Probably the most damaging cyber threats in the present day don’t goal machines or programs—they aim people. At present, 74% of data breaches depend on exploiting the human component. From staff clicking on malicious hyperlinks to being deceived by emails posing as executives and suppliers, human-targeted assaults jeopardize companies worldwide each day.
In relation to focused e-mail threats, Proofpoint has seen attackers pivot away from static file attachments towards malicious hyperlinks which should be triggered by human clicks to provoke a wider assault. Whether or not their aim is to launch a phishing assault and steal credentials or direct customers to malware-laden web sites and unleash ransomware, adversaries now depend malicious URLs as one among their favored techniques to additional their assaults.
To assist organizations cease URL-based assaults earlier than they even begin, Proofpoint is introducing the trade’s first pre-delivery suspicious URL maintain and sandboxing functionality as a part of Proofpoint Menace Safety. When mixed with our click-time protections, it creates probably the most formidable set of defense-in-depth measures out there for organizations to forestall assaults from reaching their human targets.
URL-based threats: a preferred attacker method
Current Proofpoint menace intelligence and analysis knowledge reveals that the common variety of every day URL-based threats has elevated to over 4.5 million. That is an alarming 119% rise over the previous three years.
Infographic: 1 in 7 clicks on malicious hyperlinks occur in 60 seconds of supply.
Proofpoint
What’s equally regarding is the velocity at which these assaults may cause injury. Analysis from Proofpoint reveals that 1 in 7 clicks on an unsafe hyperlink occurs in lower than 60 seconds after an e-mail’s supply. This fast click on response demonstrates the essential nature of robust pre-delivery safety to cut back danger of customers clicking on malicious hyperlinks.
Enhanced predelivery safety for URL-based threats
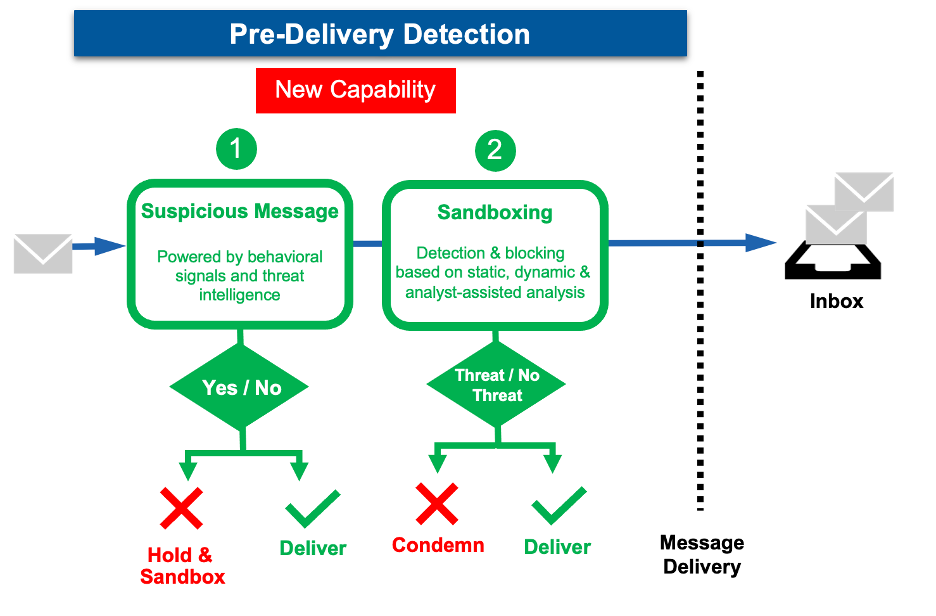
Our new functionality permits organizations to carry suspicious messages with URLs for sandbox evaluation, minimizing the danger of a person partaking with the malicious URL. We use behavioral indicators and menace intelligence to find out if a message ought to be held for extra thorough inspection. Our sandbox know-how conducts an exhaustive evaluation of the URL utilizing static and dynamic evaluation, in addition to analyst-assisted execution to maximise detection and intelligence extraction.
Maintain and sandbox messages with suspicious URLs stops threats earlier than they attain customers.
Proofpoint
Steady protection with click-time safety
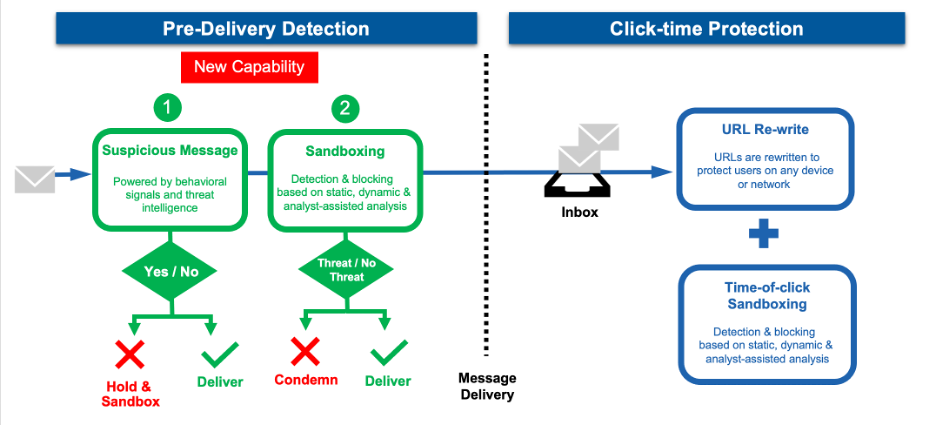
URLs should not at all times born malicious. They will grow to be weaponized post-delivery. As such, emails containing hyperlinks require fixed scrutiny to guard in opposition to superior threats. That’s why steady evaluation from pre-delivery by means of to click-time is so essential for stopping URL-based assaults. With our new pre-delivery maintain & sandbox for suspicious URL functionality, Proofpoint uniquely offers probably the most superior, end-to-end safety in opposition to URL threats.
Proofpoint uniquely delivers steady protection for URL-based threats.
Proofpoint
Predelivery detection. Proofpoint identifies and blocks assaults earlier than they land in customers’ inboxes, eliminating the possibility a person might activate them. We’ve enhanced this functionality by holding suspicious messages with URLs for sandbox evaluation.
Click on-time safety. Proofpoint continues to watch delivered messages for hyperlinks which will change over time. URLs in delivered messages are re-written and sandboxed at time of click on. Clients may allow isolation for an additional layer of safety post-delivery.
Be taught extra
If you’d like extra particulars about the best way to construct a complete e-mail security technique for your online business, see this information from Proofpoint. And to realize extra perception into the altering menace panorama and the dangers on your customers, make sure to learn our newest State of the Phish report.




