Background
Final yr, the Federal Commerce Fee (FTC) obtained greater than 330,000 reviews of enterprise impersonation scams and practically 160,000 reviews of presidency impersonation scams. This represents about half of all of the fraud reported on to the FTC. The monetary losses attributable to electronic mail impersonation scams are staggering. They topped $1.1 billion in 2023, which was greater than thrice the quantity reported in 2020.
Monetary fraud is a severe difficulty—and it’s on the rise. In 2023, customers reported shedding greater than $10 billion to fraud. That is the primary time that losses reached that benchmark, and it’s a 14% improve from 2022. The commonest reviews have been imposter scams. This class noticed vital will increase in reviews from the enterprise and authorities sectors.
The situation
Proofpoint not too long ago detected a menace actor’s message to the monetary controller of a Dutch monetary establishment, which is thought for its experience in business danger. On this assault, the menace actor pretended to be the corporate’s CEO—a tactic that’s referred to as CEO fraud. In these assaults, the aim is to use the recipient’s belief to get them to carry out a particular motion.
The menace: How did the assault occur?
The attacker emailed the Dutch monetary firm’s controller, asking that two funds be despatched to London. The e-mail demanded that funds be made “as we speak” to create a way of urgency. To assist make the message appear credible, the attacker claimed to have entry to the IBAN and SWIFT codes.
Unique electronic mail from the menace actor.
Proofpoint
The identical electronic mail translated into English
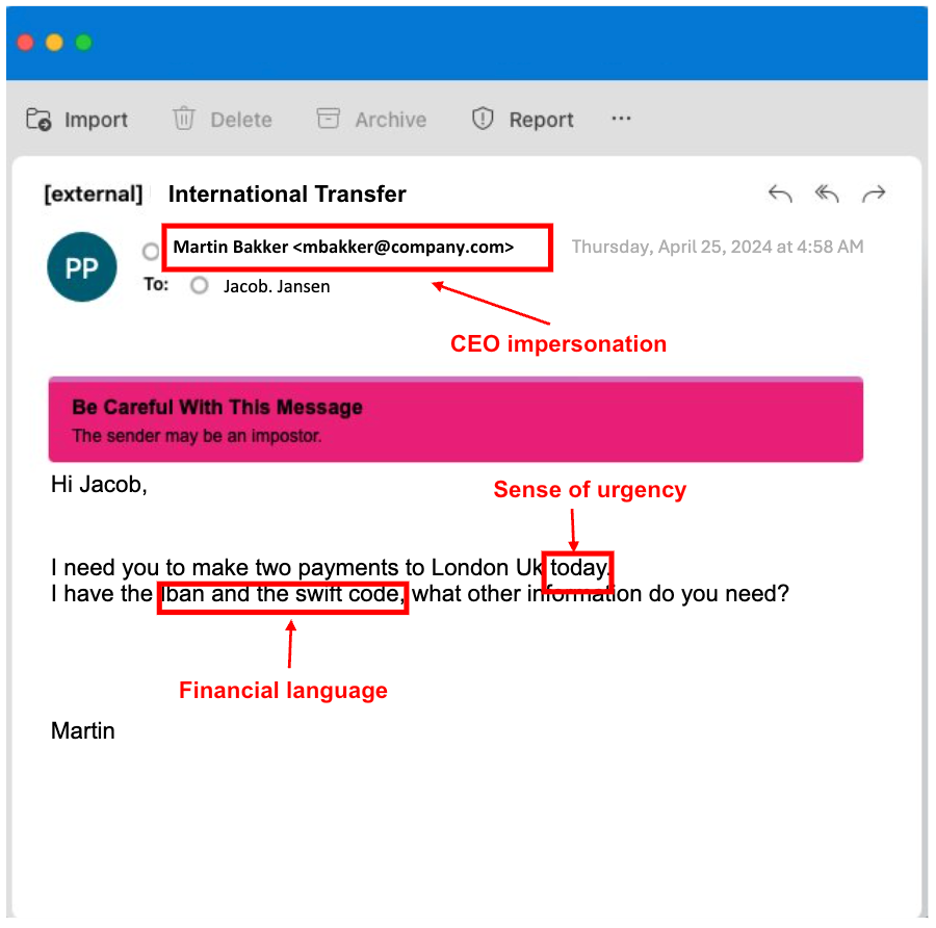
Proofpoint
Detection: How did Proofpoint stop this assault?
Proofpoint has the trade’s first predelivery menace detection engine that makes use of semantic evaluation to grasp message intent. Powered by a big language (LLM) mannequin engine, it stops superior electronic mail threats earlier than they’re delivered to customers’ inboxes. That’s what stopped this malicious message from reaching the monetary controller’s inbox.
