The Operation Triangulation spyware and adware assaults focusing on iPhone units since 2019 leveraged undocumented options in Apple chips to bypass hardware-based security protections.
This discovering comes from Kaspersky analysts who’ve been reverse-engineering the advanced assault chain over the previous 12 months, attempting to unearth all particulars that underpin the marketing campaign they initially found in June 2023.
The invention and use of obscure {hardware} options doubtless reserved for debugging and manufacturing unit testing to launch spyware and adware assaults in opposition to iPhone customers recommend {that a} subtle menace actor performed the marketing campaign.
Furthermore, it constitutes a superb instance of why reliance on security by obscurity and the secrecy of {hardware} design or {hardware} testing implementation is a false premise.
Operation Triangulation
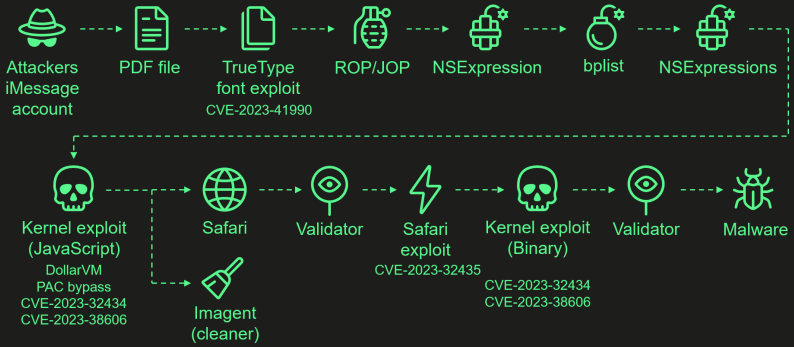
Operation Triangulation is a spyware and adware marketing campaign focusing on Apple iPhone units utilizing a sequence of 4 zero-day vulnerabilities. These vulnerabilities are chained collectively to create a zero-click exploit that permits attackers to raise privileges and carry out distant code execution.
The 4 flaws that represent the extremely subtle exploit chain and which labored on all iOS variations as much as iOS 16.2 are:
- CVE-2023-41990: A vulnerability within the ADJUST TrueType font instruction permitting distant code execution by a malicious iMessage attachment.
- CVE-2023-32434: An integer overflow subject in XNU’s reminiscence mapping syscalls, granting attackers intensive learn/write entry to the system’s bodily reminiscence.
- CVE-2023-32435: Used within the Safari exploit to execute shellcode as a part of the multi-stage assault.
- CVE-2023-38606: A vulnerability utilizing {hardware} MMIO registers to bypass the Web page Safety Layer (PPL), overriding hardware-based security protections.
The assaults begin with a malicious iMessage attachment despatched to the goal, whereas the whole chain is zero-click, which means it doesn’t require interplay from the consumer, and would not generate any noticeable indicators or traces.
Kaspersky found the assault inside its personal community, and Russia’s intelligence service (FSB) instantly accused Apple of offering the NSA with a backdoor in opposition to Russian authorities and embassy personnel.
To this point, the origin of the assaults stays unknown, and there was no proof of those allegations.
Apple fastened the then-recognized two zero-day flaws (CVE-2023-32434 and CVE-2023-32435) on June 21, 2023, with the discharge of iOS/iPadOS 16.5.1 and iOS/iPadOS 15.7.7.
Extremely subtle assaults
Of the above flaws, CVE-2023-38606, which was addressed on July 24, 2023, with the discharge of iOS/iPadOS 16.6, is probably the most intriguing for Kaspersky’s analysts.
Exploiting the flaw permits an attacker to bypass {hardware} safety on Apple chips that forestall attackers from acquiring full management over the system once they acquire learn and write entry to the kernel reminiscence, which was achieved utilizing the separate CVE-2023-32434 flaw.
Within the deep-dive technical writeup, Kaspersky explains that CVE-2023-38606 targets unknown MMIO (memory-mapped I/O) registers in Apple A12-A16 Bionic processors, doubtless linked to the chip’s GPU co-processor, that are not listed within the DeviceTree.
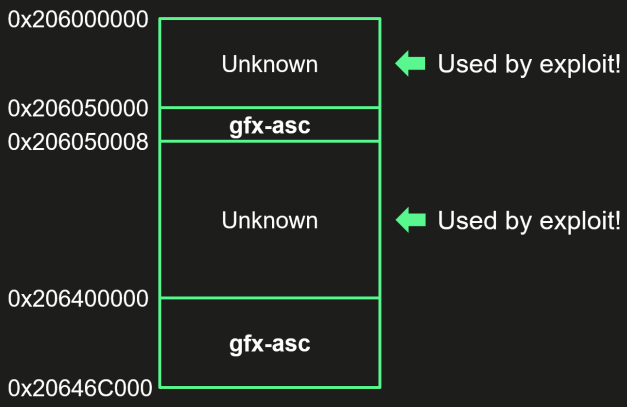
Operation Triangulation makes use of these registers to govern {hardware} options and management direct reminiscence entry through the assault.
“If we attempt to describe this characteristic and the way the attackers took benefit of it, all of it comes right down to this: they’re able to write knowledge to a sure bodily deal with whereas bypassing the hardware-based reminiscence safety by writing the information, vacation spot deal with, and knowledge hash to unknown {hardware} registers of the chip unused by the firmware,” explains Kaspersky’s report.
Kaspersky hypothesizes that together with this undocumented {hardware} characteristic on the completed client model of the iPhone is both a mistake or was left in to help Apple engineers in debugging and testing.
Apple fastened the flaw by updating the system tree to limit bodily deal with mapping.
Nonetheless, how the attackers gained information of such an obscure exploitable mechanism within the first place stays unknown.




