Human rights activists in Morocco and the Western Sahara area are the targets of a brand new menace actor that leverages phishing assaults to trick victims into putting in bogus Android apps and serve credential harvesting pages for Home windows customers.
Cisco Talos is monitoring the exercise cluster below the identify Starry Addax, describing it as primarily singling out activists related to the Sahrawi Arab Democratic Republic (SADR).
Starry Addax’s infrastructure – ondroid[.]web site and ondroid[.]retailer – is designed to focus on each Android and Home windows customers, with the latter involving faux web sites masquerading as login pages for in style social media web sites.

The adversary, believed to be lively since January 2024, is understood to ship spear-phishing emails to targets, urging recipients to put in Sahara Press Service’s cellular app or a related decoy associated to the area.
Relying on the working system from the place the request is originating from, the goal is both served a malicious APK that impersonates the Sahara Press Service or redirected to a social media login web page to reap their credentials.
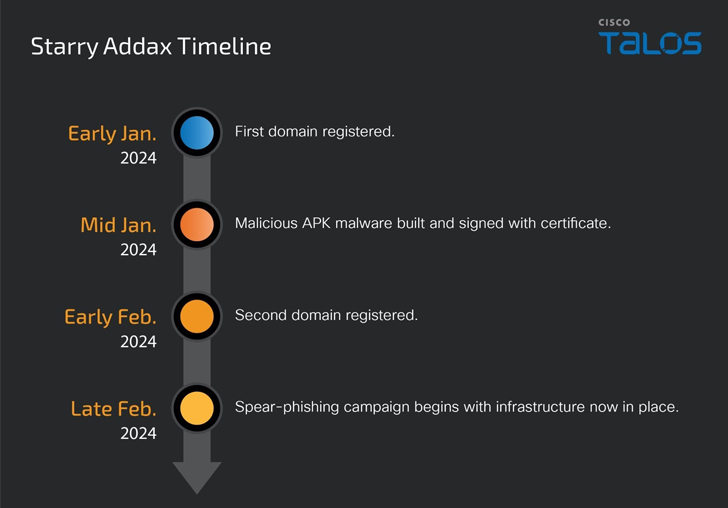
The novel Android malware, dubbed FlexStarling, is flexible and outfitted to ship further malware elements and steal delicate info from contaminated gadgets.
As soon as put in, it requests the sufferer to grant it intensive permissions that enable the malware to carry out nefarious actions, together with fetching instructions to be executed from a Firebase-based command-and-control (C2), an indication that the menace actor is trying to fly below the radar.
“Campaigns like this that concentrate on high-value people normally intend to sit down quietly on the gadget for an prolonged interval,” Talos stated.

“All elements from the malware to the working infrastructure appear to be bespoke/custom-made for this particular marketing campaign indicating a heavy concentrate on stealth and conducting actions below the radar.”
The event comes amid the emergence of a brand new business Android distant entry trojan (RAT) referred to as Oxycorat that is being supplied on the market with various info gathering capabilities.




