Menace actors are fast to weaponize out there proof-of-concept (PoC) exploits in precise assaults, typically as rapidly as 22 minutes after exploits are made publicly out there.
That’s in response to Cloudflare’s Software Safety report for 2024, which covers exercise between Could 2023 and March 2024 and highlights rising menace tendencies.
Cloudflare, which presently processes a mean of 57 million HTTP requests per second, continues to see heightened scanning exercise for disclosed CVEs, adopted by command injections and makes an attempt to weaponize out there PoCs.
Through the examined interval, probably the most focused flaws have been CVE-2023-50164 and CVE-2022-33891 in Apache merchandise, CVE-2023-29298, CVE-2023-38203 and CVE-2023-26360 in Coldfusion, and CVE-2023-35082 in MobileIron.
A attribute instance of the rise within the pace of weaponization is CVE-2024-27198, an authentication bypass flaw in JetBrains TeamCity.
Cloudflare noticed a case of an attacker deploying a PoC-based exploit 22 minutes after its publication, leaving defenders basically no margin for remediation alternative.
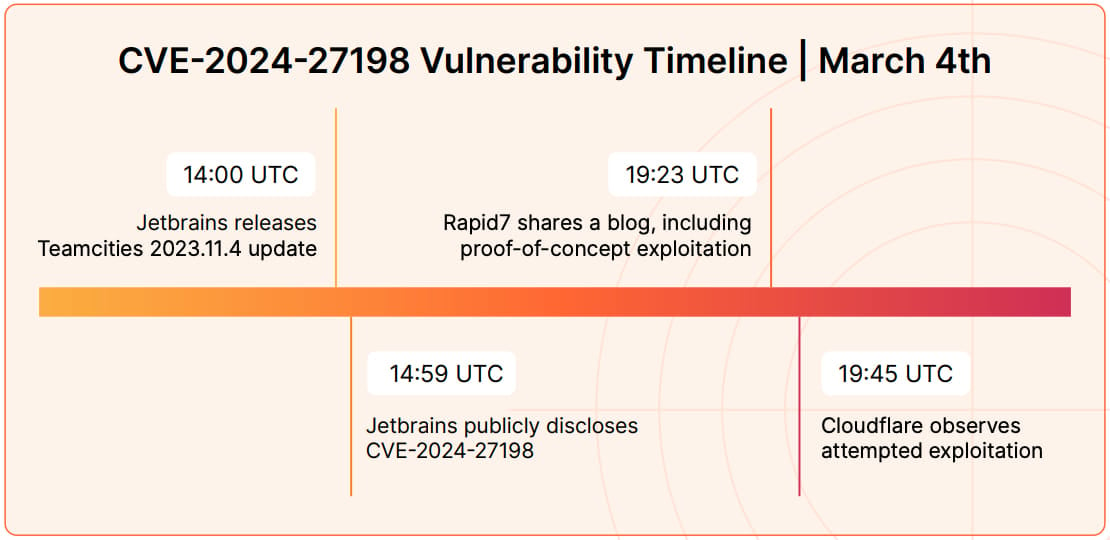
Supply: Cloudflare
The web agency says the one solution to fight this pace is to make use of AI help to rapidly develop efficient detection guidelines.
“The pace of exploitation of disclosed CVEs is commonly faster than the pace at which people can create WAF guidelines or create and deploy patches to mitigate assaults,” explains Cloudflare within the report.
“This additionally applies to our personal inside security analyst staff that maintains the WAF Managed Ruleset, which has led us to mix the human written signatures with an ML-based strategy to attain the very best steadiness between low false positives and pace of response.”
Cloudflare says that is partially the results of particular menace actors specializing in sure CVE classes and merchandise, creating an in-depth understanding of the way to rapidly make the most of new vulnerability disclosures.
