Menace actors are leveraging the ‘Citrix Bleed’ vulnerability, tracked as CVE-2023-4966, to focus on authorities, technical, and authorized organizations within the Americas, Europe, Africa, and the Asia-Pacific area.
Researchers from Mandiant report that 4 ongoing campaigns goal susceptible Citrix NetScaler ADC and Gateway home equipment, with assaults underway since late August 2023.
The security firm has seen post-exploitation exercise associated to credential theft and lateral motion, warning that exploitation leaves behind restricted forensic proof, making these assaults significantly stealthy.
Citrix Bleed
The Citrix Bleed CVE-2023-4966 vulnerability was disclosed on October 10 as a vital severity flaw impacting Citrix NetScaler ADC and NetScaler Gateway, permitting entry to delicate info on the gadgets.
Every week after a repair was made out there, Mandiant revealed the flaw was a zero-day underneath energetic exploitation since late August, with hackers leveraging it to hijack current authenticated classes and bypass multifactor safety.
Attackers used specifically crafted HTTP GET requests to power the equipment to return system reminiscence contents, which embody a legitimate Netscaler AAA session cookie issued post-authentication and after MFA checks.
Hackers who steal these authentication cookies can then entry the system with out performing an MFA verification once more.
Citrix adopted up with a second warning to admins, urging them to safe their methods in opposition to the continued assaults, which have been low-complexity and did not require any person interplay.
On October 25, AssetNote researchers launched a proof-of-concept (PoC) exploit demonstrating how one can hijack a NetScaler account by way of session token theft.
Ongoing assaults
Mandiant explains that the shortage of logging on the home equipment makes investigating the exploitation of CVE-2023-3966 difficult, requiring net utility firewalls (WAF) and different community site visitors monitoring home equipment to log site visitors and decide if a tool was exploited.
Until a community makes use of this kind of monitoring earlier than an assault, it prevents any historic evaluation and limits researchers to real-time observations.
Even post-exploitation, the attackers stay stealthy, using living-off-the-land strategies and customary administrative instruments like internet.exe and netscan.exe to mix with each day operations.
Mandiant was capable of establish exploitation makes an attempt and session hijacking by way of one of many following pathways:
- WAF request evaluation: Requests to the susceptible endpoint could be logged by WAF instruments.
- Login patterns monitoring: Consumer and supply IP handle mismatches and a number of classes from the identical IP handle written in ns.log information are indicators of potential unauthorized entry.
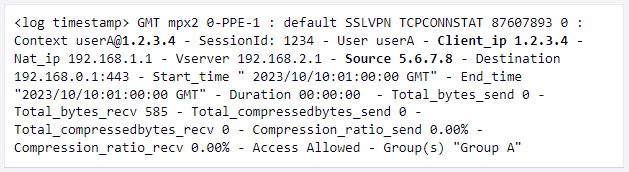
- Home windows Registry correlation: Correlating Home windows Registry entries on Citrix VDA methods with ns.log information makes it doable to hint the attacker’s origin.
- Reminiscence dump inspection: NSPPE course of reminiscence core dump information could be analyzed for unusually lengthy strings containing repetitive characters, which can point out exploitation makes an attempt.
Attack targets
After exploiting CVE-2023-4966, the attackers engaged in community reconnaissance, stealing account credentials and transferring laterally by way of RDP.
The instruments the risk actors use at this part are the next:
- internet.exe – Energetic Listing (AD) reconnaissance
- netscan.exe – inside community enumeration.
- 7-zip – create an encrypted segmented archive for compressing reconnaissance information
- certutil – encode (base64) and decode information information and deploy backdoors
- e.exe and d.dll – load into the LSASS course of reminiscence and create reminiscence dump information
- sh3.exe – run the Mimikatz LSADUMP command for credential extraction
- FREEFIRE – novel light-weight .NET backdoor utilizing Slack for command and management
- Atera – Distant monitoring and administration
- AnyDesk – Distant desktop
- SplashTop – Distant desktop
Though lots of the above are generally present in enterprise environments, their mixed deployment could also be an indication of compromise, and instruments like FREEFIRE are clear indications of a breach.
The researchers have launched a Yara rule that can be utilized to detect FREE FIRE on a tool.
Mandiant says the 4 risk actors that exploit CVE-2023-4966 in varied campaigns present some overlap within the post-exploitation stage.
All 4 extensively used csvde.exe, certutil.exe, native.exe, and nbtscan.exe, whereas two exercise clusters have been seen utilizing Mimikatz.
Making use of the out there security updates doesn’t handle current breaches, and thus, a full incident response is required.
For recommendation on system restoration, take a look at Mandiant’s remediation information.




