The Nationwide Cyber Safety Centre (NCSC) and Korea’s Nationwide Intelligence Service (NIS) warn that the North Korean Lazarus hacking group breaches firms utilizing a zero-day vulnerability within the MagicLine4NX software program to conduct supply-chain assaults.
MagicLine4NX is a security authentication software program developed by the South Korean firm Dream Safety, used for safe logins in organizations.
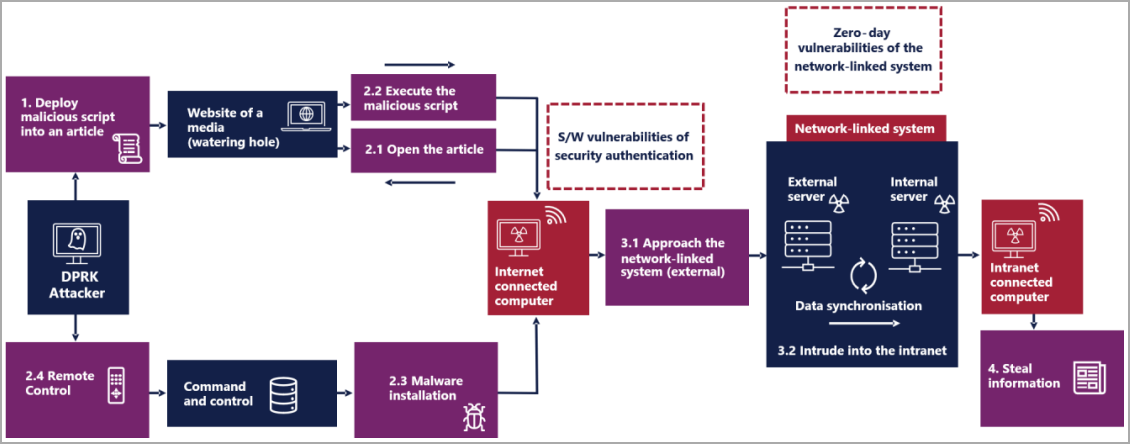
In line with the joint cybersecurity advisory, the DPRK-based risk actors leveraged a zero-day vulnerability within the product to breach their targets, primarily South Korean establishments.
“In March 2023, cyber actors used the software program vulnerabilities of security authentication and network-linked techniques in collection to realize unauthorized entry to the intranet of a goal group,” describes the advisory.
“It used a software program vulnerability of the MagicLine4NX security authentication program for the preliminary intrusion into an internet-connected laptop of the goal and exploited a zero-day vulnerability of the network-linked system to maneuver laterally and acquire unauthorized entry to info.”
The assault began with compromising a media outlet’s web site to embed malicious scripts into an article, permitting for a ‘watering gap’ assault.
When particular targets from sure IP ranges visited the article on the compromised web site, the scripts executed malicious code to set off the talked about vulnerability within the MagicLine4NX software program, impacting variations previous to 1.0.0.26.
This resulted within the sufferer’s laptop connecting to the attackers’ C2 (command and management) server, permitting them to entry an internet-side server by exploiting a vulnerability in a network-linked system.
Utilizing the info synchronization perform of this technique, the North Korean hackers unfold information-stealing code to the business-side server, compromising PCs inside the goal group.
The dropped code linked to 2 C2 servers, one performing as a gateway within the center and the second positioned externally on the web.
The perform of the malicious code consists of reconnaissance, knowledge exfiltration, downloading and executing encrypted payloads from the C2, and lateral community motion.
Detailed details about this assault, codenamed ‘Dream Magic’ and attributed to Lazarus, might be discovered on this AhnLab report, obtainable solely in Korean.
Lazarus provide chains
State-backed North Korean hacking operations persistently depend on provide chain assaults and the exploitation of zero-day vulnerabilities as a part of their cyber warfare ways.
In March 2023, it was found that “Labyrinth Chollima,” a subgroup of Lazarus, carried out a provide chain assault in opposition to VoIP software program maker 3CX to breach a number of high-profile firms worldwide.
Final Friday, Microsoft disclosed a provide chain assault on CyberLink that the Lazarus hacking group used to distribute trojanized, digitally-signed CyberLink installers to contaminate not less than 100 computer systems with the ‘LambLoad’ malware.
The North Korean hacking group makes use of most of these assaults to focus on particular firms, whether or not for cyber espionage, monetary fraud, or cryptocurrency theft.
Earlier this 12 months, the Cybersecurity Advisory (CSA) warned that the funds stolen in assaults by the North Korean hackers are used to fund the nation’s operations.
“The authoring companies assess that an unspecified quantity of income from these cryptocurrency operations helps DPRK national-level priorities and targets, together with cyber operations concentrating on america and South Korea governments—particular targets embody Division of Protection Data Networks and Protection Industrial Base member networks,” reads an advisory from CISA.