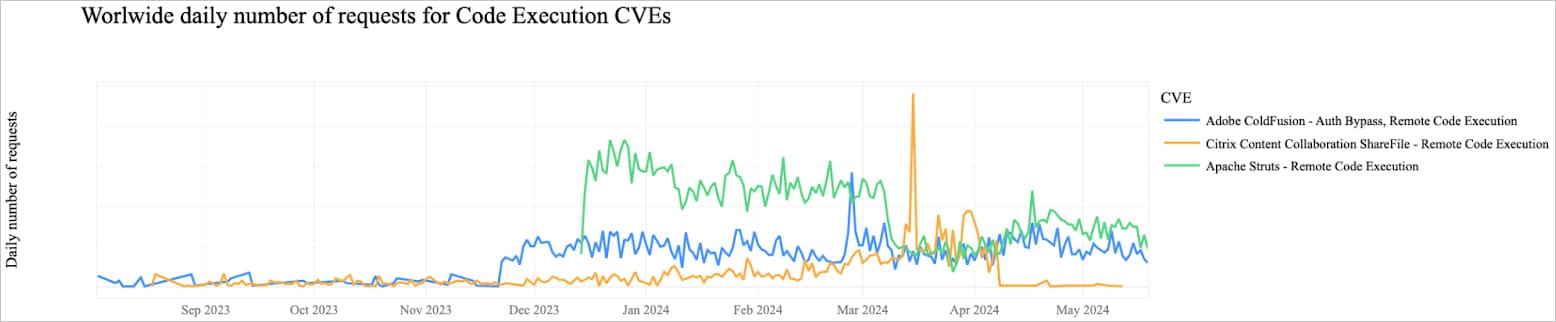
Supply: Cloudflare
6.8% of all web site visitors is DDoS
One other staggering spotlight in Cloudflare’s report is that 6.8% of all each day web site visitors is distributed denial of service (DDoS) site visitors aimed toward rendering on-line apps and companies unavailable to respectable customers.
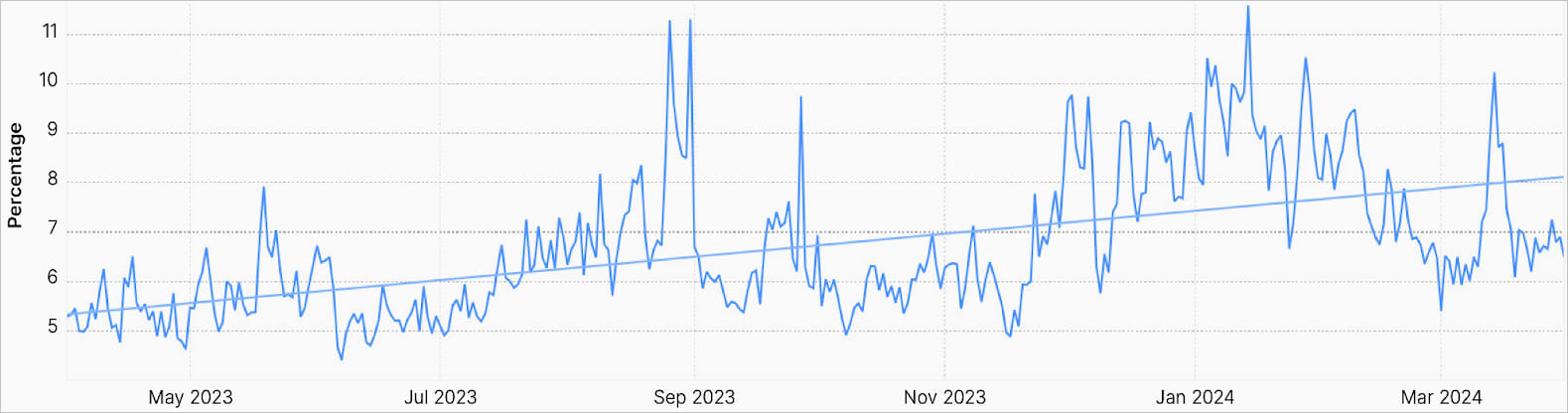
Supply: Cloudflare
It is a notable enhance in comparison with the 6% recorded over the earlier 12-month interval (2022-2023), displaying a rise within the total quantity of DDoS assaults.
Cloudflare says that in giant international assault occasions, malicious site visitors could account for as a lot as 12% of all HTTP site visitors.
“Specializing in HTTP requests solely, in Q1 2024 Cloudflare blocked a mean of 209 billion cyber threats every day (+86.6% YoY) […which] is a considerable enhance in relative phrases in comparison with the identical time final yr,” says Cloudflare.
The agency’s PDF report, out there for obtain right here, offers further suggestions for defenders and deeper insights into the compiled stats.





