Uhale Android-based digital image frames include a number of crucial security vulnerabilities and a few of them obtain and execute malware at boot time.
Cellular security firm Quokka carried out an in-depth security evaluation on the Uhale app and located conduct suggesting a reference to the Mezmess and Voi1d malware households.
The researchers reported the problems to ZEASN (now ‘Whale TV’), the Chinese language agency behind the Uhale platform used within the digital image frames of quite a few completely different manufacturers, however acquired no reply to a number of notificaitions since Might.

Computerized malware supply
Beginning with probably the most alarming findings, most of the analyzed Uhale photograph frames obtain malicious payloads from China-based servers at boot.
“Upon booting, many investigated frames test for and replace to the Uhale app model 4.2.0,” Quokka researchers say within the report.
“The machine then installs this new model and reboots. After the reboot, the up to date Uhale app initiates the obtain and execution of malware.”
The downloaded JAR/DEX file that’s saved beneath the Uhale app’s file listing is loaded and executed at each subsequent boot.
The units that Quokka examined had the SELinux security module disabled, got here rooted by default, and plenty of system elements had been signed with AOSP test-keys.
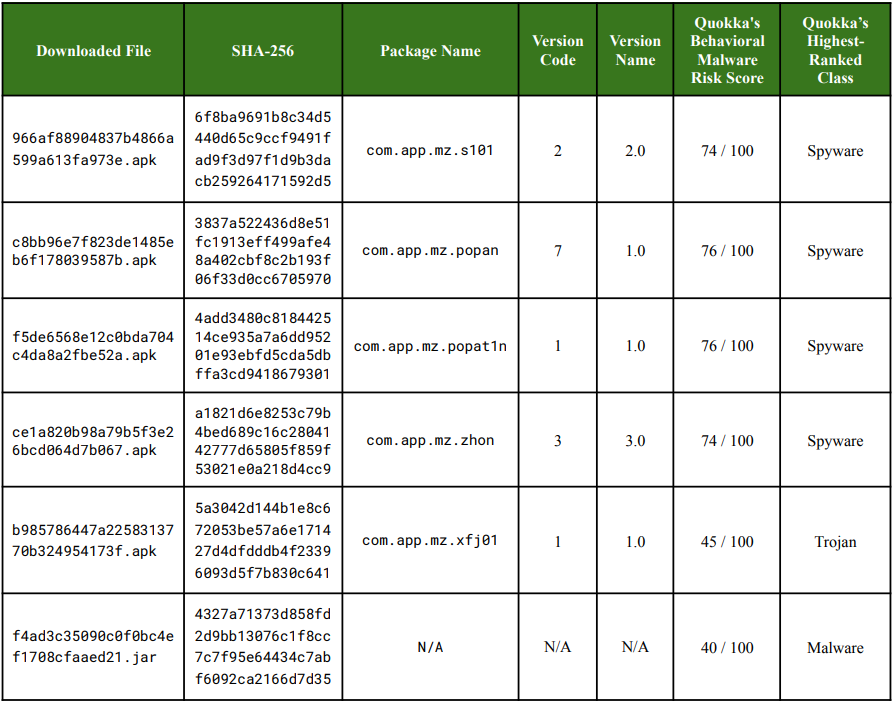
Supply: Quokka
The researchers discovered proof linking the downloaded payloads to the Vo1d botnet and Mzmess malware households, based mostly on bundle prefixes, string names, endpoints, supply workflow, and artifact places.
Nonetheless, it’s unclear how the units obtained contaminated.
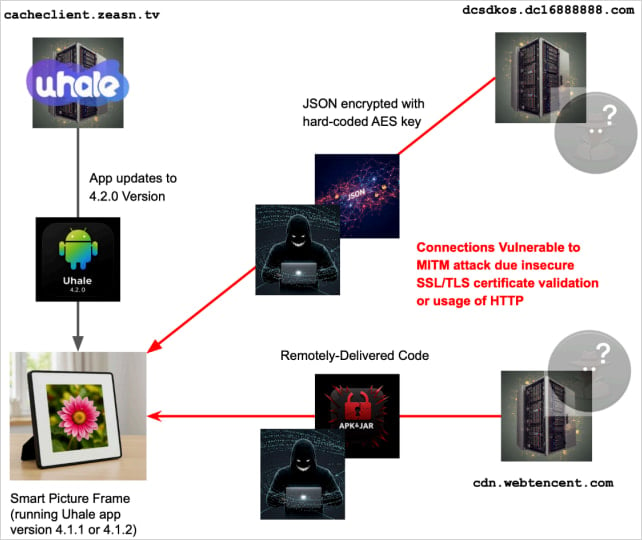
Supply: Quokka
A number of security gaps
Except for the malware supply, which didn’t happen on all Uhale-branded image frames, the researchers additionally found greater than a dozen vulnerabilities.
Among the many 17 security points that Quokka discloses within the report, 11 of which have CVE-IDs assigned, under are probably the most important:
- CVE-2025-58392 / CVE-2025-58397 – An insecure TrustManager implementation permits man-in-the-middle injection of solid encrypted responses, resulting in distant code execution as root on affected units.
- CVE-2025-58388 – The app’s replace course of passes unsanitized filenames immediately into shell instructions, enabling command injection and distant set up of arbitrary APKs.
- CVE-2025-58394 – All examined frames ship with SELinux disabled, are rooted by default, and use public AOSP test-keys, in order that they’re basically totally compromised out of the field.
- CVE-2025-58396 – The pre-installed app exposes a file server on TCP port 17802 that accepts unauthenticated uploads, permitting any native community host to jot down or delete arbitrary recordsdata.
- CVE-2025-58390 – The app’s WebViews ignore SSL/TLS errors and allow blended content material, permitting attackers to inject or intercept information displayed on the machine, enabling phishing or content material spoofing.
- Hardcoded AES key (DE252F9AC7624D723212E7E70972134D) used to decrypt sdkbin responses.
- A number of fashions embrace Adups replace elements and outdated libraries, whereas the app additionally makes use of weak crypto patterns and hardcoded keys, creating supply-chain dangers.
Since most of those merchandise are marketed and bought beneath varied manufacturers with out mentioning the platform they use, it’s troublesome to estimate the precise variety of probably impacted customers.
The Uhale app has greater than 500,000 downloads on Google Play and 11,000 consumer evaluations within the App Retailer. Uhale-branded photograph frames on Amazon have almost a thousand consumer evaluations.
BleepingComputer has independently contacted ZEASN with a request for remark, however we now have not acquired a response by publication time.
It is suggested that customers solely purchase digital units from respected manufacturers that use official Android photographs with out firmware modifications, Google Play providers, and built-in malware protections.

As MCP (Mannequin Context Protocol) turns into the usual for connecting LLMs to instruments and information, security groups are transferring quick to maintain these new providers secure.
This free cheat sheet outlines 7 finest practices you can begin utilizing in the present day.




