Ransomware teams are more and more switching to distant encryption of their assaults, marking a brand new escalation in techniques adopted by financially motivated actors to make sure the success of their campaigns.
“Firms can have 1000’s of computer systems related to their community, and with distant ransomware, all it takes is one underprotected machine to compromise the complete community,” Mark Loman, vp of risk analysis at Sophos, mentioned.
“Attackers know this, in order that they hunt for that one’ weak spot’ — and most firms have not less than one. Distant encryption goes to remain a perennial downside for defenders.”
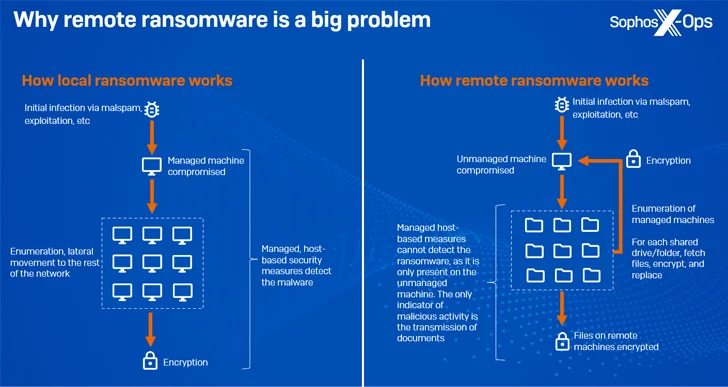
Distant encryption (aka distant ransomware), because the title implies, happens when a compromised endpoint is used to encrypt knowledge on different units on the identical community.
In October 2023, Microsoft revealed that round 60% of ransomware assaults now contain malicious distant encryption in an effort to reduce their footprint, with greater than 80% of all compromises originating from unmanaged units.
“Ransomware households identified to assist distant encryption embrace Akira, ALPHV/BlackCat, BlackMatter, LockBit, and Royal, and it is a method that is been round for a while – way back to 2013, CryptoLocker was concentrating on community shares,” Sophos mentioned.
A major benefit to this method is that it renders process-based remediation measures ineffective and the managed machines can not detect the malicious exercise since it’s only current in an unmanaged machine.
The event comes amid broader shifts within the ransomware panorama, with the risk actors adopting atypical programming languages, concentrating on past Home windows programs, auctioning stolen knowledge, and launching assaults after enterprise hours and at weekends to thwart detection and incident response efforts.
Sophos, in a report printed final week, highlighted the “symbiotic – however usually uneasy – relationship” between ransomware gangs and the media, as a option to not solely appeal to consideration, but in addition to regulate the narrative and dispute what they view as inaccurate protection.
This additionally extends to publishing FAQs and press releases on their knowledge leak websites, even together with direct quotes from the operators, and correcting errors made by journalists. One other tactic is using catchy names and slick graphics, indicating an evolution of the professionalization of cyber crime.
“The RansomHouse group, for instance, has a message on its leak website particularly geared toward journalists, through which it affords to share data on a ‘PR Telegram channel’ earlier than it’s formally printed,” Sophos famous.
Whereas ransomware teams like Conti and Pysa are identified for adopting an organizational hierarchy comprising senior executives, system admins, builders, recruiters, HR, and authorized groups, there’s proof to recommend that some have marketed alternatives for English writers and audio system on legal boards.
“Media engagement offers ransomware gangs with each tactical and strategic benefits; it permits them to use strain to their victims, whereas additionally enabling them to form the narrative, inflate their very own notoriety and egos, and additional ‘mythologize’ themselves,” the corporate mentioned.




