Every New 12 months introduces a brand new set of challenges and alternatives for strengthening our cybersecurity posture. It is the character of the sphere – the pace at which malicious actors perform superior persistent threats brings a continuing, evolving battle for cyber resilience. The thrill in cybersecurity lies on this steady adaptation and studying, at all times staying one step forward of potential threats.
As practitioners in an {industry} that operates around-the-clock, this hypervigilance turns into second nature. We’re at all times in a continuing state of readiness, anticipating the subsequent transfer, adapting methods, and counteracting threats. Nonetheless, it stays simply as essential to have our fingers on the heartbeat of the most typical vulnerabilities impacting security postures proper now. Why? Understanding these weak factors is not only about protection; it is about guaranteeing sturdy, uninterrupted enterprise continuity in an atmosphere the place dangers are at all times across the nook.
The Significance of Repeatedly Assessing Your Safety Posture
The journey to construct a cyber resilient security posture begins with figuring out present vulnerabilities; nevertheless, when requested about their vulnerability visibility, lower than half of cybersecurity professionals declare to have excessive (35%) or full visibility (11%). At greatest, greater than half of organizations (51%) have solely reasonable visibility into their vulnerabilities.[1]
Common assessments are one of many major methods you may consider your group’s security posture and achieve the visibility it’s essential to perceive the place dangers are. These assessments comprehensively overview your group’s cybersecurity practices and infrastructure and may vary in scope and frequency relying in your group’s wants and the maturity of your danger program.
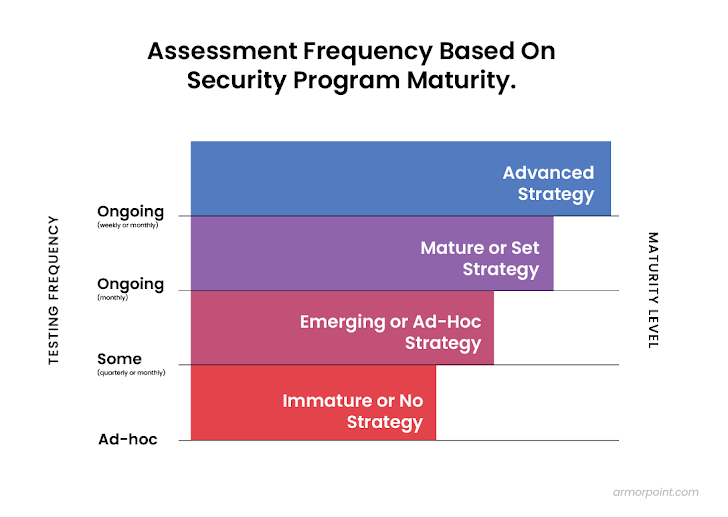
Safety Maturity and Your Testing Frequency
- Immature or No Danger Technique: Assessments usually are not carried out on an ongoing frequency or are carried out on an ad-hoc foundation.
- Rising or Advert-Hoc Danger Technique: Assessments are carried out with some frequency, usually quarterly or month-to-month.
- Mature or Set Technique: Assessments are carried out on an ongoing foundation, often month-to-month.
- Superior Technique: Repeatedly assessments are engrained within the general danger program and happen on a month-to-month or weekly foundation relying on the kind of take a look at.
Advised Testing Frequency by Widespread Framework
- NIST CSF: The Nationwide Institute of Requirements and Know-how (NIST) pointers differ from quarterly to month-to-month scans, based mostly on the particular pointers of the governing framework.
- PCI DSS: The Cost Card Trade Data Safety Customary (PCI DSS) mandates quarterly scans.
- HIPAA: The Well being Data Safety Accountability Act (HIPAA) doesn’t require particular scanning intervals however emphasizes the significance of a well-defined evaluation technique.
Forms of Common Assessments
- Vulnerability Scans
- Penetration Checks
- Breach and Ransomware Simulations
- Safety Status Scans
- Enterprise Impression Analyses
- Safety Posture Evaluation
Conducting assessments routinely permits your group to preemptively establish potential security threats and vulnerabilities, very like preventive well being check-ups in your group’s cybersecurity.
ArmorPoint has not too long ago launched a security maturity self-assessment. Take the 15-question quiz to find out the gaps in your security posture.
The High 6 Vulnerabilities
Now, let’s discover the vulnerabilities generally discovered throughout these common security posture assessments and their potential impression in your group’s security integrity.
Vulnerability Administration Program Gaps
A structured vulnerability administration program is the cornerstone of proactive cybersecurity in your group. It serves as your group’s radar for promptly figuring out and addressing security weaknesses. Organizations that lack such a program expose themselves to vital dangers equivalent to elevated publicity to recognized vulnerabilities, inefficient patch administration, and the diminished potential to prioritize crucial vulnerabilities.
Deficiencies in Detection and Monitoring
Insufficient detection techniques can depart your group blind to ongoing threats, permitting attackers to function undetected for prolonged durations. With out sufficient detection techniques, equivalent to superior Intrusion Detection Techniques (IDS) or Safety Data and Occasion Administration (SIEM) options, there’s a danger of delayed or missed risk detection, elevated dwell time for attackers, and the next potential for information exfiltration. To enhance this side, it is essential to introduce superior monitoring instruments and techniques. Deploying state-of-the-art risk detection and response applied sciences, using conduct analytics for anomaly detection, and conducting threat-hunting workout routines are a few of the key approaches to reinforce detection capabilities.
