Hackers are launching assaults towards Palo Alto Networks PAN-OS firewalls by exploiting a not too long ago mounted vulnerability (CVE-2025-0108) that permits bypassing authentication.
The security subject obtained a high-severity rating and impacts the PAN-OS administration internet interface and permits an unauthenticated attacker on the community to bypass authentication and invoke sure PHP scripts, doubtlessly compromising integrity and confidentiality.
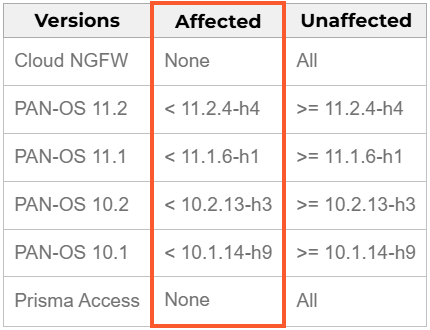
In a security bulletin on February 12, Palo Alto Networks urges admins to improve firewalls to the variations beneath to handle the problem:
- 11.2.4-h4 or later
- 11.1.6-h1 or later
- 10.2.13-h3 or later
- 10.1.14-h9 or later
PAN-OS 11.0 can be impacted however the product reached the tip of life (EoL) and Palo Alto Networks doesn’t plan to launch any fixes for it. Due to this, customers are strongly beneficial to improve to a supported launch as a substitute.
Supply: Palo Alto Networks
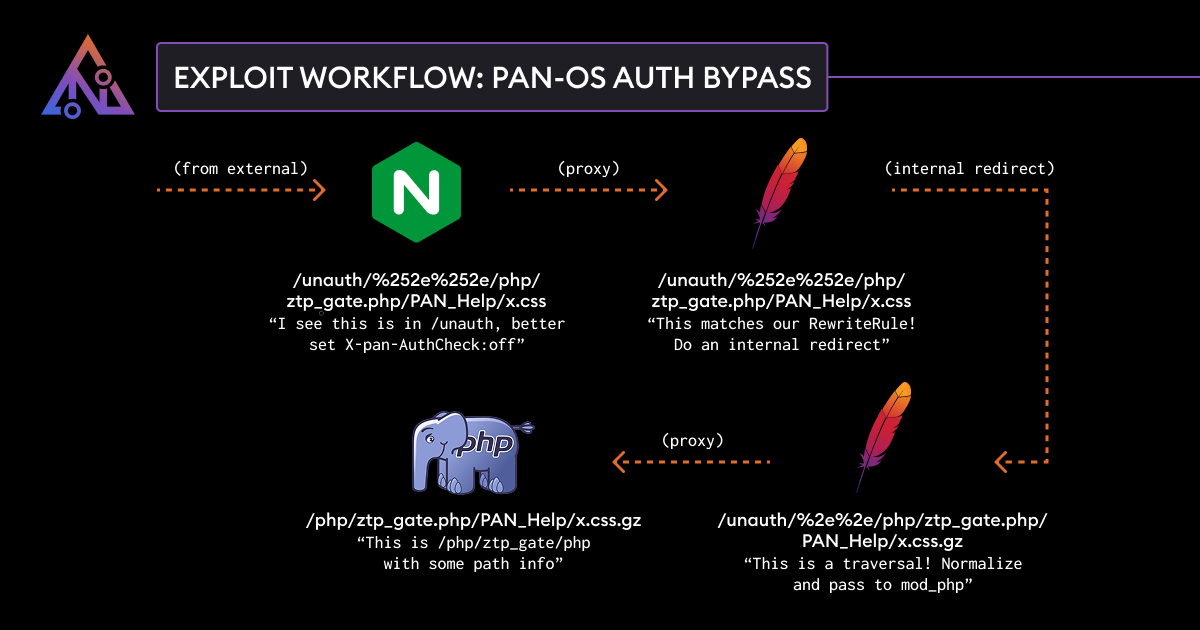
The vulnerability was found and reported to Palo Alto Networks by security researchers at Assetnote. In addition they revealed a write-up with full exploitation particulars when the patch was launched.
