Safety researchers are observing exploitation makes an attempt for the CVE-2023-22527 distant code execution flaw vulnerability that impacts outdated variations of Atlassian Confluence servers.
Atlassian disclosed the security problem final week and famous that it impacts solely Confluence variations launched earlier than December 5, 2023, together with some out-of-support releases.
The flaw has a important severity rating and is described as a template injection weak point that permits unauthenticated distant attackers to execute code on weak Confluence Data Middle and Confluence Server endpoints, variations variations 8.0.x, 8.1.x, 8.2.x, 8.3.x, 8.4.x, and eight.5.0 by means of 8.5.3.
A repair is obtainable for Confluence Data Middle and Server variations 8.5.4 (LTS), 8.6.0 (Data Middle solely), and eight.7.1 (Data Middle solely), and later variations.
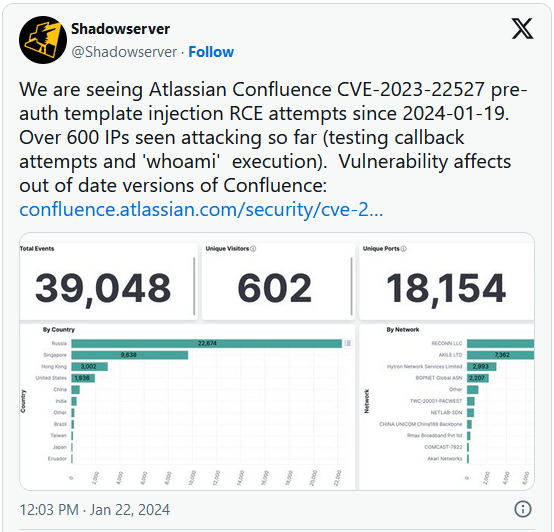
Menace monitoring service Shadowserver studies immediately that its methods recorded hundreds of makes an attempt to use CVE-2023-22527, the assaults originating from slightly over 600 distinctive IP addresses.
The service says that attackers are attempting out callbacks by executing the ‘whoami‘ command to collect details about the extent of entry and privileges on the system.
The full variety of exploitation makes an attempt logged by The Shadowserver Basis is above 39,000, many of the assaults coming from Russian IP addresses.
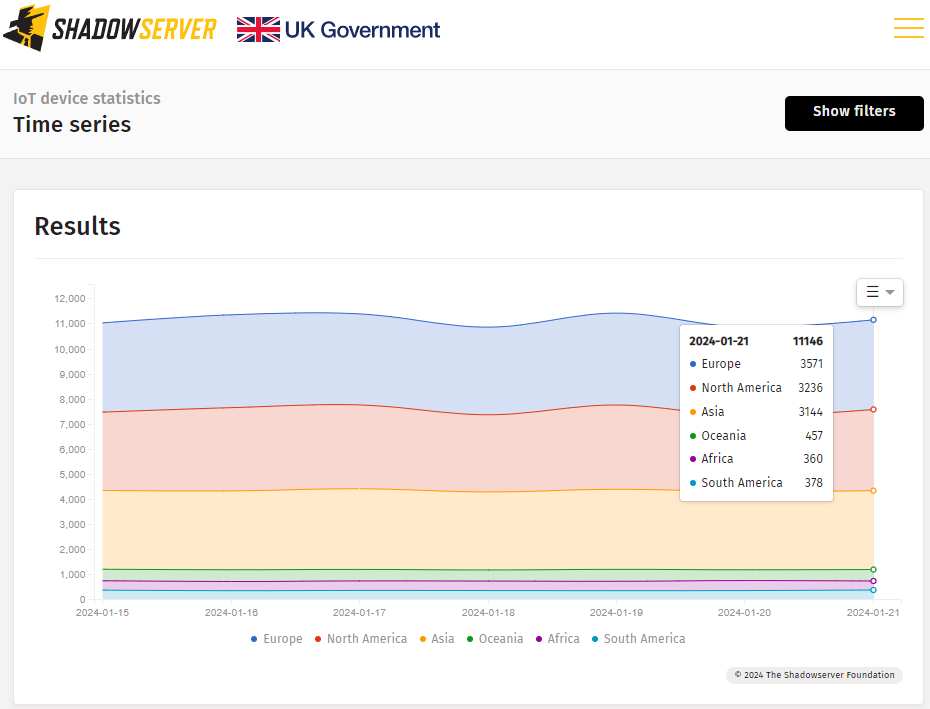
Shadowserver studies that its scanners at present detect 11,100 Atlassian Confluence cases accessible over the general public web. Nonetheless, not all of these essentially run a weak model.
Atlassian Confluence vulnerabilities are belongings ceaselessly exploited by varied varieties of attackers, together with refined state-sponsored risk actors and opportunistic ransomware teams.
Concerning CVE-2023-22527, Atlassian has beforehand stated it was unable to supply particular indicators of compromise (IoCs) that will help in detecting instances of exploitation.
Confluence server directors ought to make it possible for the endpoints they handle have been up to date a minimum of to a model launched after December 5, 2023.
For organizations with outdated Confluence cases, the recommendation is to deal with them as probably compromised, search for indicators of exploitation, carry out an intensive cleanup, and replace to a secure model.