The absence of such measures delays the identification of threats and hampers the power to reply successfully in a well timed method. Implementing a robust, well-rounded detection and monitoring system is important for sustaining a strong protection in opposition to evolving cyber threats. This contains repeatedly updating and refining detection methodologies to remain forward of the most recent assault vectors and strategies utilized by cybercriminals.
Lack of Insurance policies and Procedures
Organizations want formalized cybersecurity insurance policies and procedures to successfully handle security dangers. With out these in place, there are quite a few penalties, together with inconsistent security practices throughout departments, weakened incident response capabilities, issue in guaranteeing compliance with laws, and larger publicity to authorized, regulatory, monetary, and reputational penalties. Crafting and implementing complete security insurance policies entails creating and documenting these insurance policies clearly, guaranteeing they’re communicated successfully to all staff, and educating them on the significance of compliance.
Common opinions, updates, and variations of those insurance policies are essential to hold tempo with the evolving cyber risk panorama. This additionally ensures that the group’s cybersecurity measures stay related and efficient. As well as, having a set of well-defined procedures helps in standardizing responses to security incidents, which aids in minimizing the impression and dashing up restoration occasions within the occasion of a breach.
Insufficient Testing Practices
Common testing of security techniques and incident response plans is important for figuring out weaknesses and guaranteeing preparedness for real-world assaults. This contains conducting common penetration testing to uncover vulnerabilities, creating, training, and fine-tuning incident response plans, and fascinating in third-party security assessments. The significance of normal testing can’t be overstated, because it not solely helps in figuring out vulnerabilities earlier than attackers do but additionally assesses the effectiveness of present security controls.
Moreover, common testing ensures a swift and efficient response to incidents, mitigating potential harm proactively. This observe is essential in sustaining an up to date and resilient cybersecurity posture, able to defending in opposition to the most recent security threats. Partaking with third-party specialists for assessments brings an exterior perspective, usually uncovering blind spots that inner groups would possibly miss.
Coaching and Cyber Consciousness
Insufficiently educated employees can inadvertently introduce vulnerabilities and make a company extra vulnerable to assaults. The difficulty of inadequate coaching results in misconfigurations, human errors, and failure to acknowledge and reply to threats, thus decreasing the effectiveness of security controls. To handle this, approaches for security consciousness coaching are essential. Offering ongoing cybersecurity coaching, encouraging skilled improvement and certifications, and fostering a tradition of security consciousness are key measures.
These coaching initiatives assist be certain that employees in any respect ranges are geared up to establish and reply to security threats successfully. By conserving the workforce knowledgeable and vigilant, organizations can considerably scale back the chance of breaches brought on by human error. This proactive strategy to employees coaching is a crucial part of a complete cybersecurity technique.
Framework Adoption and Implementation
Deciding on and adhering to a cybersecurity framework is essential for organizations seeking to set up a structured strategy to security. The need of frameworks lies in offering a transparent roadmap for security, guaranteeing alignment with {industry} greatest practices, and facilitating compliance with laws. The suggested course of for framework choice entails assessing your group’s particular wants and danger tolerance, selecting an appropriate framework (e.g., NIST Cybersecurity Framework), and customizing it to suit the group’s distinctive necessities.
Framework adoption and implementation present a structured and methodical strategy to managing cybersecurity dangers. In addition they provide pointers for organising sturdy security measures and protocols, thus enhancing the general security posture of a company. Customizing the chosen framework ensures that it aligns completely with the group’s particular security wants, {industry} requirements, and regulatory necessities.
Danger Urge for food and Understanding
Understanding your group’s danger urge for food and integrating it into your cybersecurity technique is important for efficient danger administration. Figuring out the extent of danger your group is keen to simply accept varies from one group to a different and influences decision-making and useful resource allocation. This understanding of danger urge for food is essential in aligning cybersecurity efforts with the group’s danger tolerance and prioritizing security measures based mostly on danger assessments.
Danger informs technique, and sustaining steady vigilance is important to observe evolving dangers and adapt security methods accordingly. This strategy ensures that cybersecurity measures usually are not solely reactive however proactive, anticipating potential threats and mitigating them earlier than they materialize. By understanding and managing danger successfully, organizations can construct a resilient and sturdy cybersecurity posture tailor-made to their particular wants and danger tolerance ranges.
Mitigating Recognized Vulnerabilities
Now that we have totally examined these frequent vulnerabilities, it is essential to know learn how to prioritize their decision based mostly on severity and potential impression. Step one is to achieve extra visibility into your group’s vulnerabilities. As soon as recognized, you may prioritize these vulnerabilities successfully to mitigate them. To mitigate these dangers, it is steered to implement an industry-accepted framework equivalent to NIST CSF, CIS, or SANS. These frameworks information organizations in establishing sturdy cybersecurity practices and entails assessing present security measures in opposition to the framework’s requirements, creating and implementing applicable insurance policies, and guaranteeing common employees coaching for consciousness. Steady monitoring and enchancment are key, because it permits for the well timed identification and rectification of security gaps and vulnerabilities.
Take a proactive step in the direction of strengthening your security posture. Collaborate with seasoned cybersecurity specialists who will help establish and tackle your group’s particular security gaps. Request a complimentary Cybersecurity Workshop from ArmorPoint in the present day.
Cybersecurity is just not a one-time effort; it is an ongoing dedication to defending your group’s property and popularity. By addressing these frequent vulnerabilities revealed in security posture assessments and staying vigilant, you may strengthen your security posture and scale back the chance of falling sufferer to cyberattacks.
Obtain a Cybersecurity Guidelines to search out out what gaps you have got in your security posture.
1 https://www.tripwire.com/state-of-security/insight-vulnerability-management-report




