to an Iranian nation-state hacking crew it tracks underneath the title Agonizing Serpens, which is also referred to as Agrius, BlackShadow and Pink Sandstorm (beforehand Americium).
“The assaults are characterised by makes an attempt to steal delicate information, similar to personally identifiable info (PII) and mental property,” Palo Alto Networks Unit 42 mentioned in a brand new report shared with The Hacker Information.
“As soon as the attackers stole the knowledge, they deployed varied wipers supposed to cowl the attackers’ tracks and to render the contaminated endpoints unusable.”
This contains three completely different novel wipers similar to MultiLayer, PartialWasher, and BFG Agonizer, in addition to a bespoke instrument to extract info from database servers referred to as Sqlextractor.
Lively since no less than December 2020, Agonizing Serpens has been linked to wiper assaults focusing on Israeli entities. Earlier this Might, Examine Level detailed the menace actor’s use of a ransomware pressure referred to as Moneybird in its assaults focusing on the nation.
The newest set of assaults entails weaponizing weak web going through internet servers as preliminary entry routes to deploy internet shells and conduct reconnaissance of the sufferer networks and steal credentials of customers with administrative privileges.
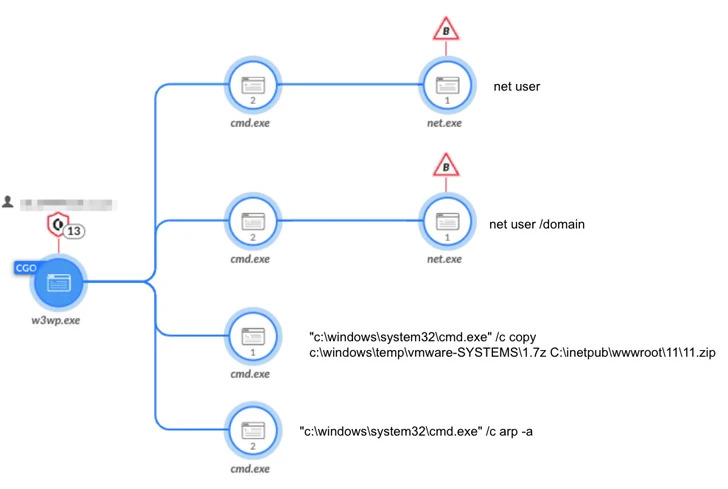
A lateral motion part is adopted by information exfiltration utilizing a mixture of public and customized instruments like Sqlextractor, WinSCP, and PuTTY, and at last ship the wiper malware –
- MultiLayer, a .NET malware that enumerates recordsdata for both deletion or corrupting them with random information to withstand restoration efforts and render the system unusable by wiping the boot sector.
- PartialWasher, a C++-based malware to scan drives and wipe specified folders and its subfolders.
- BFG Agonizer, a malware that closely depends on an open-source mission referred to as CRYLINE-v5.0.
The hyperlinks to Agrius stems from a number of code overlaps with different malware households like Apostle, IPsec Helper, and Fantasy, which have been recognized as beforehand utilized by the group.
“It seems that the Agonizing Serpens APT group has just lately upgraded their capabilities and they’re investing nice efforts and assets to try to bypass EDR and different security measures,” Unit 42 researchers mentioned.
“To take action, they’ve been rotating between utilizing completely different identified proof-of-concept (PoC) and pentesting instruments in addition to customized instruments.”




