Amazon Internet Companies (AWS), Cloudflare, and Google on Tuesday mentioned they took steps to mitigate record-breaking distributed denial-of-service (DDoS) assaults that relied on a novel method referred to as HTTP/2 Fast Reset.
The layer 7 assaults had been detected in late August 2023, the businesses mentioned in a coordinated disclosure. The cumulative susceptibility to this assault is being tracked as CVE-2023-44487, and carries a CVSS rating of seven.5 out of a most of 10.
Whereas the assaults geared toward Google’s cloud infrastructure peaked at 398 million requests per second (RPS), those geared toward AWS and Cloudflare exceeded a quantity of 155 million and 201 million requests per second (RPS), respectively.
HTTP/2 Fast Reset refers to a zero-day flaw within the HTTP/2 protocol that may be exploited to hold out DDoS assaults. A major characteristic of HTTP/2 is multiplexing requests over a single TCP connection, which manifests within the type of concurrent streams.
What’s extra, a consumer that desires to abort a request can concern a RST_STREAM body to halt the info alternate. The Fast Reset assault leverages this methodology to ship and cancel requests in fast succession, thereby circumventing the server’s concurrent stream most and overloading the server with out reaching its configured threshold.
“HTTP/2 fast reset assaults encompass a number of HTTP/2 connections with requests and resets in fast succession,” Mark Ryland and Tom Scholl at AWS mentioned.
“For instance, a collection of requests for a number of streams will likely be transmitted adopted up by a reset for every of these requests. The focused system will parse and act upon every request, producing logs for a request that’s then reset, or canceled, by a consumer.”
This means to reset streams instantly permits every connection to have an indefinite variety of requests in flight, thereby enabling a risk actor to concern a barrage of HTTP/2 requests that may overwhelm a focused web site’s functionality to reply to new incoming requests, successfully taking it down.
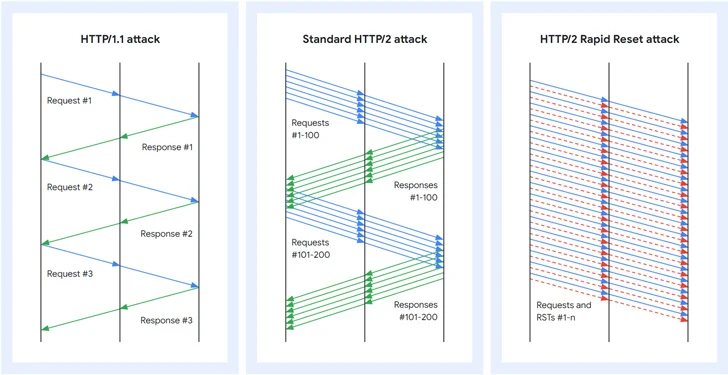
Put in another way, by initiating lots of of 1000’s of HTTP/2 streams and quickly canceling them at scale over a longtime connection, risk actors can overwhelm web sites and knock them offline. One other essential facet is that such assaults may be pulled off utilizing a modestly-sized botnet, one thing to tune of 20,000 machines as noticed by Cloudflare.
“This zero-day supplied risk actors with a vital new instrument of their Swiss Military knife of vulnerabilities to take advantage of and assault their victims at a magnitude that has by no means been seen earlier than,” Grant Bourzikas, chief security officer at Cloudflare, mentioned.
HTTP/2 is utilized by 35.6% of all of the web sites, in accordance with W3Techs. The share of requests that use HTTP/2 is at 77%, per information shared by Internet Almanac.
Google Cloud mentioned it has noticed a number of variants of the Fast Reset assaults that whereas not as efficient because the preliminary model, are extra environment friendly than the usual HTTP/2 DDoS assaults.
“The primary variant doesn’t instantly cancel the streams, however as a substitute opens a batch of streams directly, waits for a while, after which cancels these streams after which instantly opens one other giant batch of recent streams,” Juho Snellman and Daniele Lamartino mentioned.
“The second variant does away with canceling streams solely, and as a substitute optimistically tries to open extra concurrent streams than the server marketed.”
F5, in an unbiased advisory of its personal, mentioned the assault impacts the NGINX HTTP/2 module and has urged its prospects to replace their NGINX configuration to restrict the variety of concurrent streams to a default of 128 and persist HTTP connections for as much as 1000 requests.
“After at the moment, risk actors will likely be largely conscious of the HTTP/2 vulnerability; and it’ll inevitably grow to be trivial to take advantage of and kickoff the race between defenders and assaults — first to patch vs. first to take advantage of,” Bourzikas additional mentioned. “Organizations ought to assume that programs will likely be examined, and take proactive measures to make sure safety.”




