Readers assist assist Home windows Report. We might get a fee in the event you purchase by way of our hyperlinks.
Learn our disclosure web page to seek out out how will you assist Home windows Report maintain the editorial workforce. Learn extra
Based on a current report from SecurityScorecard, an enormous community of over 130,000 hacked gadgets is actively making an attempt to interrupt into Microsoft 365 accounts worldwide. These attackers are utilizing a method known as password spraying, which includes guessing frequent passwords throughout many accounts.
They’re particularly concentrating on programs that also use primary authentication, which permits them to sidestep multi-factor authentication (MFA) protections.
Based on the SecurityScorecard report, the attackers are utilizing credentials stolen by malicious software program often known as infostealers. This lets them launch large-scale assaults on quite a few accounts. By counting on non-interactive logins by way of Primary Authentication, they will sneak previous MFA safeguards and achieve entry with out setting off any security alarms. It’s like selecting a lock quietly as a substitute of kicking down the door.
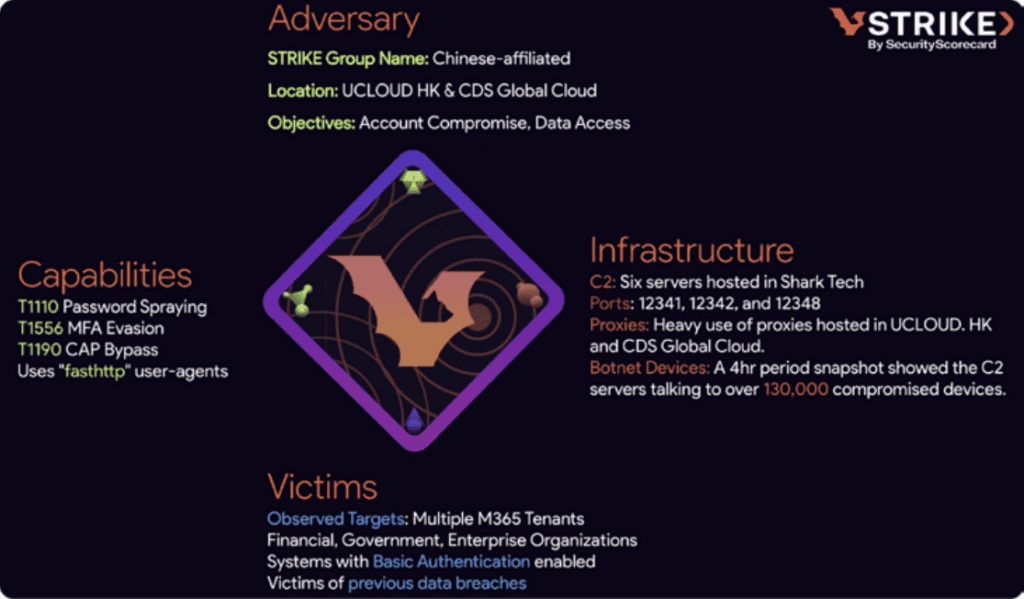
Organizations relying solely on interactive sign-in monitoring are blind to those assaults. Non-interactive sign-ins, generally used for service-to-service authentication, legacy protocols (e.g., POP, IMAP, SMTP), and automatic processes, don’t set off MFA in lots of configurations. Primary Authentication, nonetheless enabled in some environments, permits credentials to be transmitted in plain kind, making it a first-rate goal for attackers, writes SecurityScorecard.
The botnet, which is allegedly operated by a Chinese language group, is utilizing a sneaky methodology to attempt to break into accounts by leveraging Primary Authentication. This method includes concentrating on a variety of accounts with generally used or leaked passwords. Primary Auth doesn’t require any back-and-forth interplay so if the attackers discover a match with the credentials they’re making an attempt, they aren’t requested for multi-factor authentication (MFA) and sometimes slip previous Conditional Entry Insurance policies (CAP) unnoticed. This permits them to quietly verify whether or not an account’s credentials are legitimate.
As soon as they’ve verified the login particulars, these credentials can be utilized in two methods: both to entry older companies that don’t demand MFA, or as a part of extra superior phishing schemes designed to completely bypass security measures and take over the account.
SecurityScorecard factors out that you just would possibly have the ability to spot indicators of those password-spray assaults by checking your Entra ID logs. Search for uncommon patterns like a spike in non-interactive login makes an attempt, repeated failed logins from completely different IP addresses, and the looks of the fasthttp person agent within the authentication data.
This is among the most harmful assaults because the wrongdoers can bypass the multi-factor authentication. We’ve discovered about this from Bleeping Pc.
His abrupt curiosity in computer systems began when he noticed the primary House Pc as a child. Nevertheless, his ardour for Home windows and the whole lot associated grew to become apparent when he grew to become a sys admin in a pc science highschool.
With 14 years of expertise in writing about the whole lot there may be to learn about science and expertise, Claudiu additionally likes rock music, chilling within the backyard, and Star Wars. Could the pressure be with you, at all times!