Pre-delivery safety is so vital as a result of, primarily based on Proofpoint’s telemetry throughout greater than 230,000 organizations all over the world, post-delivery detections are often too late. Almost one in seven malicious URL clicks happen inside one minute of the e-mail’s arrival, and greater than one-third of BEC replies occur in lower than 5 minutes. These slim timeframes, throughout which a consumer can fall prey to an assault, underscore the significance of blocking malicious assaults earlier than they will attain a consumer’s inbox.
Right here’s extra about our LLM engine:
- Intent comprehension. Our LLM engine can perceive the intent of incoming messages, which is vital to stopping impersonation threats. On this case, the LLM engine recognized the sense of urgency and monetary language within the attacker’s electronic mail.
- Contextual understanding. Semantic evaluation can perceive the contextual utilization of phrases, phrases and mixtures, like urgency and suspicious language. In consequence, it could actually interpret data and grasp the entire that means of a given message.
- Language agnostic. It doesn’t matter what phrases are used or what language an impersonation electronic mail is written in. Our semantic evaluation is language agnostic and helps over 100 languages.
TAP Dashboard with semantic evaluation. Excessive-level Observations exhibits how Proofpoint summarizes the impersonation, together with AI Inferred Theme, Suspicious Conduct and Suspicious Textual content.
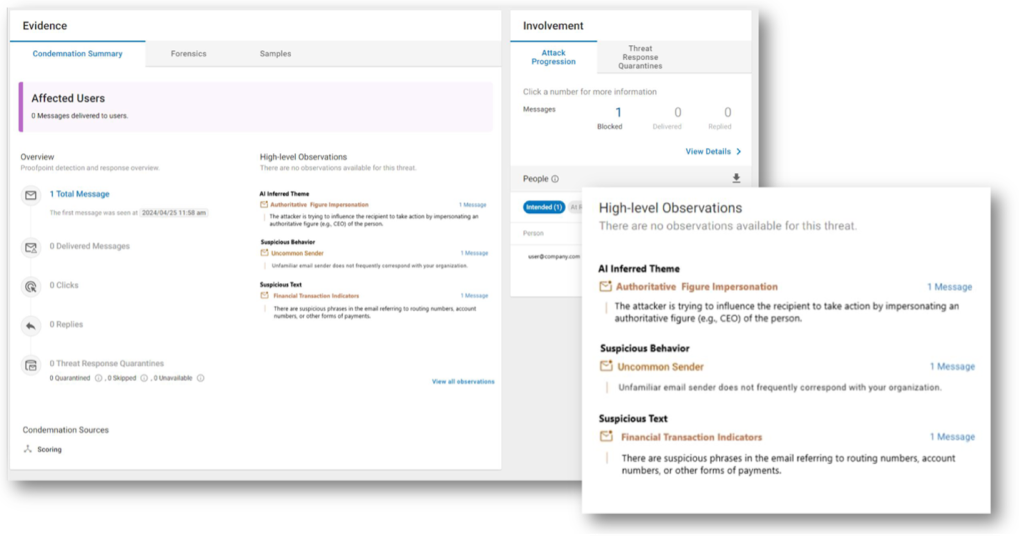
Proofpoint
Remediation: What are the teachings discovered?
Listed here are a number of classes from this CEO impersonation situation:
- Cease threats earlier than customers see them. Superior applied sciences like semantic evaluation might help detect and forestall threats earlier than they attain a consumer’s inbox. This ensures that fewer threats slip by the cracks. It additionally reduces the chance of false positives and enhances menace detection efficacy.
- Proactively report suspicious messages. Reporting instruments can make sure that threats are stopped rapidly. So give customers instruments to proactively report suspicious emails of their inbox.
- Assist customers change their habits. Menace actors will make use of refined strategies to control customers into performing actions that compromise security by impersonating figures of authority. Safety consciousness coaching might help educate finish customers and empower them to report suspicious messages.
Proofpoint delivers human-centric safety
Proofpoint affords a human-centric strategy to cybersecurity. We offer strong safety to your customers and enterprise in opposition to these and different forms of assaults. We perceive that individuals are probably the most focused hyperlink within the assault chain, which is why we concentrate on defending them.
Our new semantic evaluation LLM gives high-fidelity detection and efficacy to cease superior electronic mail threats earlier than they attain customers’ inboxes. Our fashionable strategy gives steady menace detection and evaluation all through the e-mail supply circulate, from predelivery to post-delivery—and at click-time, too. This end-to-end safety permits your enterprise to protect in opposition to new and rising threats.
To learn to defend individuals and defend knowledge on this planet of generative AI, register for our subsequent webinar sequence, “Within the Trenches with Menace Analysis: Improvements and Insights to Defend the Human Layer,” which began on June 6, 2024.




