The U.S. Cybersecurity and Infrastructure Safety Company (CISA) is warning about hackers actively exploiting a essential vulnerability in Adobe ColdFusion recognized as CVE-2023-26360 to achieve preliminary entry to authorities servers.
The security challenge permits executing arbitrary code on servers working Adobe ColdFusion 2018 Replace 15 and older, and 2021 Replace 5 and earlier. It was exploited as a zero day earlier than Adobe mounted it in mid-March by releasing ColdFusion 2018 Replace 16 and 2021 Replace 6.
On the time, CISA revealed a discover about menace actors exploiting the flaw and urged federal organizations and state providers to use the out there security updates.
In an alert at the moment, America’s Cyber Protection Company warns that CVE-2023-26360 continues to be leveraged in assaults, showcasing incidents from June that impacted two federal company programs.
“In each incidents, Microsoft Defender for Endpoint (MDE) alerted of the potential exploitation of an Adobe ColdFusion vulnerability on public-facing internet servers within the company’s pre-production atmosphere” – CISA
The company notes that “each servers had been working outdated variations of software program that are weak to numerous CVEs.”
CISA says that the menace actors leveraged the vulnerability to drop malware utilizing HTTP POST instructions to the listing path related to ColdFusion.
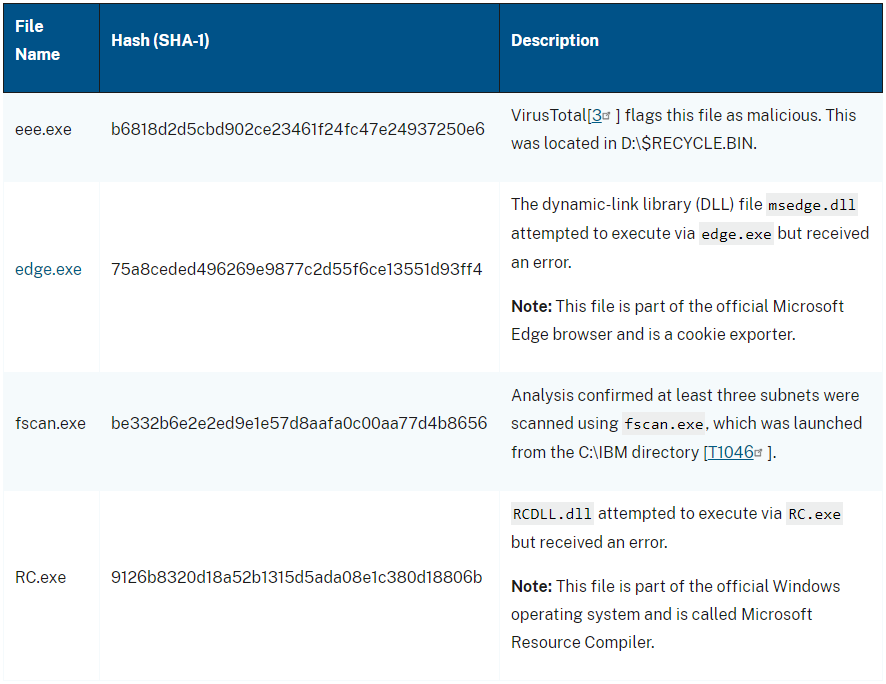
The primary incident was recorded on June 26 and relied on the essential vulnerability to breach a server working Adobe ColdFusion v2016.0.0.3.
The attackers carried out course of enumeration together with community checks and put in an online shell (config.jsp) that allowed them to insert code right into a ColdFusion configuration file and extract credentials.
Their actions included deleting recordsdata used within the assault to cover their presence and creating recordsdata within the C:IBM listing to facilitate malicious operations undetected.
The second incident occurred on June 2 when the hackers exploited CVE-2023-26360 on a server working Adobe ColdFusion v2021.0.0.2.
On this case, the attackers gathered person account data earlier than dropping a textual content file that decoded as a distant entry trojan (d.jsp).
Subsequent, they tried to exfiltrate Registry recordsdata and security account supervisor (SAM) data. The attackers abused out there security instruments to entry SYSVOL, a particular listing current on each area controller in a site.
In each circumstances, the assaults had been detected and blocked earlier than the intruders had been capable of exfiltrate information or transfer laterally, and the compromised belongings had been faraway from essential networks inside 24 hours.
CISA’s evaluation categorizes the assaults as reconnaissance efforts. Nonetheless, it’s unknown if the identical menace actor is behind each intrusions.
To mitigate the danger, CISA recommends upgrading ColdFusion to the most recent out there model, making use of community segmentation, organising a firewall or WAF, and imposing signed software program execution insurance policies.