The researchers demonstrated how the flaw may very well be leveraged to extract delicate system information, retrieve firewall configurations, or doubtlessly manipulate sure settings inside PAN-OS.
The exploit leverages a path confusion between Nginx and Apache in PAN-OS that permits bypassing authentication.
Attackers with community entry to the administration interface can leverage this to assemble intelligence for additional assaults or to weaken security defenses by modifying accessible settings.
Supply: Assetnote
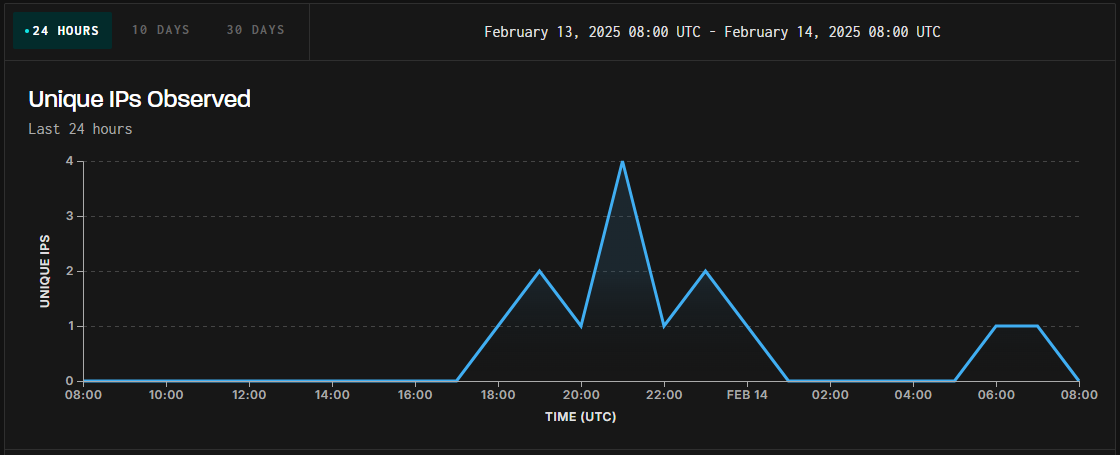
Menace monitoring platform GreyNoise logged exploitation makes an attempt focusing on unpatched PAN-OS firewalls.
The assaults began on February 13, at 17:00 UTC, and seem to originate from a number of IP addresses, doubtlessly indicating exploitation efforts from distinct risk actors.
Supply: GreyNoise
Concerning the publicity of weak gadgets on-line, Macnica researcher Yutaka Sejiyama instructed BleepingComputer that there are at the moment over 4,400 PAN-OS gadgets exposing their administration interface on-line.
To defend towards the continued exploitation exercise, which, contemplating that the PoC is public, may be very prone to culminate within the following days, it is suggested to use the obtainable patches and limit entry to firewall administration interfaces.
Replace 2/18 – Palo Alto Networks despatched BleepingComputer the beneath remark concerning the exercise noticed within the wild.
“The security of our clients is our high precedence. Palo Alto Networks has confirmed stories of lively exploitation focusing on a vulnerability (CVE-2025-0108) within the PAN-OS internet administration interface. This vulnerability, chained with different vulnerabilities like CVE-2024-9474, may permit unauthorized entry to unpatched and unsecured firewalls.
We’re urging all clients with internet-facing PAN-OS administration interfaces to right away apply the security updates launched on February 12, 2025. Securing external-facing administration interfaces is a elementary security finest apply, and we strongly encourage all organizations to overview their configurations to attenuate threat.
Detailed data and mitigation steering can be found within the CVE-2025-0108 security advisory: https://security.paloaltonetworks.com/CVE-2025-0108″




