Hewlett Packard Enterprise (HPE) is investigating a possible new breach after a risk actor put allegedly stolen information up on the market on a hacking discussion board, claiming it comprises HPE credentials and different delicate data.
The corporate has advised BleepingComputer that they haven’t discovered any proof of a security breach and no ransom has been requested, but it surely’s investigating the risk actor’s claims.
“We’re conscious of the claims and are investigating their veracity,” HPE’s Sr. Director for World Communications Adam R. Bauer advised BleepingComputer on Thursday.
“Presently now we have not discovered proof of an intrusion, nor any impression to HPE services or products. There has not been an extortion try.”
When requested to supply extra particulars concerning the corporate’s ongoing investigation, Bauer mentioned that they had “nothing new to share.”
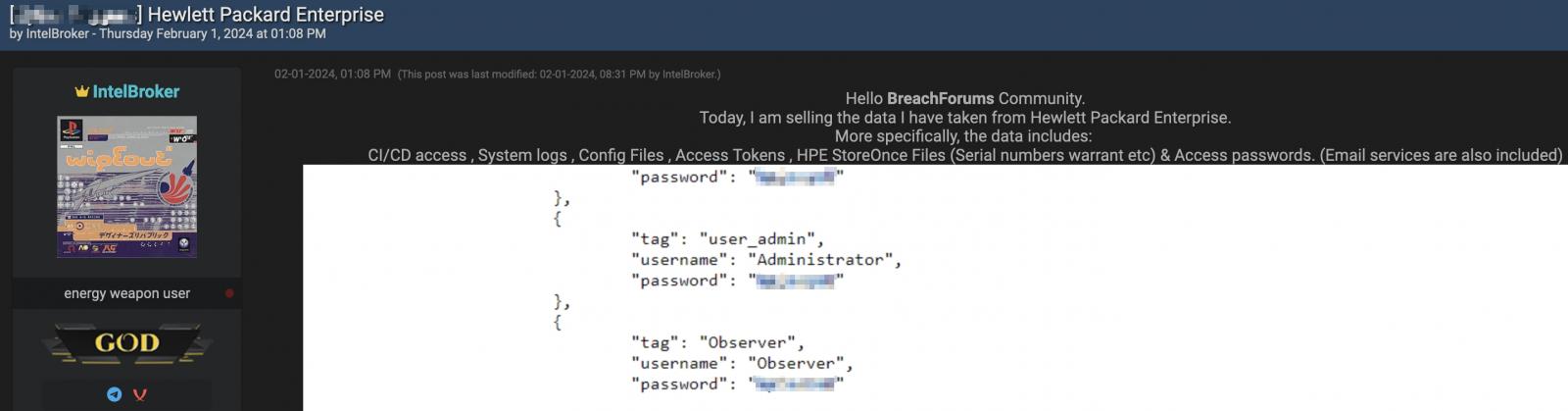
IntelBroker, the risk actor promoting the alleged HPE information, shared screenshots of among the supposedly stolen HPE credentials however has but to reveal the supply of the knowledge or the tactic used to acquire it.
“Immediately, I’m promoting the information I’ve taken from Hewlett Packard Enterprise,” the risk actor says in a publish on the hacking discussion board.
“Extra particularly, the information consists of: CI/CD entry , System logs , Config Information , Entry Tokens , HPE StoreOnce Information (Serial numbers warrant and so on) & Entry passwords. (E-mail providers are additionally included).”
IntelBroker is greatest recognized for the breach of DC Well being Hyperlink, which led to a congressional listening to after it uncovered the non-public information of U.S. Home of Representatives members and workers.
Different cybersecurity incidents linked to IntelBroker are the breach of the Weee! grocery service and an alleged breach of Normal Electrical Aviation.
Russian hackers breach HPE company electronic mail accounts
This investigation comes after HPE disclosed two weeks in the past that the corporate’s Microsoft Workplace 365 electronic mail surroundings was breached in Might 2023 by hackers the corporate believed to be a part of the Russian APT29 hacking group linked to Russia’s Overseas Intelligence Service (SVR).
The corporate mentioned the Russian hackers stole SharePoint recordsdata and information from its cybersecurity staff and different departments and maintained entry to its cloud infrastructure till December when HPE was once more alerted of a breach of its cloud-based electronic mail surroundings.
“On December 12, 2023, HPE was notified {that a} suspected nation-state actor had gained unauthorized entry to the corporate’s Workplace 365 electronic mail surroundings. HPE instantly activated cyber response protocols to start an investigation, remediate the incident, and eradicate the exercise,” HPE advised BleepingComputer.
“By way of that investigation, which stays ongoing, we decided that this nation-state actor accessed and exfiltrated information starting in Might 2023 from a small proportion of HPE mailboxes belonging to people in our cybersecurity, go-to-market, enterprise segments, and different features.”
Days earlier than HPE’s Russian hack disclosure, Microsoft revealed an analogous breach the place APT29 breached a few of its company electronic mail accounts belonging to its management staff and staff within the cybersecurity and authorized departments.
Microsoft later shared that the risk actors gained entry to the company electronic mail accounts after hacking right into a misconfigured check tenant account by brute forcing its password in a “password spraying” assault.
HPE was additionally breached in 2018 when APT10 Chinese language hackers additionally hacked into IBM’s networks and used the entry to hack into their prospects’ units.
Extra lately, HPE disclosed in 2021 that information repositories of its Aruba Central community monitoring platform have been compromised, enabling attackers to entry information about monitored units and their places.




